BDC5eChapter19
... • Standard defines information structure and allowable data types (SMI) • At least one system must be responsible for network management; others act as agents • Information exchanged using simple request/respond protocol, usually running over UDP Business Data Communications, 5e ...
... • Standard defines information structure and allowable data types (SMI) • At least one system must be responsible for network management; others act as agents • Information exchanged using simple request/respond protocol, usually running over UDP Business Data Communications, 5e ...
Proposal to Intel for research support
... Discovering topology: Network topology refers not only to the physical layout of components and cables, but also the logical partitioning of the network into administrative domains, routing areas, and other virtual views. We have come up with three novel technologies to discover, store, and display ...
... Discovering topology: Network topology refers not only to the physical layout of components and cables, but also the logical partitioning of the network into administrative domains, routing areas, and other virtual views. We have come up with three novel technologies to discover, store, and display ...
Networks - WSD Blogs
... A device that sends and receives data to and from computers over telephone lines. ...
... A device that sends and receives data to and from computers over telephone lines. ...
Cybrotech software tools
... Network adapter is selected automatically. Periodic reading is triggered on round interval, not related to when logger is actually started. For example, if logger is started at 7:45, first hourly event will be triggered at 8:00, second at 9:00 and so on. When logger is open, and Autorun is set, read ...
... Network adapter is selected automatically. Periodic reading is triggered on round interval, not related to when logger is actually started. For example, if logger is started at 7:45, first hourly event will be triggered at 8:00, second at 9:00 and so on. When logger is open, and Autorun is set, read ...
Computer Networks and the Internet
... Most LANs connect workstations and personal computers. Each node (individual computer ) in a LAN has its own CPU with which it executes programs, but it also is able to access data and devices anywhere on the LAN. This means that many users can share expensive devices, such as laser printers, as w ...
... Most LANs connect workstations and personal computers. Each node (individual computer ) in a LAN has its own CPU with which it executes programs, but it also is able to access data and devices anywhere on the LAN. This means that many users can share expensive devices, such as laser printers, as w ...
DISTRIBUTED ALGORITHMS
... • distributed mutual exclusion: needed to regulate accesses to a common resource that can be used only by one process at a time ...
... • distributed mutual exclusion: needed to regulate accesses to a common resource that can be used only by one process at a time ...
Kerio WinRoute Firewall Features Summary and Simple Setup
... specify the installation directory, which should contain sufficient storage space (minimum of 10 MB, recommended 3 GB for logs and cache file). Other parameters include the administrator account (which will be used to log into the firewall) and the option to import settings from WinRoute Pro (if app ...
... specify the installation directory, which should contain sufficient storage space (minimum of 10 MB, recommended 3 GB for logs and cache file). Other parameters include the administrator account (which will be used to log into the firewall) and the option to import settings from WinRoute Pro (if app ...
Management Information Systems
... The physical fully connected topology is generally too costly and complex for practical networks, although the topology is used when there are only a small number of nodes to be interconnected ...
... The physical fully connected topology is generally too costly and complex for practical networks, although the topology is used when there are only a small number of nodes to be interconnected ...
Survey of online attacks on E-Commerce sites
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
IDS
... – Even DPI gives limited application-level semantic information – Record and process huge amount of traffic – May be easily defeated by encryption, but can be mitigated with encryption only at the gateway/proxy ...
... – Even DPI gives limited application-level semantic information – Record and process huge amount of traffic – May be easily defeated by encryption, but can be mitigated with encryption only at the gateway/proxy ...
No Slide Title
... • iBGP when used as IGP • carries global routes around network • injected with eircom customer routes ...
... • iBGP when used as IGP • carries global routes around network • injected with eircom customer routes ...
cs739-intro - Computer Sciences User Pages
... Goals of Course Learn about challenges and existing techniques for building distributed systems and services • Read and discuss influential papers from SOSP, OSDI, NSDI ...
... Goals of Course Learn about challenges and existing techniques for building distributed systems and services • Read and discuss influential papers from SOSP, OSDI, NSDI ...
Elements of a Small PC Network
... Elements of a Small PC Network • Ethernet Hubs Can Create Latency – Only one station may transmit at a time or the signals will collide and be ...
... Elements of a Small PC Network • Ethernet Hubs Can Create Latency – Only one station may transmit at a time or the signals will collide and be ...
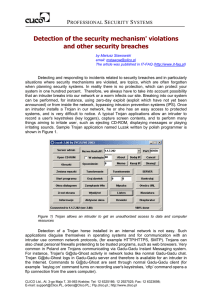
Detection of the security mechanism` violations and other
... log requires that a vendor of a security solution delivers relevant tools. The tools for viewing and sorting logs can help very little for this purpose. On the other hand, generating reports from historical logs usually takes long time, especially when an IPS/IDS system does not have its own databas ...
... log requires that a vendor of a security solution delivers relevant tools. The tools for viewing and sorting logs can help very little for this purpose. On the other hand, generating reports from historical logs usually takes long time, especially when an IPS/IDS system does not have its own databas ...
Agent-Based Decision Support Systems for the
... Each Task is meant to follow an interaction protocol to deal with a specific type of event. Based on the results returned by the tasks, an agent may choose to invoke another Task or may conclude that no further investigation is required. Conversations are instantiations of interaction protocols, bui ...
... Each Task is meant to follow an interaction protocol to deal with a specific type of event. Based on the results returned by the tasks, an agent may choose to invoke another Task or may conclude that no further investigation is required. Conversations are instantiations of interaction protocols, bui ...
WiFi Security: Keeping Your Information Private and Safe
... network to steal information from anyone who connects to it. This is often referred to as a honey pot. Example: A pineapple scans and copies legitimate access points. Once this is complete the cyber criminal can use the device and transmit copied WIFI networks. A user then connects to what appears t ...
... network to steal information from anyone who connects to it. This is often referred to as a honey pot. Example: A pineapple scans and copies legitimate access points. Once this is complete the cyber criminal can use the device and transmit copied WIFI networks. A user then connects to what appears t ...
High-Performance Data Transfer for Hybrid Optical
... Accepted authentication handler can be set on a per host/per subnet basis ...
... Accepted authentication handler can be set on a per host/per subnet basis ...
Network controller - Duke Computer Science
... Current Cloud Offerings • Limited control of the network – Requires integration of third-party solutions – Limits the opportunity to migrate production applications introduction of cloud networking functions ...
... Current Cloud Offerings • Limited control of the network – Requires integration of third-party solutions – Limits the opportunity to migrate production applications introduction of cloud networking functions ...
Chapter Answers to end-of
... 2. Explain the difference between peer-to-peer and client/server networks. In a peer-to-peer network, all the computers on the network are equals, and there is no file server. Each computer user decides which, if any, files will be accessible to other users on the network. Although peer-topeer netwo ...
... 2. Explain the difference between peer-to-peer and client/server networks. In a peer-to-peer network, all the computers on the network are equals, and there is no file server. Each computer user decides which, if any, files will be accessible to other users on the network. Although peer-topeer netwo ...
Chan
... array to the intended receiver of a free space optical communications link while limiting the power transmitted to a broadly defined region within the main lobe Results we can suppress by >10 dB the power to a defined suppression region 0.2 beam widths away from the user without requiring a signific ...
... array to the intended receiver of a free space optical communications link while limiting the power transmitted to a broadly defined region within the main lobe Results we can suppress by >10 dB the power to a defined suppression region 0.2 beam widths away from the user without requiring a signific ...
lect2_3
... Revising Important Topics 7. Besides “connecting” before transmitting, what other functions are built in the TCP protocol? 8. Why will a phone conversation not benefit from congestion control? 9. What transport protocol is most suitable for IP telephony? 10. What is the difference between circuit s ...
... Revising Important Topics 7. Besides “connecting” before transmitting, what other functions are built in the TCP protocol? 8. Why will a phone conversation not benefit from congestion control? 9. What transport protocol is most suitable for IP telephony? 10. What is the difference between circuit s ...
best practices - Palo Alto Networks
... is no guarantee that a given set of ports will always define an application, which is why security policies should be applied to traffic associated with applications, instead of just ports. Palo Alto Networks has identified hundreds of applications used to slyly deliver threats into victim organizat ...
... is no guarantee that a given set of ports will always define an application, which is why security policies should be applied to traffic associated with applications, instead of just ports. Palo Alto Networks has identified hundreds of applications used to slyly deliver threats into victim organizat ...
U2Net: Boosting ultra-broadband TextStart By Zhang Kejing U2Net
... U2Net represents the way towards ubiquitous ultra-broadband network infrastructure, as well as IP video and cloud services. Recent developments in cloud applications and OTT services have had a big impact on the telecom industry; Internet services are booming. As of 2011, fixed broadband users in No ...
... U2Net represents the way towards ubiquitous ultra-broadband network infrastructure, as well as IP video and cloud services. Recent developments in cloud applications and OTT services have had a big impact on the telecom industry; Internet services are booming. As of 2011, fixed broadband users in No ...
Chapter 01
... logical layout of a network Many types of transmission media are available Modern networks use different layers of software to handle the different aspects of managing a network The OSI and Internet models are two important conceptual layered models of networking ...
... logical layout of a network Many types of transmission media are available Modern networks use different layers of software to handle the different aspects of managing a network The OSI and Internet models are two important conceptual layered models of networking ...