Three dimensions of information protection and monitoring
... • Content not protected or encrypted • Once content is stolen, no control over content • Uncontrolled distribution of content is on-going… • Repercussions are on-going… ...
... • Content not protected or encrypted • Once content is stolen, no control over content • Uncontrolled distribution of content is on-going… • Repercussions are on-going… ...
Here is the Original File
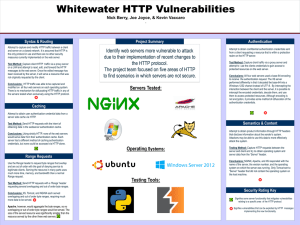
... server and client and try to obtain operating system and server data from the “Server” header. Conclusions: NGINX, Apache, and IIS responded with the name of the server, the version number, and the operating system on which the server was running. Only Tomcat sent a “Server” header that did not cont ...
... server and client and try to obtain operating system and server data from the “Server” header. Conclusions: NGINX, Apache, and IIS responded with the name of the server, the version number, and the operating system on which the server was running. Only Tomcat sent a “Server” header that did not cont ...
Secure Network Infrastructure
... optional and not often used Many application protocols incorporate their own client authentication mechanism such as username/password or S/Key These authentication mechanisms are more secure when run over SSL ...
... optional and not often used Many application protocols incorporate their own client authentication mechanism such as username/password or S/Key These authentication mechanisms are more secure when run over SSL ...
Computer Network Security Protocols and Standards
... there are some differences in design goals, implementation, and acceptance. – First S-HTTP was designed to work with only web protocols. Because SSL is at a lower level in the network stack than S-HTTP, it can work in many other network protocols. – Secondly, in terms of implementation, since SSL is ...
... there are some differences in design goals, implementation, and acceptance. – First S-HTTP was designed to work with only web protocols. Because SSL is at a lower level in the network stack than S-HTTP, it can work in many other network protocols. – Secondly, in terms of implementation, since SSL is ...
Q10 Study Guide - FSU Computer Science
... b. It does not support the dynamic loading of untrusted classes over a network. c. It does not support the execution of mutually distrusting classes within the same JVM. d. Methods in the calling sequence are not responsible for requests to access a protected resource. ...
... b. It does not support the dynamic loading of untrusted classes over a network. c. It does not support the execution of mutually distrusting classes within the same JVM. d. Methods in the calling sequence are not responsible for requests to access a protected resource. ...
WiHawk
... Allows a free access to many hosts on the Internet. Allows various remote commands like: Remote access to root shell of routers File copy ...
... Allows a free access to many hosts on the Internet. Allows various remote commands like: Remote access to root shell of routers File copy ...
Security Signaling During Handovers
... • Handover techniques that assume concurrent radio usage cannot be used • Even for dual-radio devices it might make sense to reduce the security-related signaling, as it decreases the time that both radios need to be active and thus can increase battery life • In addition, handovers between networks ...
... • Handover techniques that assume concurrent radio usage cannot be used • Even for dual-radio devices it might make sense to reduce the security-related signaling, as it decreases the time that both radios need to be active and thus can increase battery life • In addition, handovers between networks ...
Chapter 08
... the Secure Sockets Layer (SSL) protocol to allow secure ecommerce transactions Kerberos provides a network-wide user and service authentication scheme to limit network access to authorized ...
... the Secure Sockets Layer (SSL) protocol to allow secure ecommerce transactions Kerberos provides a network-wide user and service authentication scheme to limit network access to authorized ...
Data Frame Control (2) - Community College of Rhode Island
... Wireless Connection Process • Authentication is the process used by a station to verify that another station is approved for communications. This is a station authentication and not a user authentication. • Authentication Step – Two IEEE 802.11 standards: • Open System Authentication • Shared Key A ...
... Wireless Connection Process • Authentication is the process used by a station to verify that another station is approved for communications. This is a station authentication and not a user authentication. • Authentication Step – Two IEEE 802.11 standards: • Open System Authentication • Shared Key A ...
Security Features in Windows CE
... inside a database volume does not give it any additional security. Therefore, this feature is most useful in databases that are stored within the object store. Removing the system file attribute from a database volume that contains a system database will expose that database to access by untrusted a ...
... inside a database volume does not give it any additional security. Therefore, this feature is most useful in databases that are stored within the object store. Removing the system file attribute from a database volume that contains a system database will expose that database to access by untrusted a ...
Ch10aProtectionMechanisms
... • The security manager must be able to see the organization’s systems and networks from the viewpoint of potential attackers • Drawbacks: – Tools do not have human-level capabilities – Most tools function by pattern recognition, so they only handle known issues – Some governments, agencies, institut ...
... • The security manager must be able to see the organization’s systems and networks from the viewpoint of potential attackers • Drawbacks: – Tools do not have human-level capabilities – Most tools function by pattern recognition, so they only handle known issues – Some governments, agencies, institut ...
authentication
... Newer version sends hash value (key). • Hash value visible over network. • Can be re-used to authenticate. ...
... Newer version sends hash value (key). • Hash value visible over network. • Can be re-used to authenticate. ...
CS 494/594 Computer and Network Security - UTK-EECS
... - prevention: password, encryption, digital signature, access control, authentication, data integrity, firewall - detection: monitoring, log, auditing, intrusion detection - recovery: backups, bug fixes, retaliation ...
... - prevention: password, encryption, digital signature, access control, authentication, data integrity, firewall - detection: monitoring, log, auditing, intrusion detection - recovery: backups, bug fixes, retaliation ...
CS 494/594 Computer and Network Security - UTK-EECS
... - prevention: password, encryption, digital signature, access control, authentication, data integrity, firewall - detection: monitoring, log, auditing, intrusion detection - recovery: backups, bug fixes, retaliation ...
... - prevention: password, encryption, digital signature, access control, authentication, data integrity, firewall - detection: monitoring, log, auditing, intrusion detection - recovery: backups, bug fixes, retaliation ...
Security in Wireless LANs
... The frequency band and transceiver power has a great effect on the range where the transmission can be heard ...
... The frequency band and transceiver power has a great effect on the range where the transmission can be heard ...
Top-Ten Web Security Vulnerabilities
... Our products should emphasize security right out of the box” Bill Gates ...
... Our products should emphasize security right out of the box” Bill Gates ...
Lock down security exposures in your Domino web
... • User submits cookie after initial authentication • With each reply, server sends user an updated cookie – Maintains transaction state this way ...
... • User submits cookie after initial authentication • With each reply, server sends user an updated cookie – Maintains transaction state this way ...
Three challenges with secret key encryption
... Step4: The user types this response and sends it to the Authentication server. While the user is obtaining a response from the token, the Authentication server calculates what the appropriate response should be based on its database of user keys. Step5: When the server receives the user’s response, ...
... Step4: The user types this response and sends it to the Authentication server. While the user is obtaining a response from the token, the Authentication server calculates what the appropriate response should be based on its database of user keys. Step5: When the server receives the user’s response, ...
Network Access Security – It`s Broke, Now What?
... Client Broker "Middleware" that runs on the client and talks to the Posture Collectors, collecting their data, and passing it down to Network Access Requestor. In product form, this is generally bundled with the Network Access Requestor. ...
... Client Broker "Middleware" that runs on the client and talks to the Posture Collectors, collecting their data, and passing it down to Network Access Requestor. In product form, this is generally bundled with the Network Access Requestor. ...
Protection in General-Purpose Operating Systems
... Based on known crypto and hashing methods Users are issued a certificate to prove their identity Certificate is signed by a trusted third-party Biometric Bio: life; Metric: measure Uses body properties to authenticate a user • Fingerprint • Retina and iris scan • DNA? Biometric data is ...
... Based on known crypto and hashing methods Users are issued a certificate to prove their identity Certificate is signed by a trusted third-party Biometric Bio: life; Metric: measure Uses body properties to authenticate a user • Fingerprint • Retina and iris scan • DNA? Biometric data is ...
Security Risks
... – Most popular private key encryption – IBM developed (1970s) – 56-bit key: secure at the time ...
... – Most popular private key encryption – IBM developed (1970s) – 56-bit key: secure at the time ...
Database Security
... • Even if all queries are required to involve count, sum or average, user can use conditions in WHERE line to narrow the population down to one individual • System can refuse any query for which only one record satisfies the predicate-not sufficient protection • Can restrict queries – Require that t ...
... • Even if all queries are required to involve count, sum or average, user can use conditions in WHERE line to narrow the population down to one individual • System can refuse any query for which only one record satisfies the predicate-not sufficient protection • Can restrict queries – Require that t ...
Authentication
.png?width=300)
Authentication (from Greek: αὐθεντικός authentikos, ""real, genuine,"" from αὐθέντης authentes, ""author"") is the act of confirming the truth of an attribute of a single piece of data (a datum) claimed true by an entity. In contrast with identification which refers to the act of stating or otherwise indicating a claim purportedly attesting to a person or thing's identity, authentication is the process of actually confirming that identity. It might involve confirming the identity of a person by validating their identity documents, verifying the validity of a Website with a digital certificate, tracing the age of an artifact by carbon dating, or ensuring that a product is what its packaging and labeling claim to be. In other words, authentication often involves verifying the validity of at least one form of identification.