TS 124 229 - V14.3.1
... The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorizati ...
... The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorizati ...
ETSI TS 1 124 229 V8.34.0
... The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorizati ...
... The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorizati ...
CableLabs Specification:
... liability of any nature whatsoever resulting from or arising out of use or reliance upon this document by any party. This document is furnished on an AS-IS basis and neither CableLabs, nor other participating entity, provides any representation or warranty, express or implied, regarding its accuracy ...
... liability of any nature whatsoever resulting from or arising out of use or reliance upon this document by any party. This document is furnished on an AS-IS basis and neither CableLabs, nor other participating entity, provides any representation or warranty, express or implied, regarding its accuracy ...
29165-e10
... Technical Specification Group Core Network and Terminals; Inter-IMS Network to Network Interface (NNI) (Release 14) ...
... Technical Specification Group Core Network and Terminals; Inter-IMS Network to Network Interface (NNI) (Release 14) ...
HP MSR900 Series
... lists, and aggregate policies Security Access control list (ACL): supports powerful ACLs for both IPv4 and IPv6; ACLs are used for filtering traffic to prevent unauthorized users from accessing the network, or for controlling network traffic to save resources; rules can either deny or permit traffic ...
... lists, and aggregate policies Security Access control list (ACL): supports powerful ACLs for both IPv4 and IPv6; ACLs are used for filtering traffic to prevent unauthorized users from accessing the network, or for controlling network traffic to save resources; rules can either deny or permit traffic ...
MSG(13)034xxx Pseudo CHANGE REQUEST 124 229 Version 11.9
... and "urn:service:sos.ecall.manual") that are introduced in draft-gellens-ecritecall-01 and a related draft-ietf-ecrit-additional-data-15. 3GPP needs to consider the IETF drafts in the dependency list and ensure IANA registration for the URNs. The MSD is sent by the UE to the PSAP. The UE shall inser ...
... and "urn:service:sos.ecall.manual") that are introduced in draft-gellens-ecritecall-01 and a related draft-ietf-ecrit-additional-data-15. 3GPP needs to consider the IETF drafts in the dependency list and ensure IANA registration for the URNs. The MSD is sent by the UE to the PSAP. The UE shall inser ...
- Lovin Varghese
... JMS Header Fields • JMSDestination :The JMSDestination header field contains the destination to which the message is being sent. • JMSDeliveryMode : The JMSDeliveryMode header field contains the delivery mode specified when the message was sent. JMS supports two modes of message ...
... JMS Header Fields • JMSDestination :The JMSDestination header field contains the destination to which the message is being sent. • JMSDeliveryMode : The JMSDeliveryMode header field contains the delivery mode specified when the message was sent. JMS supports two modes of message ...
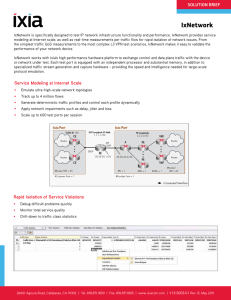
IxNetwork
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
SpamTitan Administrator Guide
... services to produce a mail firewall appliance that eliminates spam and viruses and enforces corporate email policy. Anti-Spam defences on the appliance ensure through a multi-layered approach that over 99% of all spam is detected. Anti-Virus protection is provided through the use of two industry lea ...
... services to produce a mail firewall appliance that eliminates spam and viruses and enforces corporate email policy. Anti-Spam defences on the appliance ensure through a multi-layered approach that over 99% of all spam is detected. Anti-Virus protection is provided through the use of two industry lea ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... As the sub product of electronic mail services, spam became a serious issue in penetrating into any mail system and this types of penetration is mainly used by hackers for stealing confidential data without the knowledge of the user. Generally few hackers use worm which is standalone malware compute ...
... As the sub product of electronic mail services, spam became a serious issue in penetrating into any mail system and this types of penetration is mainly used by hackers for stealing confidential data without the knowledge of the user. Generally few hackers use worm which is standalone malware compute ...
American Messaging Services Network Interface Guide
... be a hostile environment for sending critical information. Therefore, American Messaging Services does not recommend using SMTP for critical message delivery. Sending a message through e-mail may be an acceptable solution, however, if ease of use or rapid implementation outweigh potential Internet a ...
... be a hostile environment for sending critical information. Therefore, American Messaging Services does not recommend using SMTP for critical message delivery. Sending a message through e-mail may be an acceptable solution, however, if ease of use or rapid implementation outweigh potential Internet a ...
Week9b - Personal.psu.edu
... data storage and server data storage • Identify the components of e-mail headers • Understand the flow of instant messaging across the network ...
... data storage and server data storage • Identify the components of e-mail headers • Understand the flow of instant messaging across the network ...
Fact sheet A: Internet Service Providers` Efforts to Curb E
... c) Co-operate with each other to address subscriber’s feedback, for example, tracing the source of the spam e-mail, warning subscribers who send spam mail and taking appropriate actions against such subscribers. d) Implement certain technical measures to manage the spam problem. e) Make available to ...
... c) Co-operate with each other to address subscriber’s feedback, for example, tracing the source of the spam e-mail, warning subscribers who send spam mail and taking appropriate actions against such subscribers. d) Implement certain technical measures to manage the spam problem. e) Make available to ...
Ch.8 Error And Control Messages (ICMP)
... – IP header checksum to detect transmission errors – Error reporting mechanism to distinguish between events such as lost datagrams and incorrect addresses – Higher level protocols (i.e., TCP) must handle all other problems ...
... – IP header checksum to detect transmission errors – Error reporting mechanism to distinguish between events such as lost datagrams and incorrect addresses – Higher level protocols (i.e., TCP) must handle all other problems ...
Step 5 - Ning.com
... The S-CSCF determines the network operator to whom the destination subscriber belongs. Using a DNS query, it determines the address of the I-CSCF in charge of the destination network. Charging parameters P-CSCF address & S-CSCF address (record-route) Public user identity (From) Destination subscribe ...
... The S-CSCF determines the network operator to whom the destination subscriber belongs. Using a DNS query, it determines the address of the I-CSCF in charge of the destination network. Charging parameters P-CSCF address & S-CSCF address (record-route) Public user identity (From) Destination subscribe ...
Internet Control Message Protocol
... As you have seen today and over the last two days, many problems can occur in routing a message from sender to receiver. The TTL timer might expire; fragmented datagrams might not arrive with all segments intact; a gateway might misroute a datagram, and so on. Letting the sending device know of a pr ...
... As you have seen today and over the last two days, many problems can occur in routing a message from sender to receiver. The TTL timer might expire; fragmented datagrams might not arrive with all segments intact; a gateway might misroute a datagram, and so on. Letting the sending device know of a pr ...
$doc.title
... – Detects changes made to mailbox by other clients – Server keeps message state (e.g., read, replied to) ...
... – Detects changes made to mailbox by other clients – Server keeps message state (e.g., read, replied to) ...
Delay Tolerant Networks (and email)
... • Many similariVes to (abstract) e‐mail service • Primary difference involves rouVng, reliability and security • E‐mail depends on an underlying layer’s rouVng – Cannot generally move messages ‘closer’ to their desVnaVons in a parVVoned network – E‐mail protocols are not disconnecVon‐tolerant o ...
... • Many similariVes to (abstract) e‐mail service • Primary difference involves rouVng, reliability and security • E‐mail depends on an underlying layer’s rouVng – Cannot generally move messages ‘closer’ to their desVnaVons in a parVVoned network – E‐mail protocols are not disconnecVon‐tolerant o ...
ppt
... • Many similarities to (abstract) e-mail service • Primary difference involves routing, reliability and security • E-mail depends on an underlying layer’s routing – Cannot generally move messages ‘closer’ to their destinations in a partitioned network – E-mail protocols are not disconnection-toleran ...
... • Many similarities to (abstract) e-mail service • Primary difference involves routing, reliability and security • E-mail depends on an underlying layer’s routing – Cannot generally move messages ‘closer’ to their destinations in a partitioned network – E-mail protocols are not disconnection-toleran ...
Delay/Disruption Tolerant Networks
... • Additional headers to describe the message body – MIME-Version: the version of MIME being used – Content-Type: the type of data contained in the message – Content-Transfer-Encoding: how the data are encoded ...
... • Additional headers to describe the message body – MIME-Version: the version of MIME being used – Content-Type: the type of data contained in the message – Content-Transfer-Encoding: how the data are encoded ...
Electronic Mail
... • Leading to a need to explicitly define a protocol – Types of messages (e.g., requests and responses) – Message syntax (e.g., fields, and how to delineate) – Semantics of the fields (i.e., meaning of the information) – Rules for when and how a process sends messages ...
... • Leading to a need to explicitly define a protocol – Types of messages (e.g., requests and responses) – Message syntax (e.g., fields, and how to delineate) – Semantics of the fields (i.e., meaning of the information) – Rules for when and how a process sends messages ...
The Mathematics Behind the Birthday Attack
... I have presented to you how message integrity is maintained in a nutshell (actually the above is a very basic model and there is more but delving too deep into different types of Message Authentication Codes would be a digression). An important concept here is that when a tag is generated, it involve ...
... I have presented to you how message integrity is maintained in a nutshell (actually the above is a very basic model and there is more but delving too deep into different types of Message Authentication Codes would be a digression). An important concept here is that when a tag is generated, it involve ...
download
... • Most heavily used application on any network • Simple Mail Transfer Protocol (SMTP) – TCP/IP – Delivery of simple text messages • Multi-purpose Internet Mail Extension (MIME) – Delivery of other types of data – Voice, images, video clips ...
... • Most heavily used application on any network • Simple Mail Transfer Protocol (SMTP) – TCP/IP – Delivery of simple text messages • Multi-purpose Internet Mail Extension (MIME) – Delivery of other types of data – Voice, images, video clips ...
Database Techniques for fight SPAM
... Determine site responsible for entry and send UDP. Once received by owner site, forward entry to k peers using TCP. Updates communicative, order doesn’t matter. Consistency not required. Even if host goes down, database can be rebuilt in an hour. ...
... Determine site responsible for entry and send UDP. Once received by owner site, forward entry to k peers using TCP. Updates communicative, order doesn’t matter. Consistency not required. Even if host goes down, database can be rebuilt in an hour. ...