Physical Security
... left some security holes. – A form could submit itself via e-mail to an undisclosed recipient, either eavesdropping, spamming, or causing other problems. ...
... left some security holes. – A form could submit itself via e-mail to an undisclosed recipient, either eavesdropping, spamming, or causing other problems. ...
CH9
... The estimated cost, loss, or damage that can result if a threat exploits a vulnerability fraud Any business activity that uses deceitful practices or devices to deprive another of property or other rights malware (malicious software) A generic term for malicious software phishing A crimeware t ...
... The estimated cost, loss, or damage that can result if a threat exploits a vulnerability fraud Any business activity that uses deceitful practices or devices to deprive another of property or other rights malware (malicious software) A generic term for malicious software phishing A crimeware t ...
Malicious Threats - The University of Texas at Dallas
... risk of being fooled by a virus which targets that particular checksummer. Monitor/Behavior Blocker - a TSR that monitors programs while they are running for behavior which might denote a virus. TSR scanner - a TSR (memory-resident program) that checks for viruses while other programs are running. I ...
... risk of being fooled by a virus which targets that particular checksummer. Monitor/Behavior Blocker - a TSR that monitors programs while they are running for behavior which might denote a virus. TSR scanner - a TSR (memory-resident program) that checks for viruses while other programs are running. I ...
Malicious Threats - The University of Texas at Dallas
... risk of being fooled by a virus which targets that particular checksummer. Monitor/Behavior Blocker - a TSR that monitors programs while they are running for behavior which might denote a virus. TSR scanner - a TSR (memory-resident program) that checks for viruses while other programs are running. I ...
... risk of being fooled by a virus which targets that particular checksummer. Monitor/Behavior Blocker - a TSR that monitors programs while they are running for behavior which might denote a virus. TSR scanner - a TSR (memory-resident program) that checks for viruses while other programs are running. I ...
Application Security within Java 2, Standard Edition (J2SE)
... the Login method is called to login the user. Sounds simple, right? Well there is a little bit more that has to be done. When the LoginContext is created, a runtime login configuration file entry friendly name and a callback handler must be ...
... the Login method is called to login the user. Sounds simple, right? Well there is a little bit more that has to be done. When the LoginContext is created, a runtime login configuration file entry friendly name and a callback handler must be ...
PDF - IBM Redbooks
... media sites were used to both obtain information about users and as an initial access point into organizations. Attacks against mobile devices increased dramatically, in particular against mobile devices running the Android operating system. Although fixes were released to fix these mobile vulnerabi ...
... media sites were used to both obtain information about users and as an initial access point into organizations. Attacks against mobile devices increased dramatically, in particular against mobile devices running the Android operating system. Although fixes were released to fix these mobile vulnerabi ...
The Pros and Cons of Open Source Security
... any identifying information into a non-secure web page, the exit relay can detect and store login credentials or critical mission communications. To make matters worse, Tor uses the same circuit for all of each user’s connections. Therefore, once an exit node observes identifying information, it can ...
... any identifying information into a non-secure web page, the exit relay can detect and store login credentials or critical mission communications. To make matters worse, Tor uses the same circuit for all of each user’s connections. Therefore, once an exit node observes identifying information, it can ...
SOW
... methods of notification will be provided by WMATA. No price adjustments will be made for any delays resulting from an installation closing. When area radio stations, TV stations or WMATA’s website report that a facility has "delayed reporting" until a particular time, the Contractor's personnel have ...
... methods of notification will be provided by WMATA. No price adjustments will be made for any delays resulting from an installation closing. When area radio stations, TV stations or WMATA’s website report that a facility has "delayed reporting" until a particular time, the Contractor's personnel have ...
zombie. - People Search Directory
... • Today’s malware is all about stealth • Infected machines report back to attacker, its address, information…?? • Attacker uses backdoor to control the infected machine…. Make it a zombie. A collection of zombies is called a botnet Tanenbaum & Bo, Modern Operating Systems:4th ed., (c) 2013 Prentice- ...
... • Today’s malware is all about stealth • Infected machines report back to attacker, its address, information…?? • Attacker uses backdoor to control the infected machine…. Make it a zombie. A collection of zombies is called a botnet Tanenbaum & Bo, Modern Operating Systems:4th ed., (c) 2013 Prentice- ...
Cybersecurity for Asset Managers: Shielding Your Firm
... In light of the frequency and complexity of cyber risks, asset managers should operate on the assumption that breaches will occur. It’s unlikely that firms can prevent cyber menaces from infiltrating barriers all of the time. Attacks will crop up. What’s an asset manager to do? Develop a robust cybe ...
... In light of the frequency and complexity of cyber risks, asset managers should operate on the assumption that breaches will occur. It’s unlikely that firms can prevent cyber menaces from infiltrating barriers all of the time. Attacks will crop up. What’s an asset manager to do? Develop a robust cybe ...
Secure_Email_and_Web_Browsing_SEC
... ► Computer used for criminal purpose: ► Loss of confidential work ► Money extortion (private data encryption) ► Join BotNet to attack other systems on the Internet (DoS) ...
... ► Computer used for criminal purpose: ► Loss of confidential work ► Money extortion (private data encryption) ► Join BotNet to attack other systems on the Internet (DoS) ...
NEW YORK TECH-SECURITY CONFERENCE
... Session Six – Arbor Networks, Jeff Tidwell, Account Manager The Impact of DDoS Attacks Distributed Denial of Service (DDoS) attacks attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. They target a wide variety of important resources, from consumer-fa ...
... Session Six – Arbor Networks, Jeff Tidwell, Account Manager The Impact of DDoS Attacks Distributed Denial of Service (DDoS) attacks attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. They target a wide variety of important resources, from consumer-fa ...
Introduction
... How can risks be evaluated? How does a particular security solution mitigate risks? How can costs and tradeoffs of security solutions be balanced? How can secure software be designed, written, and tested? When and how can cryptography be used securely? How viruses and worms propagate and how can we ...
... How can risks be evaluated? How does a particular security solution mitigate risks? How can costs and tradeoffs of security solutions be balanced? How can secure software be designed, written, and tested? When and how can cryptography be used securely? How viruses and worms propagate and how can we ...
SG 17 is
... For on-going credibility, we need performance measures that provide some indication of the effectiveness of our standards. In the past there has been too much focus on quantity (i.e. how many standards are produced) than on the quality and effectiveness of the work. Going forward, we really need ...
... For on-going credibility, we need performance measures that provide some indication of the effectiveness of our standards. In the past there has been too much focus on quantity (i.e. how many standards are produced) than on the quality and effectiveness of the work. Going forward, we really need ...
McAfee Database Security Solution Brief
... breached involve a database. Annual research by the Computer Emergency Response Team (CERT) indicates that up to half of those breaches are caused by internal users. Why is this happening? Put simply, most companies have insufficient database protection. Three out of four organizations rely solely o ...
... breached involve a database. Annual research by the Computer Emergency Response Team (CERT) indicates that up to half of those breaches are caused by internal users. Why is this happening? Put simply, most companies have insufficient database protection. Three out of four organizations rely solely o ...
How to test an IPS
... 2. Attack detection and mitigation: systems must be vulnerable to recent attacks, then OS and application must be completely simulated. Tools like [xen] or its commercial equivalent [vmware] make possible to simulate different systems on one single physical server. 3. Denial of Service: in this last ...
... 2. Attack detection and mitigation: systems must be vulnerable to recent attacks, then OS and application must be completely simulated. Tools like [xen] or its commercial equivalent [vmware] make possible to simulate different systems on one single physical server. 3. Denial of Service: in this last ...
A Specialization Toolkit to Increase the Diversity of Operating Systems
... To support methodical specialization, we have been developing a toolkit that helps the kernel programmer in the tedious but important task of making specialized modules correct. For example, we have developed a specializer (called Tempo-C) [2, 1J for dynamic partial evaluation of C code, to simplify ...
... To support methodical specialization, we have been developing a toolkit that helps the kernel programmer in the tedious but important task of making specialized modules correct. For example, we have developed a specializer (called Tempo-C) [2, 1J for dynamic partial evaluation of C code, to simplify ...
Generic Template
... Emerging threats from IRC bots - IRC bots support automated scanning and exploitation of inadequately protected Windows systems, also offer DDoS capabilities. Massive pools of available zombies, e.g. IRC botnets with over 140,000 machines. [CERT Advisory CA-2003-08, March 2003] With so much capacity ...
... Emerging threats from IRC bots - IRC bots support automated scanning and exploitation of inadequately protected Windows systems, also offer DDoS capabilities. Massive pools of available zombies, e.g. IRC botnets with over 140,000 machines. [CERT Advisory CA-2003-08, March 2003] With so much capacity ...
- Learn Group
... Prof. Yousef B. Mahdy Prof. Yousef B. Mahdy -2014-2015, Assuit University, Egypt ...
... Prof. Yousef B. Mahdy Prof. Yousef B. Mahdy -2014-2015, Assuit University, Egypt ...
2015/16 Cyber Security Survey Results
... For those respondents which had provided periodic updates to Board members and executive management, the survey identified some shortcomings in coverage, with certain topics less commonly reported than expected. Specifically, cyber security incidents experienced (internal and external); the results ...
... For those respondents which had provided periodic updates to Board members and executive management, the survey identified some shortcomings in coverage, with certain topics less commonly reported than expected. Specifically, cyber security incidents experienced (internal and external); the results ...
EC2004_ch12
... Credit Card Attack (cont.) Brute force credit card attacks require minimal skill Hackers run thousands of small charges through merchant accounts, picking numbers at random When the perpetrator finds a valid credit card number it can then be sold on the black market Some modern-day black markets are ...
... Credit Card Attack (cont.) Brute force credit card attacks require minimal skill Hackers run thousands of small charges through merchant accounts, picking numbers at random When the perpetrator finds a valid credit card number it can then be sold on the black market Some modern-day black markets are ...
3_firewall_m
... • A firewall, is a “router, or several routers or access servers, designed as a buffer between any connected public networks and private network. ...
... • A firewall, is a “router, or several routers or access servers, designed as a buffer between any connected public networks and private network. ...
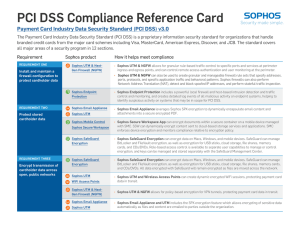
PCI DSS Compliance Reference Card
... ÌÌ Sophos UTM & NGFW can also be used to create granular and manageable firewall rule sets that specify addresses, ports, protocols, and specific application traffic and behavioral patterns. Sophos firewalls can also perform Network Address Translation (NAT), detect and block spoofed IP addresses, a ...
... ÌÌ Sophos UTM & NGFW can also be used to create granular and manageable firewall rule sets that specify addresses, ports, protocols, and specific application traffic and behavioral patterns. Sophos firewalls can also perform Network Address Translation (NAT), detect and block spoofed IP addresses, a ...
Extensions to the FTP Protocol
... The File Transfer Protocol provides a mechanism that allows a client to establish an FTP control connection and transfer a file between two FTP servers. This "Proxy FTP" mechanism can be used to decrease the amount of traffic on the network; the client instructs one server to transfer a file to anot ...
... The File Transfer Protocol provides a mechanism that allows a client to establish an FTP control connection and transfer a file between two FTP servers. This "Proxy FTP" mechanism can be used to decrease the amount of traffic on the network; the client instructs one server to transfer a file to anot ...
doc.gold.ac.uk
... • 2010: new Trojan horse-worm combination attack – Spread through a computer operating system ...
... • 2010: new Trojan horse-worm combination attack – Spread through a computer operating system ...