
Description
... The authentication feature is used in subscriber identification, authentication, and synchronization of the encryption key. This feature checks the validity of a subscriber's service requests to ensure that only legal subscribers can use network services. The authentication procedure is performed in ...
... The authentication feature is used in subscriber identification, authentication, and synchronization of the encryption key. This feature checks the validity of a subscriber's service requests to ensure that only legal subscribers can use network services. The authentication procedure is performed in ...
ExperimenTor: A Testbed for Safe and Realistic Tor Experimentation Kevin Bauer
... from Tor’s directory servers to model Tor routers. Alternatively, this type of analysis could be done with emulated Tor clients running the real Tor code in a testbed environment. In addition, parts of Tor’s design and operation have been implemented as discrete-event simulators. Using the Scalable ...
... from Tor’s directory servers to model Tor routers. Alternatively, this type of analysis could be done with emulated Tor clients running the real Tor code in a testbed environment. In addition, parts of Tor’s design and operation have been implemented as discrete-event simulators. Using the Scalable ...
PDF
... Hop count is 2 10.5.5.3 (GigabitEthernet3/0), from 10.5.5.3, Send flag is 0x0 Composite metric is (28672/28416), Route is Internal Vector metric: Minimum bandwidth is 100000 Kbit Total delay is 120 microseconds Reliability is 255/255 Load is 1/255 Minimum MTU is 1500 Hop count is 2 Router 1 will not ...
... Hop count is 2 10.5.5.3 (GigabitEthernet3/0), from 10.5.5.3, Send flag is 0x0 Composite metric is (28672/28416), Route is Internal Vector metric: Minimum bandwidth is 100000 Kbit Total delay is 120 microseconds Reliability is 255/255 Load is 1/255 Minimum MTU is 1500 Hop count is 2 Router 1 will not ...
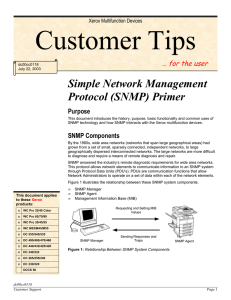
Simple Network Management Protocol (SNMP) Primer
... and getNextRequest commands with the Read-Only community name. Read-Write: A Read-Write setting allows the value of the MIB object to be accessed as well as modified. A client can issue the setRequest command as well as the getRequest and getNextRequest. If one tries to access an SNMP Agent with the ...
... and getNextRequest commands with the Read-Only community name. Read-Write: A Read-Write setting allows the value of the MIB object to be accessed as well as modified. A client can issue the setRequest command as well as the getRequest and getNextRequest. If one tries to access an SNMP Agent with the ...
Wireless Sniffing With Wireshark
... help administrators troubleshoot wireless networks. With the appropriate driver support, Wireshark can capture traffic “from the air” and decode it into a format that helps administrators track down issues that are causing poor performance, intermittent connectivity, and other common problems. Wires ...
... help administrators troubleshoot wireless networks. With the appropriate driver support, Wireshark can capture traffic “from the air” and decode it into a format that helps administrators track down issues that are causing poor performance, intermittent connectivity, and other common problems. Wires ...
Application Note: How to Evaluate WirelessHART Network and Device Performance
... using or selling these products for use in such applications do so at their own risk and agree to fully indemnify and hold Dust Networks and its officers, employees, subsidiaries, affiliates, and distributors harmless against all claims, costs, damages, and expenses, and reasonable attorney fees ari ...
... using or selling these products for use in such applications do so at their own risk and agree to fully indemnify and hold Dust Networks and its officers, employees, subsidiaries, affiliates, and distributors harmless against all claims, costs, damages, and expenses, and reasonable attorney fees ari ...
Cisco IP SLA`s
... • Optimize IP business applications and services Voice over IP, Video, and VPN ...
... • Optimize IP business applications and services Voice over IP, Video, and VPN ...
Cisco WRVS4400N Wireless-N Gigabit Security Router
... Networking and Security Basics An Introduction to LANs A Router is a network device that connects multiple networks together and forward traffic based on IP destination of each packet. The Wireless-N Gigabit Security Router can connect your local area network (LAN) or a group of PCs interconnected i ...
... Networking and Security Basics An Introduction to LANs A Router is a network device that connects multiple networks together and forward traffic based on IP destination of each packet. The Wireless-N Gigabit Security Router can connect your local area network (LAN) or a group of PCs interconnected i ...
TTAS tandard - TTA표준화 위원회
... When the subscriber happens to be under WLAN coverage, it is beneficial for the operator to offload some traffic(e.g. best effort) to the WLAN access. At the same time it may be beneficial to still keep some traffic(e.g. VoIP flow) in the cellular access. With this IP flow mobility solution the oper ...
... When the subscriber happens to be under WLAN coverage, it is beneficial for the operator to offload some traffic(e.g. best effort) to the WLAN access. At the same time it may be beneficial to still keep some traffic(e.g. VoIP flow) in the cellular access. With this IP flow mobility solution the oper ...
Unix System Administration
... • –m limit sets maximum number of SYN packets – iptables is being configured to allow the firewall to accept maxim 5 TCP/SYN packeds per second on interface eth0. iptables -A INPUT -p tcp --syn -m limit --limit 5/s -i eth0 -j ACCEPT – If more than 5 SYN packets per second, the packets are dropped. – ...
... • –m limit sets maximum number of SYN packets – iptables is being configured to allow the firewall to accept maxim 5 TCP/SYN packeds per second on interface eth0. iptables -A INPUT -p tcp --syn -m limit --limit 5/s -i eth0 -j ACCEPT – If more than 5 SYN packets per second, the packets are dropped. – ...
Chapter 3
... In contrast, Hyper Text Transfer Protocol, or HTTP, is a protocol used to transfer files from a Web server onto a browser in order to view a Web page. Unlike FTP, where entire files are transferred from one device to another and copied into memory and then disk, HTTP only transfers the contents of a ...
... In contrast, Hyper Text Transfer Protocol, or HTTP, is a protocol used to transfer files from a Web server onto a browser in order to view a Web page. Unlike FTP, where entire files are transferred from one device to another and copied into memory and then disk, HTTP only transfers the contents of a ...
Performance Characterization and Call Reliability
... VoLTE deployment by U.S. operators is still at an early stage, but it is important to empirically understand its performance from the perspective of mobile end users, especially compared to legacy call and OTT VoIP call. In this paper, we present the first systematic study using a variety of importa ...
... VoLTE deployment by U.S. operators is still at an early stage, but it is important to empirically understand its performance from the perspective of mobile end users, especially compared to legacy call and OTT VoIP call. In this paper, we present the first systematic study using a variety of importa ...
M/TCP - Internet Conference 2016
... Nevertheless, the reliable service provided by TCP is still lower compared with the public communication network using multiple data paths for backup. An outstanding reason is that TCP implementations such as Reno and Tahoe [5, 6] are a single connection. If the network interface associated with the ...
... Nevertheless, the reliable service provided by TCP is still lower compared with the public communication network using multiple data paths for backup. An outstanding reason is that TCP implementations such as Reno and Tahoe [5, 6] are a single connection. If the network interface associated with the ...
technology - Csiservices.ca
... Current Technologies Of Interest To Criminals Investigative Considerations In Today’s Technologies ...
... Current Technologies Of Interest To Criminals Investigative Considerations In Today’s Technologies ...
D1.1: Functional Architecture Definition and Top Level
... the IP header. The IETF DiffServ Working Group transformed the concept into a true architecture by – amongst others – defining the Per Hop Behaviours (PHB) and designing the functionality of DiffServ edge routers, i.e. filters, meters, markers, etc. The network operator has now at his disposal a ser ...
... the IP header. The IETF DiffServ Working Group transformed the concept into a true architecture by – amongst others – defining the Per Hop Behaviours (PHB) and designing the functionality of DiffServ edge routers, i.e. filters, meters, markers, etc. The network operator has now at his disposal a ser ...
Exploring and Improving BitTorrent Swarm Topologies
... the global internet traffic that is attributed to peer-to-peer (P2P) traffic close to a third is due to BitTorrent[11] making it the most used P2P protocol. Its scalability, reduced download times and resilience compared to traditional client-server based systems make it the de-facto standard for th ...
... the global internet traffic that is attributed to peer-to-peer (P2P) traffic close to a third is due to BitTorrent[11] making it the most used P2P protocol. Its scalability, reduced download times and resilience compared to traditional client-server based systems make it the de-facto standard for th ...
IP Networks Curriculum
... Live classroom and online training from the world’s leading telecommunications training company. ...
... Live classroom and online training from the world’s leading telecommunications training company. ...
Demystifying Layer 2 and Layer 3 VPNs
... 4.3 Business Features of Layer 2 and Layer 3 Services ................................................................................................................................................................... 37 4.3.1 Multi-point Any-to-Any Connectivity ..................................... ...
... 4.3 Business Features of Layer 2 and Layer 3 Services ................................................................................................................................................................... 37 4.3.1 Multi-point Any-to-Any Connectivity ..................................... ...
Lecture 8 - cda college
... Switched Multimegabit Data Service Special Interest Group (SMDS SIG) ...
... Switched Multimegabit Data Service Special Interest Group (SMDS SIG) ...
User Guide Linksys E-Series Routers
... How to optimize your router for gaming and voice . . . . . . . . How to remotely change your router settings . . . . . . . . . . . How to enable Voice over IP on your network . . . . . . . . . . . How to configure UPnP . . . . . . . . . . . . . . . . . . ...
... How to optimize your router for gaming and voice . . . . . . . . How to remotely change your router settings . . . . . . . . . . . How to enable Voice over IP on your network . . . . . . . . . . . How to configure UPnP . . . . . . . . . . . . . . . . . . ...
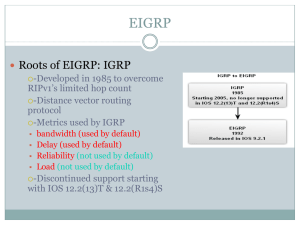
EIGRP
... connected neighbors, it can calculate its DUAL 1st metric is calculated for each route 2nd route with lowest metric is designated successor & is placed in routing table 3rd feasible successor is found –Criteria for feasible successor: it must have lower reported distance to the destination tha ...
... connected neighbors, it can calculate its DUAL 1st metric is calculated for each route 2nd route with lowest metric is designated successor & is placed in routing table 3rd feasible successor is found –Criteria for feasible successor: it must have lower reported distance to the destination tha ...
PDF
... On-device and network event correlation—Cisco Meta Event Generator provides an "onbox" correlation method to deliver accurate worm classification. Cisco IPS Sensor Software incorporates advanced sensor-level event correlation and knowledge base anomaly detection that gives security administrators an ...
... On-device and network event correlation—Cisco Meta Event Generator provides an "onbox" correlation method to deliver accurate worm classification. Cisco IPS Sensor Software incorporates advanced sensor-level event correlation and knowledge base anomaly detection that gives security administrators an ...
SwitchBlade® x908 [Rev ZJ]
... the network. Real-time applications like surveillance, video streaming and Voice over IP (VoIP) are used alongside data and Internet access. When a high-performing, resilient Enterprise core network is required, using EPSRing with the SwitchBlade x908 provides the ideal solution. EPSR creates a high ...
... the network. Real-time applications like surveillance, video streaming and Voice over IP (VoIP) are used alongside data and Internet access. When a high-performing, resilient Enterprise core network is required, using EPSRing with the SwitchBlade x908 provides the ideal solution. EPSR creates a high ...




















![SwitchBlade® x908 [Rev ZJ]](http://s1.studyres.com/store/data/008053519_1-53b0e3770fa5647be537fdbf48703248-300x300.png)