Getting Started Guide
... ZoneAlarm® Secure Wireless Router Z100G is the first comprehensive security solution for home networks. Developed and supported by SofaWare Technologies, an affiliate of Check Point Software Technologies, the worldwide leader in securing the Internet, ZoneAlarm® Secure Wireless Router Z100G incorpor ...
... ZoneAlarm® Secure Wireless Router Z100G is the first comprehensive security solution for home networks. Developed and supported by SofaWare Technologies, an affiliate of Check Point Software Technologies, the worldwide leader in securing the Internet, ZoneAlarm® Secure Wireless Router Z100G incorpor ...
IP Based VPNs
... • The Provider (P) routers or non-edge backbone routers need not be VPN aware. In piggyback models, the provider/intermediate routers may be VPN aware to determine if the packets sent belong to the VPN or the backbone routing • Backbone protocol can be independent of the VR protocol used • No change ...
... • The Provider (P) routers or non-edge backbone routers need not be VPN aware. In piggyback models, the provider/intermediate routers may be VPN aware to determine if the packets sent belong to the VPN or the backbone routing • Backbone protocol can be independent of the VR protocol used • No change ...
3rd Edition: Chapter 4 - Northwestern Networks Group
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
Chapter 7 TCP Traffic Control
... — proceed with incrementing the congestion window size by adding 1 segment for each ACK received ...
... — proceed with incrementing the congestion window size by adding 1 segment for each ACK received ...
Admission Control in IP Multicast over Heterogeneous Access
... – Receivers are free to join any group – Sources are free to transmit to any group Makes IP multicast-based commercial services difficult to implement ...
... – Receivers are free to join any group – Sources are free to transmit to any group Makes IP multicast-based commercial services difficult to implement ...
Panasonic Ethernet
... and a short processing time. ■ TCP/IP establishes logical point-to-point communication between two devices and provides the basics for exchanging information among all areas of production. ■ You can connect 8 ethernet connections with each other at a transmission speed of up to 100Mbits/sec. ■ ...
... and a short processing time. ■ TCP/IP establishes logical point-to-point communication between two devices and provides the basics for exchanging information among all areas of production. ■ You can connect 8 ethernet connections with each other at a transmission speed of up to 100Mbits/sec. ■ ...
15-441 Lecture
... • Hard to pre-compute multicast trees for all possible sources and all possible groups – Otherwise, may end up with a lot of unwanted state where there are no senders ...
... • Hard to pre-compute multicast trees for all possible sources and all possible groups – Otherwise, may end up with a lot of unwanted state where there are no senders ...
ppt
... Periodic Updates: Updates to the routing tables are sent at the end of a certain time period. A typical value is 30 seconds. Triggered Updates: If a metric changes on a link, a router immediately sends out an update without waiting for the end of the update period. Full Routing Table Update: Most di ...
... Periodic Updates: Updates to the routing tables are sent at the end of a certain time period. A typical value is 30 seconds. Triggered Updates: If a metric changes on a link, a router immediately sends out an update without waiting for the end of the update period. Full Routing Table Update: Most di ...
A Review on Routing Information Protocol (RIP) and Open Shortest
... in the network by overflowing of OSPF link state advertisements (LSA). In this protocol source is the root and multicast receivers are the terminal nodes and this cluster info is used by the routers to build the shortest path tree. OSPF is an interior routing protocol deliberate to be used within a ...
... in the network by overflowing of OSPF link state advertisements (LSA). In this protocol source is the root and multicast receivers are the terminal nodes and this cluster info is used by the routers to build the shortest path tree. OSPF is an interior routing protocol deliberate to be used within a ...
BlueTooth Simulation - Networked Software Systems Laboratory
... Bluetooth scheduling algorithm. We will shortly explain each of these problems. Bluetooth scatternets problem Although scatternets are defined by BT specifications, there are some uncovered points which need to be specific handled. A simple example is considering a master that is also a slave in a ...
... Bluetooth scheduling algorithm. We will shortly explain each of these problems. Bluetooth scatternets problem Although scatternets are defined by BT specifications, there are some uncovered points which need to be specific handled. A simple example is considering a master that is also a slave in a ...
Practical Network-Wide Compression of IP Routing Tables
... Flexibility: By default, MMS operates in a transparent fashion, with absolutely no changes to the way routes are chosen and packets are forwarded. In this “transparent mode” external networks (e.g., other ASes) need not be aware that an MMS has been deployed. In such a situation, the MMS can still p ...
... Flexibility: By default, MMS operates in a transparent fashion, with absolutely no changes to the way routes are chosen and packets are forwarded. In this “transparent mode” external networks (e.g., other ASes) need not be aware that an MMS has been deployed. In such a situation, the MMS can still p ...
CCNA 1: Chapter 11 Exam Answer v4.0 100%
... The connection between routers B and C has been successfully tested. However, after rebooting router C, the administrator noticed the response time between networks 10.10.3.0 and 10.10.4.0 is slower. Ping between the two routers is successful. A trace route indicates three hops from router B to rout ...
... The connection between routers B and C has been successfully tested. However, after rebooting router C, the administrator noticed the response time between networks 10.10.3.0 and 10.10.4.0 is slower. Ping between the two routers is successful. A trace route indicates three hops from router B to rout ...
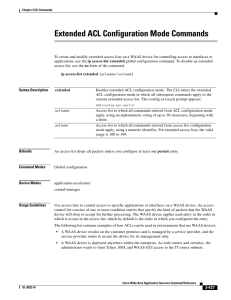
Extended ACL Configuration Mode Commands
... Replace wildcard with the dotted decimal notation for a mask that is the reverse of a subnet mask, where a 0 indicates a position that must be matched and a 1 indicates a position that does not matter. For instance, the wildcard 0.0.0.255 causes the last eight bits in the source IP address to be ign ...
... Replace wildcard with the dotted decimal notation for a mask that is the reverse of a subnet mask, where a 0 indicates a position that must be matched and a 1 indicates a position that does not matter. For instance, the wildcard 0.0.0.255 causes the last eight bits in the source IP address to be ign ...
cPacket Networks - Semantic Scholar
... consumers of ultra-low latency, as it relates to the competitive advantage in electronic trading, has substantially increased in 2009. Furthermore, new regulations put more responsibility on brokers and exchanges to ensure that trades are executed at the best available price. Distributed trading app ...
... consumers of ultra-low latency, as it relates to the competitive advantage in electronic trading, has substantially increased in 2009. Furthermore, new regulations put more responsibility on brokers and exchanges to ensure that trades are executed at the best available price. Distributed trading app ...
module_42 - Faculty Personal Homepage
... Packetizer encapsulates a certain number of speech samples into packets and adds the RTP, UDP, IP, and Ethernet headers. Playback Buffer absorbs variations or jitter in delay and provide a smooth playout. Depacketizer strips headers Decoder reconstructs the original voice signal. K. Salah ...
... Packetizer encapsulates a certain number of speech samples into packets and adds the RTP, UDP, IP, and Ethernet headers. Playback Buffer absorbs variations or jitter in delay and provide a smooth playout. Depacketizer strips headers Decoder reconstructs the original voice signal. K. Salah ...
Study on a Fast OSPF Route Reconstruction Method Under Network
... to the DR. If the DR does not respond to 4 hello packets from a neighbor, a neighbor detects DR failure and all neighbors start to elect new DR among their own neighbors. The hello packet interval is 10 sec (Hello Interval, default value), hence it takes 40 sec (Router Dead Interval) for neighbors t ...
... to the DR. If the DR does not respond to 4 hello packets from a neighbor, a neighbor detects DR failure and all neighbors start to elect new DR among their own neighbors. The hello packet interval is 10 sec (Hello Interval, default value), hence it takes 40 sec (Router Dead Interval) for neighbors t ...
cti - High Speed Network
... Established Channels will be increasingly augmented by Internet and Web-related technologies. Each of the technologies outlined below are available today. Several still require improvements in scalability, security, or robustness; but, none are fantasy... ESTABLISHED CHANNELS Direct Physical Inte ...
... Established Channels will be increasingly augmented by Internet and Web-related technologies. Each of the technologies outlined below are available today. Several still require improvements in scalability, security, or robustness; but, none are fantasy... ESTABLISHED CHANNELS Direct Physical Inte ...
Service-Built Edge & CPE Initiative: M7i & M10i Overview
... Network Consolidation - Before Resilient Low latency ...
... Network Consolidation - Before Resilient Low latency ...
Elmustafa Sayed Ali Ahmed and Rashid A. Saeed
... includes mobile gateways and mobile Internet nodes, which are one-hop away from Mobile IP foreign agents; the third layer has all MANET nodes and visiting mobile Internet nodes that are at least one-hop away from mobile gateways. The second layer is to provide Internet. Mobile gateways are powerful ...
... includes mobile gateways and mobile Internet nodes, which are one-hop away from Mobile IP foreign agents; the third layer has all MANET nodes and visiting mobile Internet nodes that are at least one-hop away from mobile gateways. The second layer is to provide Internet. Mobile gateways are powerful ...
the document - Support
... The NE9000 supports multicast traffic forwarding at line rate. The NE9000 hardware supports two-level multicast traffic replication: replication from switch fabric units (SFUs) to line processing units (LPUs) and replication from an LPU's forwarding engine to interfaces on the ...
... The NE9000 supports multicast traffic forwarding at line rate. The NE9000 hardware supports two-level multicast traffic replication: replication from switch fabric units (SFUs) to line processing units (LPUs) and replication from an LPU's forwarding engine to interfaces on the ...
Module 2 - OoCities
... at MIT in 1957.(Answer: John McCarthy). Q15: ARPA’s networking project Managed by ______________ from MIT. (Answer: Lawrence Robert). Q16: Nodes with large time-sharing computers at the connected sites are called _____________. (Answer: hosts). Q17: What’s the different between Circuit-switching vs. ...
... at MIT in 1957.(Answer: John McCarthy). Q15: ARPA’s networking project Managed by ______________ from MIT. (Answer: Lawrence Robert). Q16: Nodes with large time-sharing computers at the connected sites are called _____________. (Answer: hosts). Q17: What’s the different between Circuit-switching vs. ...
EE 122: Computer Networks
... Border Gateway Protocol (BGP) • Interdomain routing protocol for the Internet –Prefix-based path-vector protocol –Policy-based routing based on AS Paths –Evolved during the past 20 years • 1989 : BGP-1 [RFC 1105] – Replacement for EGP (1984, RFC 904) ...
... Border Gateway Protocol (BGP) • Interdomain routing protocol for the Internet –Prefix-based path-vector protocol –Policy-based routing based on AS Paths –Evolved during the past 20 years • 1989 : BGP-1 [RFC 1105] – Replacement for EGP (1984, RFC 904) ...