Paper
... Module 2 (WISM2). Cisco also has standalone wireless controllers that work in conjunction with the Cisco Catalyst switches. ...
... Module 2 (WISM2). Cisco also has standalone wireless controllers that work in conjunction with the Cisco Catalyst switches. ...
OWASP_Flyer_Sep06
... OWASP Validation Project - a project that provides guidance and tools related to validation. ...
... OWASP Validation Project - a project that provides guidance and tools related to validation. ...
CIS484-FIREWALL
... DMZ (Demilitarized Zone): An area outside the firewall that guards valuable information inside the firewall. Firewall: A computer firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It may b ...
... DMZ (Demilitarized Zone): An area outside the firewall that guards valuable information inside the firewall. Firewall: A computer firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It may b ...
Cisco Platform Exchange Grid (pxGrid) Overview At-A-Glance
... operation status, historical event information, operational telemetry, usage statistics, or any other information an IT platform has to share or needs to consume. • Ability to control what context is shared and with which platforms – Because pxGrid is customizable, partners can “publish” only the s ...
... operation status, historical event information, operational telemetry, usage statistics, or any other information an IT platform has to share or needs to consume. • Ability to control what context is shared and with which platforms – Because pxGrid is customizable, partners can “publish” only the s ...
Step 5: Securing Routing Protocols
... –A worm executes code and installs copies of itself in the infected computer, which can infect other hosts. •A worm installs itself by exploiting known vulnerabilities in systems, such as naive end users who open unverified executable attachments in e-mails ...
... –A worm executes code and installs copies of itself in the infected computer, which can infect other hosts. •A worm installs itself by exploiting known vulnerabilities in systems, such as naive end users who open unverified executable attachments in e-mails ...
Exploration CCNA4
... –A worm executes code and installs copies of itself in the infected computer, which can infect other hosts. •A worm installs itself by exploiting known vulnerabilities in systems, such as naive end users who open unverified executable attachments in e-mails ...
... –A worm executes code and installs copies of itself in the infected computer, which can infect other hosts. •A worm installs itself by exploiting known vulnerabilities in systems, such as naive end users who open unverified executable attachments in e-mails ...
ipSecMicrosof
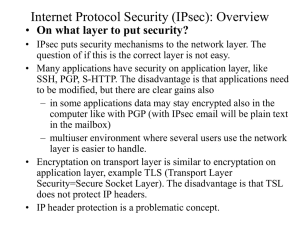
... Internet Protocol Security (IPSec) is a set of extensions to the Internet Protocol (IP) family. ...
... Internet Protocol Security (IPSec) is a set of extensions to the Internet Protocol (IP) family. ...
lesson05 - Seneca - School of Information & Communications
... • This policy is configured to match every incoming connection, regardless of network access server type. • Because the first policy matches all connections to a Microsoft Routing and Remote Access server, this policy will take effect only if an incoming connection is being authenticated by a RADIUS ...
... • This policy is configured to match every incoming connection, regardless of network access server type. • Because the first policy matches all connections to a Microsoft Routing and Remote Access server, this policy will take effect only if an incoming connection is being authenticated by a RADIUS ...
Document
... Legal compliance. For critical applications like, health, public financial records, bank accounts, Government requires the organizations to maintain logs Protecting the trustworthiness of the log sources and also, the logs themselves need to be protected from malicious activities ...
... Legal compliance. For critical applications like, health, public financial records, bank accounts, Government requires the organizations to maintain logs Protecting the trustworthiness of the log sources and also, the logs themselves need to be protected from malicious activities ...
Intruders and password protection
... Use a password manager (PM). It is a utility that creates an encrypted file where your passwords are stored. Try to use "nonsense words." Do not tell anybody your password. ...
... Use a password manager (PM). It is a utility that creates an encrypted file where your passwords are stored. Try to use "nonsense words." Do not tell anybody your password. ...
Collaborative Approaches to Medical Device Cybersecurity
... Health care providers want manufacturers to provide a bill of materials for their devices ...
... Health care providers want manufacturers to provide a bill of materials for their devices ...
The key questions that we`d like to ask at the beginning
... websites have disabled the feature to improve site performance. But as the Heartbleed bug shows, the cost of not running PFS can be far greater than a slight drop in website speed. Even before Heartbleed, forward-thinking websites announced their intention to enable PFS. Twitter introduced PFS to pr ...
... websites have disabled the feature to improve site performance. But as the Heartbleed bug shows, the cost of not running PFS can be far greater than a slight drop in website speed. Even before Heartbleed, forward-thinking websites announced their intention to enable PFS. Twitter introduced PFS to pr ...
8_19Counter Hack 6 scanning
... The Nessus Architecture Supports strong authentication, based on public key encryption. Supports strong encryption based on the twofish and ripemd algorithms. The most common use: running on a single machine. ...
... The Nessus Architecture Supports strong authentication, based on public key encryption. Supports strong encryption based on the twofish and ripemd algorithms. The most common use: running on a single machine. ...
SWIFT Customer Security Program
... Over the past few years, financial services policymakers and regulators have realized that it is now a matter of when, not if, the industry will suffer a major system-wide disruption, one that aims to destroy. Well-publicized attacks in the last 12 months have made this feel probable, not just plaus ...
... Over the past few years, financial services policymakers and regulators have realized that it is now a matter of when, not if, the industry will suffer a major system-wide disruption, one that aims to destroy. Well-publicized attacks in the last 12 months have made this feel probable, not just plaus ...
IPSec: Cryptography basics
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
Application level gateway Firewalls - Mercer University
... Application level firewalls decide whether to drop a packet or send them through based on the application information. They do this by setting up various proxies on a single firewall for different applications. Both the client and the server connect to these proxies instead of connecting directly t ...
... Application level firewalls decide whether to drop a packet or send them through based on the application information. They do this by setting up various proxies on a single firewall for different applications. Both the client and the server connect to these proxies instead of connecting directly t ...
5. Detailed working of RADIUS - Department of Computer Science
... Network administrators have to guard their modems against break-ins in order to maintain the security of the network. The strategy for verifying the identity of, granting access to, and tracking the actions of remote users is known as Authentication, Authorization and Accounting (AAA) RADIUS uses UD ...
... Network administrators have to guard their modems against break-ins in order to maintain the security of the network. The strategy for verifying the identity of, granting access to, and tracking the actions of remote users is known as Authentication, Authorization and Accounting (AAA) RADIUS uses UD ...
The AIG netAdvantage Suite® Coverage Highlights
... client’s digital assets. These are coverages generally not provided under most standard policies. The absence of these specific coverages could expose your clients to significant financial loss. ...
... client’s digital assets. These are coverages generally not provided under most standard policies. The absence of these specific coverages could expose your clients to significant financial loss. ...
faculty.elgin.edu
... • A phishing filter has also been added • Prevents unauthorized Web sites from stealing log-on credentials and other personal information ...
... • A phishing filter has also been added • Prevents unauthorized Web sites from stealing log-on credentials and other personal information ...
Slide 1
... Involves an attempts to define a set of rules or attack patterns that can be used to decide that a given behavior is that of an intruder. Indeed, anomaly approaches attempt to define normal, or expected, behavior, whereas signature-based approaches attempt to define proper behavior. 25-May-17 ...
... Involves an attempts to define a set of rules or attack patterns that can be used to decide that a given behavior is that of an intruder. Indeed, anomaly approaches attempt to define normal, or expected, behavior, whereas signature-based approaches attempt to define proper behavior. 25-May-17 ...
IPS/IDS - SudeeraJ.com
... • Ability to update all the security functions or programs concurrently • Eliminates the need for systems administrators to maintain multiple security programs over time ...
... • Ability to update all the security functions or programs concurrently • Eliminates the need for systems administrators to maintain multiple security programs over time ...
Employee Internet Use Monitoring and Filtering Policy
... that staff member, or self-help or health advice sites might identify a physical or mental health condition. By carrying out such activities using 1836 Technologies’s Internet access facilities, Staff consent to 1836 Technologies processing any sensitive personal data about them that may be revealed ...
... that staff member, or self-help or health advice sites might identify a physical or mental health condition. By carrying out such activities using 1836 Technologies’s Internet access facilities, Staff consent to 1836 Technologies processing any sensitive personal data about them that may be revealed ...
Principals of Information Security, Fourth Edition
... – Protect cardholder data – Maintain vulnerability management program – Implement strong access control measures – Regularly monitor and test networks – Maintain information security policy Principles of Information Security, Fifth Edition ...
... – Protect cardholder data – Maintain vulnerability management program – Implement strong access control measures – Regularly monitor and test networks – Maintain information security policy Principles of Information Security, Fifth Edition ...