Zero Downtime with GoldenGate
... Older software versions lacked functionality Ability to provide a robust and reliable service to its customers was at risk Priority 1 and 2 applications demanded little or no downtime ...
... Older software versions lacked functionality Ability to provide a robust and reliable service to its customers was at risk Priority 1 and 2 applications demanded little or no downtime ...
Knowledge Discovery in Databases: An Attribute
... of its attribute values are generalized data, that is, nonleaf nodes in the concept hierarchies. Some leaming-fromexamplesalgorithms require the final learned rule to be in conjunctive normal form [14]. This requirement is usually unreasonablefor large databasessince the generalized data often conta ...
... of its attribute values are generalized data, that is, nonleaf nodes in the concept hierarchies. Some leaming-fromexamplesalgorithms require the final learned rule to be in conjunctive normal form [14]. This requirement is usually unreasonablefor large databasessince the generalized data often conta ...
Document
... large instant-access applications. ■ Instant access is made possible by databases. – Individual database records can be accessed directly without sequentially searching. – Databases have been used in business applications for decades. ...
... large instant-access applications. ■ Instant access is made possible by databases. – Individual database records can be accessed directly without sequentially searching. – Databases have been used in business applications for decades. ...
SYSTEM 2000 Data Management Software Release 12 Enhancements and Why SYSTEM 2000 Software Is the Best Place to Maintain Your Production SAS Data
... SASfACCESS product enables you to view a SYSTEM 2000 database just as you would when using SAS data files. This allows you to write SAS programs that take full advantage of the powers of SYSTEM 2000 software, but at the same time does not require you to learn the DBMS's programming concepts. ...
... SASfACCESS product enables you to view a SYSTEM 2000 database just as you would when using SAS data files. This allows you to write SAS programs that take full advantage of the powers of SYSTEM 2000 software, but at the same time does not require you to learn the DBMS's programming concepts. ...
Database Extract Tool (DeTL)
... Database eXtract Tool (DeTL) is a windows based desktop application those who wants to extract the database table data into flat files. The application will provide a GUI which can configure and extract the table data into files. This is comprehensive tool for all data extract needs from databases. ...
... Database eXtract Tool (DeTL) is a windows based desktop application those who wants to extract the database table data into flat files. The application will provide a GUI which can configure and extract the table data into files. This is comprehensive tool for all data extract needs from databases. ...
SQLIA: Detection And Prevention Techniques: A Survey Pushkar Y.Jane , M.S.Chaudhari
... SQLIA: Detection And Prevention Techniques: A Survey Dynamic Candidate Evaluations Approach - In, Bisht et al. propose CANDID. It is a Dynamic Candidate Evaluations method for automatic prevention of SQL Injection attacks. This framework dynamically extracts the query structures from every SQL quer ...
... SQLIA: Detection And Prevention Techniques: A Survey Dynamic Candidate Evaluations Approach - In, Bisht et al. propose CANDID. It is a Dynamic Candidate Evaluations method for automatic prevention of SQL Injection attacks. This framework dynamically extracts the query structures from every SQL quer ...
I 257: Database Management - Courses
... • A SET is a string object that can have zero or more values, each of which must be chosen from a list of allowed values specified when the table is created. • SET column values that consist of multiple set members are specified with members separated by commas (‘,’) • For example, a column specifie ...
... • A SET is a string object that can have zero or more values, each of which must be chosen from a list of allowed values specified when the table is created. • SET column values that consist of multiple set members are specified with members separated by commas (‘,’) • For example, a column specifie ...
Reading Data
... database. Alternatively you can create a DSN (data source name) for this file, say TransportData, and use the command “DSN=TransportData”. ■”Cost” is the name of the table in the database. Alternatively we can use an SQL command like “SQL=SELECT * FROM Cost” ■ The : is syntax. What follows is the ma ...
... database. Alternatively you can create a DSN (data source name) for this file, say TransportData, and use the command “DSN=TransportData”. ■”Cost” is the name of the table in the database. Alternatively we can use an SQL command like “SQL=SELECT * FROM Cost” ■ The : is syntax. What follows is the ma ...
Database Systems - University of Texas at Dallas
... Explicit Sets and Renaming of Attributes in SQL • Can use explicit set of values in WHERE clause E. g. SELECT * FROM works_on where pno in (1,2,3) • Use qualifier AS followed by desired new name – Rename any attribute that appears in the result of a query – Useful when you have ambiguous names ...
... Explicit Sets and Renaming of Attributes in SQL • Can use explicit set of values in WHERE clause E. g. SELECT * FROM works_on where pno in (1,2,3) • Use qualifier AS followed by desired new name – Rename any attribute that appears in the result of a query – Useful when you have ambiguous names ...
ERC+: an object+relationship paradigm for database applications
... known as the first normal form rule). An object in a relation (a tuple) is a list of atomic values. Composite attributes are not allowed: for instance, it is not possible to specify a date attribute as composed of day, month and year attributes. Multivalued attributes are not allowed: for instance, ...
... known as the first normal form rule). An object in a relation (a tuple) is a list of atomic values. Composite attributes are not allowed: for instance, it is not possible to specify a date attribute as composed of day, month and year attributes. Multivalued attributes are not allowed: for instance, ...
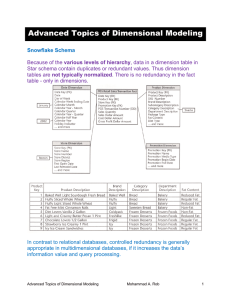
Dimensional Modeling
... seven, or 255,500,000/7 = 36,500,000. This will not be the case due to the sparsity of data, because all stores do not sell the same products on the same day. The number of rows will be (100X15000X52 =) 78,000,000, or double than expected. Measures in the Fact Tables The values that quantify facts a ...
... seven, or 255,500,000/7 = 36,500,000. This will not be the case due to the sparsity of data, because all stores do not sell the same products on the same day. The number of rows will be (100X15000X52 =) 78,000,000, or double than expected. Measures in the Fact Tables The values that quantify facts a ...
Database Design Data Modeling Standards - PA
... Use English words with no abbreviations separated by a space. ...
... Use English words with no abbreviations separated by a space. ...
Efficient, hot & automatic oracle database cloning
... • Cloning large databases can take a long time • Why not just split the amount of objects needed to be copied among different tasks? – For each tablespace: • Create a process for each datafile to be copied until a maximum level of parallelism is reached (_maximum_parallelism_barrier) • Once the maxi ...
... • Cloning large databases can take a long time • Why not just split the amount of objects needed to be copied among different tasks? – For each tablespace: • Create a process for each datafile to be copied until a maximum level of parallelism is reached (_maximum_parallelism_barrier) • Once the maxi ...
Chemical Database of Optimized Molecular Structures
... Generally, database is a dynamic collection of information stored in a certain way. Hence, this information needs constant update. This is the case of MDL ACD database, which is commercial and thus requires constant update. Often the databases are used in conjunction with auxiliary software. For ins ...
... Generally, database is a dynamic collection of information stored in a certain way. Hence, this information needs constant update. This is the case of MDL ACD database, which is commercial and thus requires constant update. Often the databases are used in conjunction with auxiliary software. For ins ...
Chapter 7: Relational Database Design
... which are independent of each other E.g. temporary/permanent is independent of Officer/secretary/teller Create a subclass for each combination of subclasses – Need not create subclasses for combinations that are not possible in the database being modeled A class inherits variables and methods ...
... which are independent of each other E.g. temporary/permanent is independent of Officer/secretary/teller Create a subclass for each combination of subclasses – Need not create subclasses for combinations that are not possible in the database being modeled A class inherits variables and methods ...
Computational Complexity of Semantic Web Language
... • Whenever the complexity for a given problem is described as Open, with a star, (*), it is meant that its decidability is still an open question; if the star (*) is omitted, then the problem is known to be decidable but precise complexity bounds have not yet been established. If a problem is lab ...
... • Whenever the complexity for a given problem is described as Open, with a star, (*), it is meant that its decidability is still an open question; if the star (*) is omitted, then the problem is known to be decidable but precise complexity bounds have not yet been established. If a problem is lab ...
Lecture 6: SQL II - NYU Computer Science
... number of groups in a relation – The number of groups is not known in advance (depends on the relation instance) – Example: Find the age of the youngest sailor for each rating level ...
... number of groups in a relation – The number of groups is not known in advance (depends on the relation instance) – Example: Find the age of the youngest sailor for each rating level ...
ppt - Information Systems
... Spatial and Geographic Databases Spatial databases store information related to spatial ...
... Spatial and Geographic Databases Spatial databases store information related to spatial ...
Profiles, password policies, privileges, and roles
... – Public database role: • Cannot be dropped • Users automatically belong to this role • Users cannot be dropped Database Security & Auditing: Protecting Data Integrity & Accessibility ...
... – Public database role: • Cannot be dropped • Users automatically belong to this role • Users cannot be dropped Database Security & Auditing: Protecting Data Integrity & Accessibility ...
Case sensitivity of column names in SQL Server Importing source
... retrieving data from the SQL Server tables using those column names if the case does not match the way they are defined in SQL Server. SQL Server will allow mixed case for column names, but the Oracle database assumes all uppercase for column names. It is possible to query a mixed-case column name i ...
... retrieving data from the SQL Server tables using those column names if the case does not match the way they are defined in SQL Server. SQL Server will allow mixed case for column names, but the Oracle database assumes all uppercase for column names. It is possible to query a mixed-case column name i ...
Chapter 1
... SQL is the most popular database language and has commands that enable it to be used for both the manipulation and definition of relational databases because of its English-based syntax. Oracle was one of the first companies to release RDBMS software that used an Englishbased structured query langua ...
... SQL is the most popular database language and has commands that enable it to be used for both the manipulation and definition of relational databases because of its English-based syntax. Oracle was one of the first companies to release RDBMS software that used an Englishbased structured query langua ...