Qt basic programming
... • Items are added to the scene by calling QGraphicsScene::addItem(), and then retrieved by calling one of the many item discovery functions i.e. QGraphicsScene::itemAt() • QGraphicsScene's event propagation architecture schedules scene events for delivery to items, and also manages propagation betwe ...
... • Items are added to the scene by calling QGraphicsScene::addItem(), and then retrieved by calling one of the many item discovery functions i.e. QGraphicsScene::itemAt() • QGraphicsScene's event propagation architecture schedules scene events for delivery to items, and also manages propagation betwe ...
NetIntel: A Database for Manipulation of Rich Social Network Data
... Social network analysis focuses on the relations among and between entities in a social or organizational system. For most of its history, social network analysis has operated on a notion of a dataset - a clearly delimited and pruned set of observations that have been encoded and parameterized using ...
... Social network analysis focuses on the relations among and between entities in a social or organizational system. For most of its history, social network analysis has operated on a notion of a dataset - a clearly delimited and pruned set of observations that have been encoded and parameterized using ...
slides
... • Interleaving actions of different user programs can lead to inconsistency: e.g., check is cleared while account balance is being computed. • DBMS ensures such problems don’t arise: users can pretend they are using a single-user system. CS 4320 ...
... • Interleaving actions of different user programs can lead to inconsistency: e.g., check is cleared while account balance is being computed. • DBMS ensures such problems don’t arise: users can pretend they are using a single-user system. CS 4320 ...
here - AMIS Technology Blog
... • The iterator binding rangesize property represents the current set of objects to be displayed on the page • Rule of thumb: for, and
components set the rangesize to the max number of records that you
can display in the browser, not more (usually not more than 50 ...
... • The iterator binding rangesize property represents the current set of objects to be displayed on the page • Rule of thumb: for
9781133629627_Ch03
... • Multidimensional databases and online analytical processing programs store data and allow users to explore data from a number of ...
... • Multidimensional databases and online analytical processing programs store data and allow users to explore data from a number of ...
Chapter 8 - Spatial Database Group
... accesses and CPU usage, a weight can be used to combine them into one measure. The weight is usually close to 0 because many CPU operations can be performed in the time to perform one physical record ...
... accesses and CPU usage, a weight can be used to combine them into one measure. The weight is usually close to 0 because many CPU operations can be performed in the time to perform one physical record ...
Designing and implementing a data warehouse for
... Picture 2. An example of a BI architecture and the BI process (Super Develop 2014) ...
... Picture 2. An example of a BI architecture and the BI process (Super Develop 2014) ...
- Courses - University of California, Berkeley
... – Physical representation and location of data and the use of that data are separated • The application doesn’t need to know how or where the database has stored the data, but just how to ask for it. • Moving a database from one DBMS to another should not have a material effect on application ...
... – Physical representation and location of data and the use of that data are separated • The application doesn’t need to know how or where the database has stored the data, but just how to ask for it. • Moving a database from one DBMS to another should not have a material effect on application ...
Introduction to SAS/ACCESS Software
... VIEW. They point to information stored in ACCESS descriptors and can specifY a subset of the columns specified in an ACCESS descriptor. They can define different SAS variable names and formats than what is prescribed In the ACCESS descriptor. View descriptors are referenced as if they were a SAS dat ...
... VIEW. They point to information stored in ACCESS descriptors and can specifY a subset of the columns specified in an ACCESS descriptor. They can define different SAS variable names and formats than what is prescribed In the ACCESS descriptor. View descriptors are referenced as if they were a SAS dat ...
IC52C4: Introduction
... Need to know local DBMS query languages, and write applications using functionality provided by the Local DBMS ...
... Need to know local DBMS query languages, and write applications using functionality provided by the Local DBMS ...
Data Modeling - Liberty University
... A generalization hierarchy is a form of abstraction that specifies that two or more entities that share common attributes can be generalized into a higher level entity type called a supertype or generic entity. The lower-level of entities become the subtype, or categories, to the supertype. Subtypes ...
... A generalization hierarchy is a form of abstraction that specifies that two or more entities that share common attributes can be generalized into a higher level entity type called a supertype or generic entity. The lower-level of entities become the subtype, or categories, to the supertype. Subtypes ...
Start_to_Finish_with_Azure_Data_Factory
... 4. Create Datasets: Input and Output 5. Create Pipeline: Define Activities 6. Monitor and Manage: Portal or PowerShell, Alerts and Metrics ...
... 4. Create Datasets: Input and Output 5. Create Pipeline: Define Activities 6. Monitor and Manage: Portal or PowerShell, Alerts and Metrics ...
APPENDIX BB Database Administration Document Template
... Specify any administrative tasks that need to be performed on the database server including scheduled jobs, tuning, replication, data retention, etc. Reminder: Click the show/hide icon on your tool bar to view examples of the required input. ...
... Specify any administrative tasks that need to be performed on the database server including scheduled jobs, tuning, replication, data retention, etc. Reminder: Click the show/hide icon on your tool bar to view examples of the required input. ...
MySQL: Database Design
... Database Design Entity-Relationship Diagram (ERD) is a tool for modeling data. 3 concepts to remember about ERD – Entity - the main object in the problem domain. – Attribute - describes the main object (entity). – Relation - association defines the between entity. ...
... Database Design Entity-Relationship Diagram (ERD) is a tool for modeling data. 3 concepts to remember about ERD – Entity - the main object in the problem domain. – Attribute - describes the main object (entity). – Relation - association defines the between entity. ...
Fault-Tolerance in Real
... Replication Mechanism for Very High Availability, Proceedings of the International Workshop on Databases in Telecommunications II, LNCS ...
... Replication Mechanism for Very High Availability, Proceedings of the International Workshop on Databases in Telecommunications II, LNCS ...
Lecture 3
... Function SUM returns sum of all values from the beginning of the table until current record Records are sorted by name: OVER (order by ...
... Function SUM returns sum of all values from the beginning of the table until current record Records are sorted by name: OVER (order by ...
A 1
... Model data in business environments by drawing entity-relationship diagrams that involve unary, binary, and ternary relationships. Understand the relational data model and relational database constraints ...
... Model data in business environments by drawing entity-relationship diagrams that involve unary, binary, and ternary relationships. Understand the relational data model and relational database constraints ...
AT33264269
... be due to the presence of an auxiliary information, such as a comment, recommendation, or advertisement. While the method in can find all data regions containing at least two QRRs in a query result page using data mining techniques, almost all other data extraction methods, such as, assume that the ...
... be due to the presence of an auxiliary information, such as a comment, recommendation, or advertisement. While the method in can find all data regions containing at least two QRRs in a query result page using data mining techniques, almost all other data extraction methods, such as, assume that the ...
Prototype for Traversing and Browsing Related Data in a Relation
... What we need to see is not only the records that are in our selected table, but also related records from other tables. That would give us more information about the records in the selected table, and we could also assess the correctness of the data in our table and in the related tables. Where nece ...
... What we need to see is not only the records that are in our selected table, but also related records from other tables. That would give us more information about the records in the selected table, and we could also assess the correctness of the data in our table and in the related tables. Where nece ...
Class Summary
... Data Store – Consists of an integrated set of objects that are modeled by classes or feature classes defined within one or more schemas. Data stores can be either file based, such as SHP, or a database, such as Oracle®. Drawing Objects – Objects that exist in a drawing file (DWG) or an attached draw ...
... Data Store – Consists of an integrated set of objects that are modeled by classes or feature classes defined within one or more schemas. Data stores can be either file based, such as SHP, or a database, such as Oracle®. Drawing Objects – Objects that exist in a drawing file (DWG) or an attached draw ...
Chapter 10
... • Some database tables have an identity column – Assigned a unique number by the database – Occurs automatically for identity columns – No need to manually supply a value for this column • Payments table uses an identity column – Omit ID column value – Only supply Member_Id, Payment_Date, and Amount ...
... • Some database tables have an identity column – Assigned a unique number by the database – Occurs automatically for identity columns – No need to manually supply a value for this column • Payments table uses an identity column – Omit ID column value – Only supply Member_Id, Payment_Date, and Amount ...
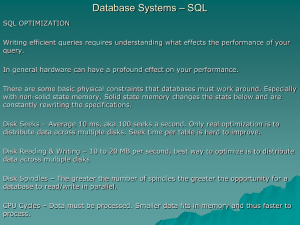
Optimizing SQL
... There isn’t much you can do here other than improving your hardware. Transmission of the data to the client. There isn’t much you can do here other than to minimize the number of columns returned in the result set as well as the number of rows. ...
... There isn’t much you can do here other than improving your hardware. Transmission of the data to the client. There isn’t much you can do here other than to minimize the number of columns returned in the result set as well as the number of rows. ...
Windows Azure SQL Database
... on tables with billions of records Scalable SQL like syntax Google Storage is the persistent mechanism Does not currently support joins Access control only at the level of datasets, not to tables. Anyone with access to a dataset has access to all tables within that dataset ...
... on tables with billions of records Scalable SQL like syntax Google Storage is the persistent mechanism Does not currently support joins Access control only at the level of datasets, not to tables. Anyone with access to a dataset has access to all tables within that dataset ...
dbase
... • Triggers are programs embedded within a table that are automatically invoked by a updates to another table. • Stored procedures are programs embedded within a table that can be called from an application program. ...
... • Triggers are programs embedded within a table that are automatically invoked by a updates to another table. • Stored procedures are programs embedded within a table that can be called from an application program. ...