SQLScript Guide SAP - SCN Wiki
... provided that the above copyright notice appear in all copies and that both that copyright notice and this permission notice appear in supporting documentation. Hewlett-Packard Company makes no representations about the suitability of this software for any purpose. It is provided “as is” without exp ...
... provided that the above copyright notice appear in all copies and that both that copyright notice and this permission notice appear in supporting documentation. Hewlett-Packard Company makes no representations about the suitability of this software for any purpose. It is provided “as is” without exp ...
Database Security and Auditing
... – Use any user other than SYS or SYSTEM to create a table – Add three rows into the table – Log on as SYSTEM or SYS to enable auditing: For ALTER and DELETE – Log in as DBSEC: • Delete a row • Modify the structure of the table Database Security and Auditing ...
... – Use any user other than SYS or SYSTEM to create a table – Add three rows into the table – Log on as SYSTEM or SYS to enable auditing: For ALTER and DELETE – Log in as DBSEC: • Delete a row • Modify the structure of the table Database Security and Auditing ...
Database Security and Auditing
... – Use any user other than SYS or SYSTEM to create a table – Add three rows into the table – Log on as SYSTEM or SYS to enable auditing: For ALTER and DELETE – Log in as DBSEC: • Delete a row • Modify the structure of the table Database Security and Auditing ...
... – Use any user other than SYS or SYSTEM to create a table – Add three rows into the table – Log on as SYSTEM or SYS to enable auditing: For ALTER and DELETE – Log in as DBSEC: • Delete a row • Modify the structure of the table Database Security and Auditing ...
What is an Embedded Database? - Downloads
... Implement best practices (pre-upgrade database backup, replacing obsolete parameters, verify successful completion) Guide administrators in activating new features ...
... Implement best practices (pre-upgrade database backup, replacing obsolete parameters, verify successful completion) Guide administrators in activating new features ...
(A) R
... and F logically implies (F – { }) {( – A) }. Attribute A is extraneous in if A and the set of functional dependencies (F – { }) { ( – A)} logically implies F. Note: implication in the opposite direction is trivial in each of ...
... and F logically implies (F – { }) {( – A) }. Attribute A is extraneous in if A and the set of functional dependencies (F – { }) { ( – A)} logically implies F. Note: implication in the opposite direction is trivial in each of ...
Advanced SQL
... Program sends SQL commands to database by using SQLExecDirect Result tuples are fetched using SQLFetch() SQLBindCol() binds C language variables to attributes of the query ...
... Program sends SQL commands to database by using SQLExecDirect Result tuples are fetched using SQLFetch() SQLBindCol() binds C language variables to attributes of the query ...
DEVQ400-03 SQL Server 2000 XML Enhancements
... Transforms each row in the result set into an XML element with the generic identifier row Returns query results in a simple, nested XML tree ...
... Transforms each row in the result set into an XML element with the generic identifier row Returns query results in a simple, nested XML tree ...
08_DBApplicationDeve.. - School of Information Technologies
... starts a database transaction (otherwise: autocommit) successfully finishes current transaction aborts current transaction checks whether there's an active transaction ...
... starts a database transaction (otherwise: autocommit) successfully finishes current transaction aborts current transaction checks whether there's an active transaction ...
Document
... Whether you remove duplicate rows from result or not, it is up to you since relations are sets, and could have contained duplicate rows themselves E.g. To eliminate the branch-name attribute of account ...
... Whether you remove duplicate rows from result or not, it is up to you since relations are sets, and could have contained duplicate rows themselves E.g. To eliminate the branch-name attribute of account ...
Oracle Database 12c Global Data Services (Oracle White Paper)
... geographically disparate data centers to meet various business requirements such as high availability, disaster recovery, content localization and caching, scalability, optimal performance for local clients or compliance with local laws. Oracle Active Data Guard and Oracle GoldenGate are the strateg ...
... geographically disparate data centers to meet various business requirements such as high availability, disaster recovery, content localization and caching, scalability, optimal performance for local clients or compliance with local laws. Oracle Active Data Guard and Oracle GoldenGate are the strateg ...
Chapter 14: Query Optimization
... expressions equivalent to the given expression Conceptually, generate all equivalent expressions by repeatedly executing the following step until no more expressions can be found Very expensive in space and time Space requirements reduced by sharing common subexpressions: ...
... expressions equivalent to the given expression Conceptually, generate all equivalent expressions by repeatedly executing the following step until no more expressions can be found Very expensive in space and time Space requirements reduced by sharing common subexpressions: ...
Optimization of Continuous Queries in Federated
... system, however, supports queries that access both streaming data and stored data as well. One major challenge of such systems is to find the optimal execution plan for a given continuous query. Existing federated database and stream processing systems either have no federated optimizer at all [BCD+ ...
... system, however, supports queries that access both streaming data and stored data as well. One major challenge of such systems is to find the optimal execution plan for a given continuous query. Existing federated database and stream processing systems either have no federated optimizer at all [BCD+ ...
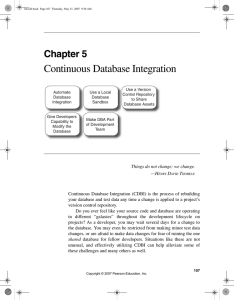
Continuous Database Integration
... local instance of the database on their workstations. Every team member can then create a database “sandbox” to make and test database changes without affecting others. If your database integration is scripted, creating a new database instance is a push-button affair; conversely, if you don’t automa ...
... local instance of the database on their workstations. Every team member can then create a database “sandbox” to make and test database changes without affecting others. If your database integration is scripted, creating a new database instance is a push-button affair; conversely, if you don’t automa ...
Distributed Databases - University of Texas at El Paso
... Database Administration Database Administration Functions: Selection of Hardware and Software Difficult to keep abreast of current technology Difficult to predict future changes Emphasis on established off-the-shelf products ...
... Database Administration Database Administration Functions: Selection of Hardware and Software Difficult to keep abreast of current technology Difficult to predict future changes Emphasis on established off-the-shelf products ...
MySQL Backup and Recovery
... 1.5 Point-in-Time (Incremental) Recovery Using the Binary Log ............................................ 16 1.5.1 Point-in-Time Recovery Using Event Times ......................................................... 17 1.5.2 Point-in-Time Recovery Using Event Positions ............................... ...
... 1.5 Point-in-Time (Incremental) Recovery Using the Binary Log ............................................ 16 1.5.1 Point-in-Time Recovery Using Event Times ......................................................... 17 1.5.2 Point-in-Time Recovery Using Event Positions ............................... ...
Auditing and Inference Control in
... No one proposed protection mechanism is suitable for all SDB's. Protection mechanism 1 is shown to be compromisable [12], and protection mechanism 2 may not be feasible to implement. Mechanism 3 may be overly restrictive and limits the usefulness of the SDB. Mechanism 4, which employs output perturb ...
... No one proposed protection mechanism is suitable for all SDB's. Protection mechanism 1 is shown to be compromisable [12], and protection mechanism 2 may not be feasible to implement. Mechanism 3 may be overly restrictive and limits the usefulness of the SDB. Mechanism 4, which employs output perturb ...