IPv6 - Labs
... The increasing scarcity of Ipv4 will force carriage providers to add address sharing mechanisms into the ...
... The increasing scarcity of Ipv4 will force carriage providers to add address sharing mechanisms into the ...
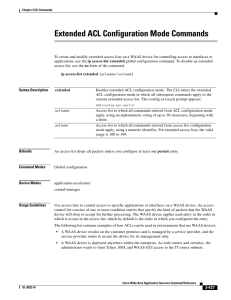
Extended ACL Configuration Mode Commands
... Use access lists to control access to specific applications or interfaces on a WAAS device. An access control list consists of one or more condition entries that specify the kind of packets that the WAAS device will drop or accept for further processing. The WAAS device applies each entry in the ord ...
... Use access lists to control access to specific applications or interfaces on a WAAS device. An access control list consists of one or more condition entries that specify the kind of packets that the WAAS device will drop or accept for further processing. The WAAS device applies each entry in the ord ...
pana-3
... • Need for a subscriber access authentication mechanism – DSL Forum working around DHCP evolution for supporting EAP • DSL Liaison discussion during IETF70 in the Internet Area meeting session ...
... • Need for a subscriber access authentication mechanism – DSL Forum working around DHCP evolution for supporting EAP • DSL Liaison discussion during IETF70 in the Internet Area meeting session ...
Alcatel-Lucent OmniAccess 5510
... The Alcatel-Lucent OmniAccess 5510 Unified Services Gateway (USG) router is a compact, affordable, and purpose-built platform for simultaneous, secure, wire-speed delivery of voice and data services to small offices. It has been specifically designed to meet the needs of carrier managed services app ...
... The Alcatel-Lucent OmniAccess 5510 Unified Services Gateway (USG) router is a compact, affordable, and purpose-built platform for simultaneous, secure, wire-speed delivery of voice and data services to small offices. It has been specifically designed to meet the needs of carrier managed services app ...
Document
... IPv6 Status Today in India 1. Major ISP TCL, Bharti, Reliance, SIFY etc in India are ready for IPv6 Services. 2. IPv6 Penetration in India is less than 1% 3. Many ISPs lack the network infrastructure to handle IPv6 4. Access Infrastructure not IPv6 ready 5. IPv6 Penetration in Broadband /Mobile In ...
... IPv6 Status Today in India 1. Major ISP TCL, Bharti, Reliance, SIFY etc in India are ready for IPv6 Services. 2. IPv6 Penetration in India is less than 1% 3. Many ISPs lack the network infrastructure to handle IPv6 4. Access Infrastructure not IPv6 ready 5. IPv6 Penetration in Broadband /Mobile In ...
IPX Transport Service
... A carrier connects Service Provider to exchange any kind of data with specific quality differentiation. This IPX Transit service can be used to exchange any kind of data if agreed so between the Service Providers, examples being WiFi authentication, RCS interconnect, LTE data roaming payload, 2G/3G ...
... A carrier connects Service Provider to exchange any kind of data with specific quality differentiation. This IPX Transit service can be used to exchange any kind of data if agreed so between the Service Providers, examples being WiFi authentication, RCS interconnect, LTE data roaming payload, 2G/3G ...
Voice over IP
... B. Establish a 10 digit emergency number in a central office that call forwards, with ANI of that CO number, to the central office’s 9-1-1 trunk group into the Selective Router. For both routing control to the target PSAP, and for ALI purposes, establish a fixed ALI record against that call forward ...
... B. Establish a 10 digit emergency number in a central office that call forwards, with ANI of that CO number, to the central office’s 9-1-1 trunk group into the Selective Router. For both routing control to the target PSAP, and for ALI purposes, establish a fixed ALI record against that call forward ...
The Fundamentals of Passive Monitoring Access
... Switched Port Analyzer (SPAN) Ports, also referred to as “port mirroring” and “port monitoring,” present combined traffic from multiple switch ports. Advantages: • Easy access to network traffic because a single NIC on the sensor can connect to a single SPAN port on the switch • SPAN ports can combi ...
... Switched Port Analyzer (SPAN) Ports, also referred to as “port mirroring” and “port monitoring,” present combined traffic from multiple switch ports. Advantages: • Easy access to network traffic because a single NIC on the sensor can connect to a single SPAN port on the switch • SPAN ports can combi ...
Admission Control in IP Multicast over Heterogeneous Access
... • IP Multicast Open architecture – Receivers are free to join any group – Sources are free to transmit to any group Makes IP multicast-based commercial services difficult to implement ...
... • IP Multicast Open architecture – Receivers are free to join any group – Sources are free to transmit to any group Makes IP multicast-based commercial services difficult to implement ...
PowerConnect W-Series OS (OPERATING SYSTEM
... Dell PowerConnect W-Series Adaptive Radio Management (ARM) takes the guesswork out of AP deployments. Once APs are brought up, they immediately begin monitoring their local environment for interference, noise, and signals being received from other Dell PowerConnect W-Series APs. This information is ...
... Dell PowerConnect W-Series Adaptive Radio Management (ARM) takes the guesswork out of AP deployments. Once APs are brought up, they immediately begin monitoring their local environment for interference, noise, and signals being received from other Dell PowerConnect W-Series APs. This information is ...
App Development for Smart Devices
... • You must have a client and a server. Used classes are: ➤ BluetoothServerSocket: Used to establish a listening socket at the server for initiating a link between devices. ➤ BluetoothSocket: Used in creating a new client socket to connect to a listening Bluetooth Server Socket, and returned by the ...
... • You must have a client and a server. Used classes are: ➤ BluetoothServerSocket: Used to establish a listening socket at the server for initiating a link between devices. ➤ BluetoothSocket: Used in creating a new client socket to connect to a listening Bluetooth Server Socket, and returned by the ...
Mobility Devices
... Corridor warriors are typically mobile professionals, including executives and healthcare workers, and mobile students in campus environments. They travel less than 20 percent of the time and are usually dashing through the corridors from one meeting or one patient to the next. They require access t ...
... Corridor warriors are typically mobile professionals, including executives and healthcare workers, and mobile students in campus environments. They travel less than 20 percent of the time and are usually dashing through the corridors from one meeting or one patient to the next. They require access t ...
Document
... Differences between planning of CNs (Community Networks), and ISPs’ and other service providers’ design methodology Requirements to take into account in the planning of CNs Ubiquitous Wi-Fi access covering the whole territory of the community (e.g. a city, a county or a province), no matter if ...
... Differences between planning of CNs (Community Networks), and ISPs’ and other service providers’ design methodology Requirements to take into account in the planning of CNs Ubiquitous Wi-Fi access covering the whole territory of the community (e.g. a city, a county or a province), no matter if ...
Document
... event signaling: server can push content to the client event handling table indicating how to react on certain events from the network client may now be able to handle unknown events telephony functions some application on the client may access telephony functions ...
... event signaling: server can push content to the client event handling table indicating how to react on certain events from the network client may now be able to handle unknown events telephony functions some application on the client may access telephony functions ...
Before You Begin: Assign Information Classification
... data) together over a common, QoS, managed, secure network Integrate wireless and wired VPN into enterprise LAN management and control Inbound request is directed based on the citizens’ need and access type Session Number Presentation_ID ...
... data) together over a common, QoS, managed, secure network Integrate wireless and wired VPN into enterprise LAN management and control Inbound request is directed based on the citizens’ need and access type Session Number Presentation_ID ...
MEDS – Sample Report - MIEL e
... This report is being supplied by us on the basis that it is for your benefit and information only and that, save as may be required by law or by a competent regulatory authority (in which case you shall inform us in advance), it shall not be copied, referred to or disclosed, in whole (save for your ...
... This report is being supplied by us on the basis that it is for your benefit and information only and that, save as may be required by law or by a competent regulatory authority (in which case you shall inform us in advance), it shall not be copied, referred to or disclosed, in whole (save for your ...
What is wireless networking?
... How many wireless networked computers can use a single access point? Can I have more than one access point? What is Roaming? How can I use a wireless network to interconnect two LANs? Is it true that wireless networking is only good for laptop computers? Wireless Network Security? ...
... How many wireless networked computers can use a single access point? Can I have more than one access point? What is Roaming? How can I use a wireless network to interconnect two LANs? Is it true that wireless networking is only good for laptop computers? Wireless Network Security? ...