Week5 - Information Management and Systems
... Advocated by Ralph Kimball (see his manifesto, and a rebuttal, available on the web site). A logical design technique that seeks to present data in a standard framework that is intuitive and allows for high-performance access. ...
... Advocated by Ralph Kimball (see his manifesto, and a rebuttal, available on the web site). A logical design technique that seeks to present data in a standard framework that is intuitive and allows for high-performance access. ...
detection and prevention of tautology and union query
... In tautology-based attack attacker injects code in one or more conditional statements so that they always evaluate to true. Consider a website‟s page in which SQL query is dynamically created and includes user input fields. The following query is used for fetching information about books: “SELECT * ...
... In tautology-based attack attacker injects code in one or more conditional statements so that they always evaluate to true. Consider a website‟s page in which SQL query is dynamically created and includes user input fields. The following query is used for fetching information about books: “SELECT * ...
File
... Focusing on the modeling and analysis of data for decision makers, not on daily operations or transaction processing Provide a simple and concise view around particular ...
... Focusing on the modeling and analysis of data for decision makers, not on daily operations or transaction processing Provide a simple and concise view around particular ...
The Case For Change Notifications in Pull-Based
... to change notifications. In recent years, new database systems have emerged that aim to provide real-time change notifications in a scalable manner, but they provide only vendor-specific solutions. Existing applications working on a purely pull-based database have to either switch the underlying dat ...
... to change notifications. In recent years, new database systems have emerged that aim to provide real-time change notifications in a scalable manner, but they provide only vendor-specific solutions. Existing applications working on a purely pull-based database have to either switch the underlying dat ...
Dynamic Query Forms for Database Queries
... • Modern scientific databases and web databases maintain large and heterogeneous data. These real-world databases contain over hundreds or even thousands of relations and attributes. Traditional predefined query forms are not able to satisfy various ad-hoc queries from users on those databases. This ...
... • Modern scientific databases and web databases maintain large and heterogeneous data. These real-world databases contain over hundreds or even thousands of relations and attributes. Traditional predefined query forms are not able to satisfy various ad-hoc queries from users on those databases. This ...
Powerpoint - SQL Saturday
... • You can SPLIT a db into multiple. • You can MERGE multiple dbs into one. • These operations allow to respond to changes in capacity needs. • It’s delivered as a customer-hosted Azure service. ...
... • You can SPLIT a db into multiple. • You can MERGE multiple dbs into one. • These operations allow to respond to changes in capacity needs. • It’s delivered as a customer-hosted Azure service. ...
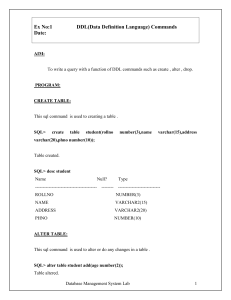
11. Relational Databases and SQL
... – what's the name of the customer that placed order #12351? – we need to join Customers table with Orders table… Select FirstName, LastName From Customers Inner Join Orders On Customers.CID = Orders.CID Where Orders.OID = 12351; ...
... – what's the name of the customer that placed order #12351? – we need to join Customers table with Orders table… Select FirstName, LastName From Customers Inner Join Orders On Customers.CID = Orders.CID Where Orders.OID = 12351; ...
Data Integration and Exchange - Informatics Homepages Server
... ◦ query answering is by no means unique – there could be several ways to answer a query ◦ different possibilities for answering queries are a result of inconsistencies and incomplete information ...
... ◦ query answering is by no means unique – there could be several ways to answer a query ◦ different possibilities for answering queries are a result of inconsistencies and incomplete information ...
BCS THE CHARTERED INSTITUTE FOR IT DATABASE SYSTEMS BCS HIGHER EDUCATION QUALIFICATIONS
... If you add a new item to the table and make a mistake in the description, then you may end up with (e.g.) two different descriptions for the same item. (2 marks) Modification Anomaly If the description of an item changes, and if you neglect to change all the descriptions, then the table will contain ...
... If you add a new item to the table and make a mistake in the description, then you may end up with (e.g.) two different descriptions for the same item. (2 marks) Modification Anomaly If the description of an item changes, and if you neglect to change all the descriptions, then the table will contain ...
PPT - Esri
... • be owned by the user registering the table. • have a single SDO_GEOMETRY column. • have no other columns of a user-defined type. • have a valid entry in the view USER_SDO_GEOM_METADATA. • have a single type of geometry (points, lines, or polygons), can be multipart. ...
... • be owned by the user registering the table. • have a single SDO_GEOMETRY column. • have no other columns of a user-defined type. • have a valid entry in the view USER_SDO_GEOM_METADATA. • have a single type of geometry (points, lines, or polygons), can be multipart. ...
Chapter 3 - Anson
... that is used to manipulate relational databases • Basic form of an SQL query: SELECT-FROMWHERE • Use CREATE TABLE command to describe table layout to the DBMS, which creates the table • In SQL retrieval commands, fields are listed after SELECT, tables are listed after FROM, and conditions are listed ...
... that is used to manipulate relational databases • Basic form of an SQL query: SELECT-FROMWHERE • Use CREATE TABLE command to describe table layout to the DBMS, which creates the table • In SQL retrieval commands, fields are listed after SELECT, tables are listed after FROM, and conditions are listed ...
Chapter 3
... that is used to manipulate relational databases • Basic form of an SQL query: SELECT-FROMWHERE • Use CREATE TABLE command to describe table layout to the DBMS, which creates the table • In SQL retrieval commands, fields are listed after SELECT, tables are listed after FROM, and conditions are listed ...
... that is used to manipulate relational databases • Basic form of an SQL query: SELECT-FROMWHERE • Use CREATE TABLE command to describe table layout to the DBMS, which creates the table • In SQL retrieval commands, fields are listed after SELECT, tables are listed after FROM, and conditions are listed ...
Performance Tuning Microsoft Azure SQL Database
... Defines how often and how many times to retry when a fault is identified as a transient fault Combines a detection strategy and a retry strategy, and is used to call services that might encounter transient ...
... Defines how often and how many times to retry when a fault is identified as a transient fault Combines a detection strategy and a retry strategy, and is used to call services that might encounter transient ...
Distributing near-real time data
... • A widely used metadata standard for atmospheric, ocean, and climate data, based on netCDF • Specifies coordinate systems used in models, data cell properties and methods, packing, standard names for quantities, and grid mappings • CF-aware software can automatically determine spacetime location of ...
... • A widely used metadata standard for atmospheric, ocean, and climate data, based on netCDF • Specifies coordinate systems used in models, data cell properties and methods, packing, standard names for quantities, and grid mappings • CF-aware software can automatically determine spacetime location of ...
The AMBIT database - Generis | Communication Design & Design
... and mining of the data stored in the database. The unique feature of AMBIT is the ability to store multifaceted information about chemical structures and provide a searchable interface linking these diverse components. The AMBIT database: AMBIT database contains over 450 000 chemical compounds with ...
... and mining of the data stored in the database. The unique feature of AMBIT is the ability to store multifaceted information about chemical structures and provide a searchable interface linking these diverse components. The AMBIT database: AMBIT database contains over 450 000 chemical compounds with ...
What are the security issues in database management
... to 20 years on building security solutions for our infrastructure. Almost all of that has gone into network- and perimeter-oriented approaches. We have done some work with operating systems and spam and things like this. But it has really been focused on perimeter- and network-based security soluti ...
... to 20 years on building security solutions for our infrastructure. Almost all of that has gone into network- and perimeter-oriented approaches. We have done some work with operating systems and spam and things like this. But it has really been focused on perimeter- and network-based security soluti ...
Projects: 1. You have given a brand new system. We need to install
... should be deleted automatically. 2. Take on demand backup for user databases on dev databases and restore it on ZAAR server. 3. Setup maintenance plan for indexes. 4. Move one of the development database to test server 5. Move a database using script. You need to include all data as well. 6. What is ...
... should be deleted automatically. 2. Take on demand backup for user databases on dev databases and restore it on ZAAR server. 3. Setup maintenance plan for indexes. 4. Move one of the development database to test server 5. Move a database using script. You need to include all data as well. 6. What is ...
Views-Your Window on Data
... There is some overhead in materializing the data through all these levels. If you wanted to perionn 10 consecutive PROC GCHARTs on this data, it woUld be more efficient to make a copy of the data in a temporary SAS dataset, and then process that data set. This process is oot diffICult, because the ...
... There is some overhead in materializing the data through all these levels. If you wanted to perionn 10 consecutive PROC GCHARTs on this data, it woUld be more efficient to make a copy of the data in a temporary SAS dataset, and then process that data set. This process is oot diffICult, because the ...
pstmt.setInt(1, 100)
... • As we saw last week, some queries can’t be computed in SQL. • PL/pgSQL includes more programming tools than SQL • However, sometimes using PL/pgSQL will not be suitable: – If we require object-oriented programming – If accessing the database is a small part of a large Java application – Etc. • Why ...
... • As we saw last week, some queries can’t be computed in SQL. • PL/pgSQL includes more programming tools than SQL • However, sometimes using PL/pgSQL will not be suitable: – If we require object-oriented programming – If accessing the database is a small part of a large Java application – Etc. • Why ...
Database Management System
... Relational Database: It is a collection of tables / relations. The software required to handle or manipulate these tables or relations is known as Relational Database Management System (RDBMS). Oracle, DB2, Access, MySQL and Visual FoxPro are some commonly used RDBM. Table / Relation: A group of row ...
... Relational Database: It is a collection of tables / relations. The software required to handle or manipulate these tables or relations is known as Relational Database Management System (RDBMS). Oracle, DB2, Access, MySQL and Visual FoxPro are some commonly used RDBM. Table / Relation: A group of row ...
Database Integrity: State of the Art
... and continuously, the database designer depicts consistent states at design time (Codd, 1990). Integrity enforcement efficiency is influenced by the complexity of the assertion set, by the structure of the database repository and by the device that controls and drives database actualizations. Semant ...
... and continuously, the database designer depicts consistent states at design time (Codd, 1990). Integrity enforcement efficiency is influenced by the complexity of the assertion set, by the structure of the database repository and by the device that controls and drives database actualizations. Semant ...
Database Interfaces Under The Version 6 Engine Architecture
... engine concepts 01 Version 6 01 the SAS" System that make data access transparent. Thus lar, we have implemented lour database engines and development is underway on other database engines, so you can see that the engine architecture has bacome a reality. These new interlaces provide much more lunct ...
... engine concepts 01 Version 6 01 the SAS" System that make data access transparent. Thus lar, we have implemented lour database engines and development is underway on other database engines, so you can see that the engine architecture has bacome a reality. These new interlaces provide much more lunct ...
Class 19 - Computer Science, NMSU
... • has no attributes or method code – only signatures • does not have its own objects – only the objects that belong to the interface’s ODMG subclasses • cannot inherit from (be a subclass of) an ODMG class – only from another ODMG interface (in fact, from multiple such interfaces) ...
... • has no attributes or method code – only signatures • does not have its own objects – only the objects that belong to the interface’s ODMG subclasses • cannot inherit from (be a subclass of) an ODMG class – only from another ODMG interface (in fact, from multiple such interfaces) ...