CopySense® Appliance Case Study
... “We appreciate the ability to leverage the ‘teachable moment’ so we can educate our students about the legal use of the Internet. After reading our messages, they understand why their network access is being blocked and how to move forward to unblock it. As an academic institution, it makes perfect ...
... “We appreciate the ability to leverage the ‘teachable moment’ so we can educate our students about the legal use of the Internet. After reading our messages, they understand why their network access is being blocked and how to move forward to unblock it. As an academic institution, it makes perfect ...
LiveAction Case Study-Multinational Shipping Company-v1
... schedule—gain insights from our special presenters about topics like QoS, Hybrid WAN http://hubs.ly/H05CQNX0 Management, Capacity Planning and more. Additional Resources Case studies, white papers, eBooks and more are available for your learning on the LiveAction resources page. http://hubs.ly/H05Cz ...
... schedule—gain insights from our special presenters about topics like QoS, Hybrid WAN http://hubs.ly/H05CQNX0 Management, Capacity Planning and more. Additional Resources Case studies, white papers, eBooks and more are available for your learning on the LiveAction resources page. http://hubs.ly/H05Cz ...
ORCA BTX-8 and BTX-21 - Nuera Communications Inc
... and BTX-21 allows SS7 networks to control subscriber calls. To support E911 calls and Operator Services, each BTX-8 and BTX-21 voice port supports MF tone generation and detection. To support quality of service over the cable HFC plant, the BTX-8 and BTX-21 interoperate with leading softswitches to ...
... and BTX-21 allows SS7 networks to control subscriber calls. To support E911 calls and Operator Services, each BTX-8 and BTX-21 voice port supports MF tone generation and detection. To support quality of service over the cable HFC plant, the BTX-8 and BTX-21 interoperate with leading softswitches to ...
ACCESS CONTROL OPTIONS FOR WIRED NETWORKS
... profiling efforts have been solely focused on wireless access. This has led to wired access controls being overshadowed or not configured at all, leading to security gaps in many organizations. And as IT Security experts are well aware, networks are only as strong as their weakest link. As the moder ...
... profiling efforts have been solely focused on wireless access. This has led to wired access controls being overshadowed or not configured at all, leading to security gaps in many organizations. And as IT Security experts are well aware, networks are only as strong as their weakest link. As the moder ...
download
... • No single mechanism that will support all functions required • One particular element underlies many of the security mechanisms in use: cryptographic techniques ...
... • No single mechanism that will support all functions required • One particular element underlies many of the security mechanisms in use: cryptographic techniques ...
Overview of Operating Systems Security Features
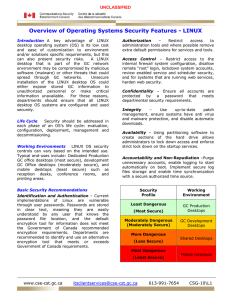
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
IP Convergence
... within a common switched network platform You only needed a single protocol, a single carriage architecture and a single OSS (and a single operator!) to drive the entire network operation ...
... within a common switched network platform You only needed a single protocol, a single carriage architecture and a single OSS (and a single operator!) to drive the entire network operation ...
Security Devices and Practices
... In general, authorization can be handled by: – Authorization for each authenticated user, in which the system performs an authentication process to verify the specific entity and then grants access to resources for only that entity – Authorization for members of a group, in which the system matches ...
... In general, authorization can be handled by: – Authorization for each authenticated user, in which the system performs an authentication process to verify the specific entity and then grants access to resources for only that entity – Authorization for members of a group, in which the system matches ...
Complex Networks
... Can we capture these policies? • Domains do not disclose their connectivity ...
... Can we capture these policies? • Domains do not disclose their connectivity ...
PDF
... causes of frequent collisions.) At Level-3, we can not only passively detect problems such as loss of connectivity using SNMP, but can actively probe the network in two ways. The first approach involves proactively testing paths in the network for routing loops and black holes with IP loose source r ...
... causes of frequent collisions.) At Level-3, we can not only passively detect problems such as loss of connectivity using SNMP, but can actively probe the network in two ways. The first approach involves proactively testing paths in the network for routing loops and black holes with IP loose source r ...
Enterprise Network Analyzer and OmniEngine Console
... OmniPeek Enterprise offers an intuitive, easy-to-use graphical interface that engineers can use to rapidly analyze and troubleshoot enterprise networks. OmniPeek Enterprise provides centralized Expert analysis for all networks under management. Using OmniPeek’s intuitive user interface and “top-down ...
... OmniPeek Enterprise offers an intuitive, easy-to-use graphical interface that engineers can use to rapidly analyze and troubleshoot enterprise networks. OmniPeek Enterprise provides centralized Expert analysis for all networks under management. Using OmniPeek’s intuitive user interface and “top-down ...
IT Security Policy
... DISTRICTS shall maintain a network configuration management program which includes as a minimum: a network diagram identifying all connections, addresses, and purpose of each connection including management approval of all high risk internetfacing ports such as mail (SMTP/25), file transport protoco ...
... DISTRICTS shall maintain a network configuration management program which includes as a minimum: a network diagram identifying all connections, addresses, and purpose of each connection including management approval of all high risk internetfacing ports such as mail (SMTP/25), file transport protoco ...
Small Business Networking
... because of the different functions it can perform. The server can back up information, saving time and preventing data loss as well as providing security for information. A server acts as the single centralized unit for the whole of the network, so Internet connectivity can be easily monitored and c ...
... because of the different functions it can perform. The server can back up information, saving time and preventing data loss as well as providing security for information. A server acts as the single centralized unit for the whole of the network, so Internet connectivity can be easily monitored and c ...
Lecture X ISA & IPSecurity
... manual reconfiguration of secret keys and helps protect against secret key determination. Secure links end to end—IPSec for Windows Server provides secure links end-to-end for private network users within the same domain or across any trusted domain in the enterprise. Centralized management—Network ...
... manual reconfiguration of secret keys and helps protect against secret key determination. Secure links end to end—IPSec for Windows Server provides secure links end-to-end for private network users within the same domain or across any trusted domain in the enterprise. Centralized management—Network ...
Wireless, Voice, Desktop Video, and BYOD Implications for
... 4.Network service rates will continue to decline to partially offset growth in demand, based on cost improvements in hardware/software components as well as bandwidth. ...
... 4.Network service rates will continue to decline to partially offset growth in demand, based on cost improvements in hardware/software components as well as bandwidth. ...
Communications and Data Flow Within the FHWA VII Network
... signal phase and timing information to passing vehicles in support of safety applications. – Interface with roadside sensors to forward information to network user or to distribute advisory messages to passing vehicles. – Interface with roadside transaction processing systems. ...
... signal phase and timing information to passing vehicles in support of safety applications. – Interface with roadside sensors to forward information to network user or to distribute advisory messages to passing vehicles. – Interface with roadside transaction processing systems. ...
Computer Security Presentation
... September [2004], a 600% increase over the 250 spotted a year ago. Of those, 45% were Trojan horses attempting to steal personal data, the company said. The company also reported a “surge in zombie networks,” saying it had found 400 programs in the past month compared with 17 a year ago. ...
... September [2004], a 600% increase over the 250 spotted a year ago. Of those, 45% were Trojan horses attempting to steal personal data, the company said. The company also reported a “surge in zombie networks,” saying it had found 400 programs in the past month compared with 17 a year ago. ...
Interceptor™ Optical Network Security System Design Guide
... Uncontrolled access areas (UCAs) are any areas where there are no physical access controls, allowing free and unrestricted access to the immediate population or to the general public. A PDS is always required for any unencrypted classified network deployments in or through a UCA. Frequently, an orga ...
... Uncontrolled access areas (UCAs) are any areas where there are no physical access controls, allowing free and unrestricted access to the immediate population or to the general public. A PDS is always required for any unencrypted classified network deployments in or through a UCA. Frequently, an orga ...
Are Clouds Secure? - San Francisco Bay Area ISSA Chapter
... What We’re Not Going to Discuss • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
... What We’re Not Going to Discuss • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
Are Clouds Secure?
... What We’re Not Going to Discuss • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
... What We’re Not Going to Discuss • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
Networking and communication
... User data is sent from the application layer to the transport layer The OS adds a TCP header that identify the source and destination ports, forming a TCP segment, and sends that to the network layer In the network layer, an IP header identifying the source and destination systems are added, w ...
... User data is sent from the application layer to the transport layer The OS adds a TCP header that identify the source and destination ports, forming a TCP segment, and sends that to the network layer In the network layer, an IP header identifying the source and destination systems are added, w ...
Home Network Basics
... – Media Access Control address – Unique address for each item on a network • Can be found in System Information under Network Adapter ...
... – Media Access Control address – Unique address for each item on a network • Can be found in System Information under Network Adapter ...
Network
... desired data safely, easily, quickly, and accurately, regardless of their location. In the context, “data” is not limited to specific data types like audio or video content, but describes all information accessible on a network. 1) Data access: be designed and implemented for optimal and efficient h ...
... desired data safely, easily, quickly, and accurately, regardless of their location. In the context, “data” is not limited to specific data types like audio or video content, but describes all information accessible on a network. 1) Data access: be designed and implemented for optimal and efficient h ...
PCI Compliance - Aug 2009 - Commonwealth Business Travel
... property, gas station, supermarket, or other point of sale location). Internet protocol (IP) -based POS environment is one in which transactions are stored, processed, or transmitted on IP-based systems, or systems communicating via TCP/IP. ...
... property, gas station, supermarket, or other point of sale location). Internet protocol (IP) -based POS environment is one in which transactions are stored, processed, or transmitted on IP-based systems, or systems communicating via TCP/IP. ...