ECE/CS 4984: Lecture 11
... ● Nomadic services ● Virtual private networks (VPNs) ● Dynamic Host Configuration Protocol (DHCP) ● Network address translation (NAT) ● Firewalls and packet filtering ● HTML and web programming ● Brief comments on a wireless “hot spot” service ...
... ● Nomadic services ● Virtual private networks (VPNs) ● Dynamic Host Configuration Protocol (DHCP) ● Network address translation (NAT) ● Firewalls and packet filtering ● HTML and web programming ● Brief comments on a wireless “hot spot” service ...
20070228-IMSP2P-Paris
... • What P2P does, it creates an overlay network for a set of specific applications • P2P provides actually a suite of technologies that solves today the problems of IMS ...
... • What P2P does, it creates an overlay network for a set of specific applications • P2P provides actually a suite of technologies that solves today the problems of IMS ...
GÉANT2 - 7th RoEduNet International Conference
... • But GÉANT2 has long PoP-PoP links (~800km, up to ~2000km) • Differential phase shift keying (DPSK) suitable for spans up to 1000km but requires 100 GHz channel spacing • Trial of 40 Gb/s with DPSK modulation planned (likely for Geneva – Frankfurt) just as soon as we can get our hands on it! • 100G ...
... • But GÉANT2 has long PoP-PoP links (~800km, up to ~2000km) • Differential phase shift keying (DPSK) suitable for spans up to 1000km but requires 100 GHz channel spacing • Trial of 40 Gb/s with DPSK modulation planned (likely for Geneva – Frankfurt) just as soon as we can get our hands on it! • 100G ...
PYLON: An Architectural Framework for Ad-Hoc QoS
... can operate directly with extranet traffic. One concern here is the DSCP (Differentiated Service Code Point) set that the ad-hoc domain should use to serve the DiffServ traffic. This is discussed in Section 4 of this study. The basic tenet of SWAN is to maintain a stateless model with no need to pro ...
... can operate directly with extranet traffic. One concern here is the DSCP (Differentiated Service Code Point) set that the ad-hoc domain should use to serve the DiffServ traffic. This is discussed in Section 4 of this study. The basic tenet of SWAN is to maintain a stateless model with no need to pro ...
Bonjour-Standards
... services on IP networks. Bonjour uses industry standard IP protocols to allow devices to automatically discover each other without the need to enter IP addresses or configure DNS servers. Specifically, Bonjour enables automatic IP address assignment without a DHCP server, name to address translation ...
... services on IP networks. Bonjour uses industry standard IP protocols to allow devices to automatically discover each other without the need to enter IP addresses or configure DNS servers. Specifically, Bonjour enables automatic IP address assignment without a DHCP server, name to address translation ...
Technical Report DSL Forum TR-059
... The service must address a wider market with: o Variable speeds, o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more typ ...
... The service must address a wider market with: o Variable speeds, o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more typ ...
The Essential Guide for Wireless ISPs Broadband Wireless Access
... Providers industry for comprehensive information on Broadband Wireless Access (BWA). It is intended for ISPs who are looking at BWA as an alternative to traditional wire- or cable-based services, including: a. An established ISP that considers adding BWA to its infrastructure for one or more of the ...
... Providers industry for comprehensive information on Broadband Wireless Access (BWA). It is intended for ISPs who are looking at BWA as an alternative to traditional wire- or cable-based services, including: a. An established ISP that considers adding BWA to its infrastructure for one or more of the ...
Chapter 13 PowerPoint
... The latest update to PPTP has added support for MSCHAPv2 and EAP authentication. With PPTP deployed, it is possible to determine the password by using a dictionary attack if weak passwords have been used. If weak passwords are a major concern, ensure that all remote access clients use Windows 2000, ...
... The latest update to PPTP has added support for MSCHAPv2 and EAP authentication. With PPTP deployed, it is possible to determine the password by using a dictionary attack if weak passwords have been used. If weak passwords are a major concern, ensure that all remote access clients use Windows 2000, ...
Application Enablement Services 4.1 SDKs
... Avaya Application Enablement (AE) Services is a software platform that provides connectivity between client applications and Avaya Communication Manager. AE Services includes an enhanced set of Application Programming Interfaces (APIs), client-side libraries, protocols, and web services that expose ...
... Avaya Application Enablement (AE) Services is a software platform that provides connectivity between client applications and Avaya Communication Manager. AE Services includes an enhanced set of Application Programming Interfaces (APIs), client-side libraries, protocols, and web services that expose ...
An Architectural Framework for Inter
... and negotiates them with SLS Order Handling in the downstream peer. SLS Order Handling in turn performs subscription level admission control (AC). It takes incoming pSLS requests and investigates based on information from Offline TE whether there is sufficient intra- and inter-domain capacity. For i ...
... and negotiates them with SLS Order Handling in the downstream peer. SLS Order Handling in turn performs subscription level admission control (AC). It takes incoming pSLS requests and investigates based on information from Offline TE whether there is sufficient intra- and inter-domain capacity. For i ...
Ericsson Mobility Report
... outlook All regions are showing continued growth in mobile subscriptions. In Asia Pacific, this is driven by new subscribers. In more mature markets, such as North America and Western Europe, the growth comes from the increasing number of subscriptions per individual – for example, many have recentl ...
... outlook All regions are showing continued growth in mobile subscriptions. In Asia Pacific, this is driven by new subscribers. In more mature markets, such as North America and Western Europe, the growth comes from the increasing number of subscriptions per individual – for example, many have recentl ...
Remote Access Techniques
... Network administrators can offer both modes of operation—remote node and remote control—to their users and let them decide which one is most appropriate to their needs and environments. For this there are hybrid remote access solutions that integrate remote control, remote node, and other communicat ...
... Network administrators can offer both modes of operation—remote node and remote control—to their users and let them decide which one is most appropriate to their needs and environments. For this there are hybrid remote access solutions that integrate remote control, remote node, and other communicat ...
Exploration_LAN_Switching_Chapter7-TonyChen
... when moving a person within a building, reorganizing a lab, or moving to temporary locations or project sites. –Another example is when a company moves into a new building that does not have any wired infrastructure. In this case, the savings resulting from using WLANs can be even more noticeable, b ...
... when moving a person within a building, reorganizing a lab, or moving to temporary locations or project sites. –Another example is when a company moves into a new building that does not have any wired infrastructure. In this case, the savings resulting from using WLANs can be even more noticeable, b ...
Wireless LANs - College of DuPage
... moving a person within a building, reorganizing a lab, or moving to temporary locations or project sites. –Another example is when a company moves into a new building that does not have any wired infrastructure. In this case, the savings resulting from using WLANs can be even more noticeable, becaus ...
... moving a person within a building, reorganizing a lab, or moving to temporary locations or project sites. –Another example is when a company moves into a new building that does not have any wired infrastructure. In this case, the savings resulting from using WLANs can be even more noticeable, becaus ...
DTPC Acceptable Use Guidelines for Dube iConnect
... Spam and unsolicited bulk mail are highly problematic practices. They affect the use and enjoyment of services by others and often compromise network security. Dube iConnect will take swift and firm action against any user engaging in any of the following unacceptable practices: 1. Sending unsolicit ...
... Spam and unsolicited bulk mail are highly problematic practices. They affect the use and enjoyment of services by others and often compromise network security. Dube iConnect will take swift and firm action against any user engaging in any of the following unacceptable practices: 1. Sending unsolicit ...
Management`s Discussion and Analysis
... fastest high-speed Internet plans which offer unlimited access and download speeds of up to 250 Mbps. • Providing the best Internet coverage – MTS provides high-speed Internet coverage to over 87% of homes, making it the most comprehensive Internet service in the province. High-speed Internet subscr ...
... fastest high-speed Internet plans which offer unlimited access and download speeds of up to 250 Mbps. • Providing the best Internet coverage – MTS provides high-speed Internet coverage to over 87% of homes, making it the most comprehensive Internet service in the province. High-speed Internet subscr ...
Systematic Design of Space-Time Trellis Codes for Wireless
... Both cellular and D2D users adaptively adjust the transmit power according to the SINR report. Typically, the D2D users can control the transmit power at first, and then the cellular users make change afterward. This iterative process terminates until all the users meet their SINR ...
... Both cellular and D2D users adaptively adjust the transmit power according to the SINR report. Typically, the D2D users can control the transmit power at first, and then the cellular users make change afterward. This iterative process terminates until all the users meet their SINR ...
WiFi Security: WEP, WPA, and WPA2
... – for some seed values (called weak keys), the beginning of the RC4 output is not really random – if a weak key is used, then the first few bytes of the output reveals a lot of information about the key Æ breaking the key is made easier – for this reason, crypto experts suggest to always throw away ...
... – for some seed values (called weak keys), the beginning of the RC4 output is not really random – if a weak key is used, then the first few bytes of the output reveals a lot of information about the key Æ breaking the key is made easier – for this reason, crypto experts suggest to always throw away ...
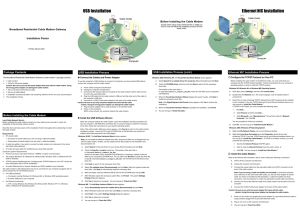
Ethernet NIC Installation USB Installation
... Cable LED is not lit or keeps blinking Orange Possible reason: The cable modem cannot detect any carrier or valid data channel from the coaxial cable. Action: Make sure the connectors at each end of the coaxial cable are securely seated. If the problem persists, please contact your cable modem servi ...
... Cable LED is not lit or keeps blinking Orange Possible reason: The cable modem cannot detect any carrier or valid data channel from the coaxial cable. Action: Make sure the connectors at each end of the coaxial cable are securely seated. If the problem persists, please contact your cable modem servi ...