Unstructured Data Management with Oracle Database 12c
... For decades now, Oracle database technology has been used to address the unique problems encountered when managing large volumes of all forms of information. Databases are often used to catalog and reference documents, images and media content stored in files through “pointer-based” implementations. ...
... For decades now, Oracle database technology has been used to address the unique problems encountered when managing large volumes of all forms of information. Databases are often used to catalog and reference documents, images and media content stored in files through “pointer-based” implementations. ...
Query Languages for XML
... IDREFs can be referenced using function id() id() can also be applied to sets of references such as IDREFS and even to strings containing multiple references separated by blanks E.g. /bank-2/account/id(@owner) returns all customers referred to from the owners attribute ...
... IDREFs can be referenced using function id() id() can also be applied to sets of references such as IDREFS and even to strings containing multiple references separated by blanks E.g. /bank-2/account/id(@owner) returns all customers referred to from the owners attribute ...
Designing and implementing a web-based data warehouse solution
... structural form which has been loaded into an OLAP cube running Microsoft SQL Server Analysis Services. Because the analyzed data is read-only within the cube techniques for pre-calculation of results across hierarchical levels of granularity are made possible which has been shown to be very effecti ...
... structural form which has been loaded into an OLAP cube running Microsoft SQL Server Analysis Services. Because the analyzed data is read-only within the cube techniques for pre-calculation of results across hierarchical levels of granularity are made possible which has been shown to be very effecti ...
ZENworks Mobile Management 2.7.x Database Maintenance
... automatically enabled when ZENworks Mobile Management is initially installed. These parameters are recommended for a system accommodating 1,000 devices. Administrators of larger systems should adjust the task parameters according to the recommendations in the best practices guidelines outlined below ...
... automatically enabled when ZENworks Mobile Management is initially installed. These parameters are recommended for a system accommodating 1,000 devices. Administrators of larger systems should adjust the task parameters according to the recommendations in the best practices guidelines outlined below ...
12 SQL
... as a primary key in some other relation. This key is used to enforce referential integrity in RDBMS. Candidate Key: Set of all attributes which can serve as a primary key in a relation. Alternate Key: All the candidate keys other than the primary keys of a relation are alternate keys for a relation. ...
... as a primary key in some other relation. This key is used to enforce referential integrity in RDBMS. Candidate Key: Set of all attributes which can serve as a primary key in a relation. Alternate Key: All the candidate keys other than the primary keys of a relation are alternate keys for a relation. ...
PPT
... $mysqli->query("insert into courses(cid,prof,cred,cap,title) values(362,'agroce',4,70,'SE II')"); $mysqli->query("insert into courses(cid,prof,cred,cap,title) values(496,'cscaffid',4,70,'Mobile/Cloud')"); ...
... $mysqli->query("insert into courses(cid,prof,cred,cap,title) values(362,'agroce',4,70,'SE II')"); $mysqli->query("insert into courses(cid,prof,cred,cap,title) values(496,'cscaffid',4,70,'Mobile/Cloud')"); ...
SQL Server Database Files
... A database page is exactly 8KB (8192-byte) in size, and acts as an individual piece of a database data file. If you have 1 MB worth of data, that data will be stored on 128 separate pages. These 8K pages aren't dedicated just for the data only; the first 96 bytes are used to store information about ...
... A database page is exactly 8KB (8192-byte) in size, and acts as an individual piece of a database data file. If you have 1 MB worth of data, that data will be stored on 128 separate pages. These 8K pages aren't dedicated just for the data only; the first 96 bytes are used to store information about ...
Who Dares Wins – SQL Server Consolidation in the Cloud
... Pooled resources leveraged by many databases Standard elastic pool provides 200-1200* DTUs for up to 100* databases Elastic Standard databases can burst up to 100 DTUs (S3 level) Created/configure pool via portal, PowerShell, REST APIs Move databases in/out using portal, PowerShell, REST APIs, T-SQL ...
... Pooled resources leveraged by many databases Standard elastic pool provides 200-1200* DTUs for up to 100* databases Elastic Standard databases can burst up to 100 DTUs (S3 level) Created/configure pool via portal, PowerShell, REST APIs Move databases in/out using portal, PowerShell, REST APIs, T-SQL ...
3. Elementary and complex transformations
... a meta-model is a formal system of abstract constructs that can be used to describe any situation pertaining to a modeling domain; the notation is an integral part of a meta-model; a model is an artefact made up of instances of constructs of a meta-model, and that specifies the structures of a d ...
... a meta-model is a formal system of abstract constructs that can be used to describe any situation pertaining to a modeling domain; the notation is an integral part of a meta-model; a model is an artefact made up of instances of constructs of a meta-model, and that specifies the structures of a d ...
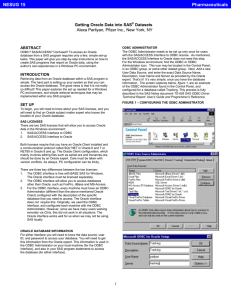
Getting Oracle Data into SAS® Datasets
... For the Windows environment, find the ODBC or ODBC Administrator icon. This icon may be located in the Control Panel, in an ODBC group, or some other related group. Next, Add a new User Data Source, and enter the exact Data Source Name, Description, User Name and Server as provided by the Oracle exp ...
... For the Windows environment, find the ODBC or ODBC Administrator icon. This icon may be located in the Control Panel, in an ODBC group, or some other related group. Next, Add a new User Data Source, and enter the exact Data Source Name, Description, User Name and Server as provided by the Oracle exp ...
Database Administration and Tuning
... optimization, what pitfalls there are, and how the query optimizer can be assisted in its job. Database administrators who know well their data can often influence the optimizer to choose certai ...
... optimization, what pitfalls there are, and how the query optimizer can be assisted in its job. Database administrators who know well their data can often influence the optimizer to choose certai ...
Database Security and Auditing: Leading Practices
... Apply the principle of “least privilege” giving users only the access they need to do their jobs – separation of duties Eliminate weak or default passwords on systems Maintain role-based access controls and disable access after an employee changes positions within a company Formal policies a ...
... Apply the principle of “least privilege” giving users only the access they need to do their jobs – separation of duties Eliminate weak or default passwords on systems Maintain role-based access controls and disable access after an employee changes positions within a company Formal policies a ...
11 Scalability Concepts Every Architect Should Understand
... – Decoupled front/back ends insulate from other system issues if… – Twitter down – Email server unreachable – Order processing partner doing maintenance – Internet connectivity interruption ...
... – Decoupled front/back ends insulate from other system issues if… – Twitter down – Email server unreachable – Order processing partner doing maintenance – Internet connectivity interruption ...
XML Publishing - Computer Science, NMSU
... Database administrator starts by writing an RXL query that defines the XML view of the database. It is called the view query. A materialized view is fed directly into the Plan Generator, which generates a set of SQL queries and one XML template. A virtual view is first composed by the Query Composer ...
... Database administrator starts by writing an RXL query that defines the XML view of the database. It is called the view query. A materialized view is fed directly into the Plan Generator, which generates a set of SQL queries and one XML template. A virtual view is first composed by the Query Composer ...
CODESOFT Tutorial
... databases. The software comes with several ODBC drivers. These enable you to access the most common types of databases. Some of the more common drivers are listed below: ...
... databases. The software comes with several ODBC drivers. These enable you to access the most common types of databases. Some of the more common drivers are listed below: ...
Foundations of Probabilistic Answers to Queries
... Quality in Data Integration Types of imprecision addressed Overlapping, inconsistent, incomplete data sources • Data is probabilistic • Query answers are probabilistic They use already a probabilistic model • Needed: complex probabilistic spaces. E.g. a tuple t in V1 has 60% probability of also bein ...
... Quality in Data Integration Types of imprecision addressed Overlapping, inconsistent, incomplete data sources • Data is probabilistic • Query answers are probabilistic They use already a probabilistic model • Needed: complex probabilistic spaces. E.g. a tuple t in V1 has 60% probability of also bein ...
Using Data Access Objects (DAO)
... Using Active Objects (ADO) First convert your database to Access 97 by using Tools Database Utilities Convert Database To Access 97 Format. Next, start a Standard EXE project and ensure that in Project References you have Microsoft DAO 3.6 Object Library selected and pushed as far up as it w ...
... Using Active Objects (ADO) First convert your database to Access 97 by using Tools Database Utilities Convert Database To Access 97 Format. Next, start a Standard EXE project and ensure that in Project References you have Microsoft DAO 3.6 Object Library selected and pushed as far up as it w ...
reldes
... in greater detail in the remaining sections of this paper. Step One: Determine the purpose of your database. This will help you decide which facts you want Microsoft Access to store. Step Two: Determine the tables you need. Once you have a clear purpose for your database, you can divide your informa ...
... in greater detail in the remaining sections of this paper. Step One: Determine the purpose of your database. This will help you decide which facts you want Microsoft Access to store. Step Two: Determine the tables you need. Once you have a clear purpose for your database, you can divide your informa ...
Tutorial - Teklynx
... databases. The software comes with several ODBC drivers. These enable you to access the most common types of databases. Some of the more common drivers are listed below: ...
... databases. The software comes with several ODBC drivers. These enable you to access the most common types of databases. Some of the more common drivers are listed below: ...
Access Pattern Confidentiality-Preserving - CEUR
... last few years which have put a focus on ORAM to be a considerable alternative when it comes to secure data outsourcing [5, 9, 13, 4, 15], i.e., storing and retrieving data records based on fixed identifiers. Outsourced relational databases, on the other hand, are more complex and require efficient ...
... last few years which have put a focus on ORAM to be a considerable alternative when it comes to secure data outsourcing [5, 9, 13, 4, 15], i.e., storing and retrieving data records based on fixed identifiers. Outsourced relational databases, on the other hand, are more complex and require efficient ...