Operating System Security (II)
... • UNIX systems distinguish between uppercase and lowercase, MS-DOS and Windows do not • many systems support two-part, period-separated naming: the second part is called the extension • in UNIX, the extension is a user convention; not enforced • Windows is extension-aware and associates files with s ...
... • UNIX systems distinguish between uppercase and lowercase, MS-DOS and Windows do not • many systems support two-part, period-separated naming: the second part is called the extension • in UNIX, the extension is a user convention; not enforced • Windows is extension-aware and associates files with s ...
Test Plan - Rose
... Verify ALUResult Output when using 8-bit BSrc mux. input values for SE Input. Set BSrc to the appropriate mux input. Connect the Register File module to the ALU. Connect A and B. ReadData1 A ASrc Mux ReadData2 B BSrc Mux Do Not Connect ALUOut to WriteData yet Add the mux for the Register Fil ...
... Verify ALUResult Output when using 8-bit BSrc mux. input values for SE Input. Set BSrc to the appropriate mux input. Connect the Register File module to the ALU. Connect A and B. ReadData1 A ASrc Mux ReadData2 B BSrc Mux Do Not Connect ALUOut to WriteData yet Add the mux for the Register Fil ...
File Systems - Personal Web Pages
... Files are identified by their characteristics, - type of file, - topic, - author, - or metadata. ...
... Files are identified by their characteristics, - type of file, - topic, - author, - or metadata. ...
Initiates file download
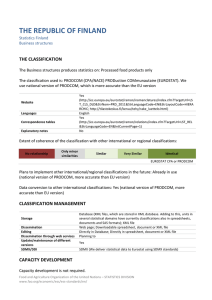
... Data conversion to other international classifications: Yes (national version of PRODCOM, more accurate than EU version) ...
... Data conversion to other international classifications: Yes (national version of PRODCOM, more accurate than EU version) ...
chapter4
... CPU access to RAM to perform a computation using the data in RAM. 2) Secondary or “hard disk” access time is slower in several orders of magnitude than RAM, but stores large volume of records. Retain contents without power. Dataset of a database cannot be fitted into main memory, forcing the data to ...
... CPU access to RAM to perform a computation using the data in RAM. 2) Secondary or “hard disk” access time is slower in several orders of magnitude than RAM, but stores large volume of records. Retain contents without power. Dataset of a database cannot be fitted into main memory, forcing the data to ...
Comparing and Contrasting Windows and Linux Forensics Zlatko
... account. In order to connect the user with the administrative action performed, logging is essential. Also, in Windows one user can access one application, while in Linux several users can access one application. In both Operating Systems file system is hierarchical, but as Volonino states, another ...
... account. In order to connect the user with the administrative action performed, logging is essential. Also, in Windows one user can access one application, while in Linux several users can access one application. In both Operating Systems file system is hierarchical, but as Volonino states, another ...
File Processing
... address pointers Links generated when data is entered Efficient but not flexible Ad hoc design Query dependent on specific DBMS (may support SQL) ...
... address pointers Links generated when data is entered Efficient but not flexible Ad hoc design Query dependent on specific DBMS (may support SQL) ...
Disk Attachment
... NAS systems contain one or more hard disks, often arranged into logical, redundant storage containers or RAID arrays. ...
... NAS systems contain one or more hard disks, often arranged into logical, redundant storage containers or RAID arrays. ...
ch11.pdf
... 2. Creating data structures and algorithms to map the logical file system onto the physical secondary storage device. ...
... 2. Creating data structures and algorithms to map the logical file system onto the physical secondary storage device. ...
What Is File Fragmentation?
... occurs in PC’s once they have been in operation for a year or so and can be even more of a problem if you're working with lots of data every day. File processing is very easy and takes little time at all if the file being searched for is located in one spot in your hard-disc, but when the file is fr ...
... occurs in PC’s once they have been in operation for a year or so and can be even more of a problem if you're working with lots of data every day. File processing is very easy and takes little time at all if the file being searched for is located in one spot in your hard-disc, but when the file is fr ...
File Systems - Dickinson College
... File Structure: One for each file or directory that is opened by a process. Open File ID Table: An array of pointers to all of the Open File Structures. One for the entire system. Open File Structure: One for each file or directory that is open. File Descriptor: One for every file or dire ...
... File Structure: One for each file or directory that is opened by a process. Open File ID Table: An array of pointers to all of the Open File Structures. One for the entire system. Open File Structure: One for each file or directory that is open. File Descriptor: One for every file or dire ...
sequential file - KCPE-KCSE
... Changes in the structure of the database do not affect programming that accesses other parts of the database. This is called Data Independence from the program. Eg Adding a new field called Gender to the Borrower table doesn’t mean you have to reprogram the Loans Report. (You would have to do this o ...
... Changes in the structure of the database do not affect programming that accesses other parts of the database. This is called Data Independence from the program. Eg Adding a new field called Gender to the Borrower table doesn’t mean you have to reprogram the Loans Report. (You would have to do this o ...
PowerPoint
... To connect PHP to a database, use mysql_connect, which can have three parameters: • Host (default is localhost) • Username (default is the username of the PHP script) • Password (default is blank, which works if the database does not require a password) ...
... To connect PHP to a database, use mysql_connect, which can have three parameters: • Host (default is localhost) • Username (default is the username of the PHP script) • Password (default is blank, which works if the database does not require a password) ...
File-System
... Sharing of files on multi-user systems is desirable Sharing may be done through a protection ...
... Sharing of files on multi-user systems is desirable Sharing may be done through a protection ...
File Systems and File Sharing
... time.Unix Semantics is most desirable because it is easy to serialize all read/write requests but is difficult to implement in a distributed file system. In Session Semantics, all changes made to a file during a session (A Series of file accesses made between the open and close operations) are initi ...
... time.Unix Semantics is most desirable because it is easy to serialize all read/write requests but is difficult to implement in a distributed file system. In Session Semantics, all changes made to a file during a session (A Series of file accesses made between the open and close operations) are initi ...
Database Size
... backup. If there is insufficient space on the hard drive where Jim2 is stored, this backup will fail. An easy check is to view the file size of the backup file – if it is 1KB, the backup file is probably incomplete. On a regular basis, check your backups by restoring the most recent backup to a Jim2 ...
... backup. If there is insufficient space on the hard drive where Jim2 is stored, this backup will fail. An easy check is to view the file size of the backup file – if it is 1KB, the backup file is probably incomplete. On a regular basis, check your backups by restoring the most recent backup to a Jim2 ...
CRSP SuRvivoR-biaS-fRee uS mutual fund databaSe April 2013 quArterly updAte
... The holdings file in the Mutual Funds database hit a milestone this month in exceeding 4 GB in size. As a result, CRSP provides a new ZIP install of the database that can more easily handle large files than the previously used InstallAnywhere process. While introduced sooner than planned, the plan t ...
... The holdings file in the Mutual Funds database hit a milestone this month in exceeding 4 GB in size. As a result, CRSP provides a new ZIP install of the database that can more easily handle large files than the previously used InstallAnywhere process. While introduced sooner than planned, the plan t ...
Distributed File Systems – 1
... – NFSv4: introduced in 2003 • Version 4 made significant changes ...
... – NFSv4: introduced in 2003 • Version 4 made significant changes ...
eDiscovery, the jargon explained.
... eDiscovery, the jargon explained. In the day-to-day operations of eDiscovery we use terms that may well be new to many, so to assist with our communications between new, existing and prospective client’s we have created this glossary of electronic discovery terms, set out in alphabetical order, with ...
... eDiscovery, the jargon explained. In the day-to-day operations of eDiscovery we use terms that may well be new to many, so to assist with our communications between new, existing and prospective client’s we have created this glossary of electronic discovery terms, set out in alphabetical order, with ...
File Systems - Computer Science Department
... • Multiple concurrent accesses are possible. If two I/O operations start at about the same time, serial access is enforced to make sure data is consistent. That is, one operation is performed in its entirety before the next one begins. • However, a read from user 1, followed by a write from user 2, ...
... • Multiple concurrent accesses are possible. If two I/O operations start at about the same time, serial access is enforced to make sure data is consistent. That is, one operation is performed in its entirety before the next one begins. • However, a read from user 1, followed by a write from user 2, ...
Section 17 - Dist. File Sys
... smaller pieces; this leads to considerable efficiency for the network. 3. Disk accesses can be better optimized on the server if it's understood that requests are always for large contiguous chunks. 4. Cache consistency is the major problem with caching. When there are infrequent writes, caching is ...
... smaller pieces; this leads to considerable efficiency for the network. 3. Disk accesses can be better optimized on the server if it's understood that requests are always for large contiguous chunks. 4. Cache consistency is the major problem with caching. When there are infrequent writes, caching is ...
Cyfin Datasheet - Wavecrest Computing
... and many more. Our built-in syslog server can manage the syslog data from your syslog-enabled devices. ...
... and many more. Our built-in syslog server can manage the syslog data from your syslog-enabled devices. ...
Record Locking
... ODBC and Access Record Locking When you edit data in a linked SQL database table using ODBC, Microsoft Access doesn't lock records; instead, the rules of that SQL database govern locking. In this instance, regardless of the record-locking setting you choose for your database, Microsoft Access alway ...
... ODBC and Access Record Locking When you edit data in a linked SQL database table using ODBC, Microsoft Access doesn't lock records; instead, the rules of that SQL database govern locking. In this instance, regardless of the record-locking setting you choose for your database, Microsoft Access alway ...