blue
... Goals • To modify libnids - add a packet dispatch mechanism • Let libnids can analyze and reassemble packets which already received • Memory can be released normally • Packet header informations delivered to AP layer ...
... Goals • To modify libnids - add a packet dispatch mechanism • Let libnids can analyze and reassemble packets which already received • Memory can be released normally • Packet header informations delivered to AP layer ...
ICMP
... ICMP provides a feedback mechanism when an IP message is sent. In this example, device A sends an IP datagram to device B. When it gets to router R3 a problem of some sort is detected, dropping the datagram. R3 sends an ICMP message back to A to tell it that something happened, hopefully with enough ...
... ICMP provides a feedback mechanism when an IP message is sent. In this example, device A sends an IP datagram to device B. When it gets to router R3 a problem of some sort is detected, dropping the datagram. R3 sends an ICMP message back to A to tell it that something happened, hopefully with enough ...
contents - Dialup USA
... Except to the extent expressly permitted by this Agreement or by the laws of the jurisdiction where you acquired the Software, you may not use, copy or modify the Software. Nor may you sub-license any of your rights under this Agreement. You may use the software for your personal use only, and not f ...
... Except to the extent expressly permitted by this Agreement or by the laws of the jurisdiction where you acquired the Software, you may not use, copy or modify the Software. Nor may you sub-license any of your rights under this Agreement. You may use the software for your personal use only, and not f ...
5_atm
... 2. Traffic control mechanisms (enforcement of contract) Connection Admission Control (CAC): the network decides if a connection request can be accepted Usage Parameter Control (UPC): the network detects violations of negotiated parameters and takes appropriate action (e.g. cell discarding or cell ta ...
... 2. Traffic control mechanisms (enforcement of contract) Connection Admission Control (CAC): the network decides if a connection request can be accepted Usage Parameter Control (UPC): the network detects violations of negotiated parameters and takes appropriate action (e.g. cell discarding or cell ta ...
Implementation of the Gnutella protocol in Python
... As the 0.6 specification says (section 2.1) [5], the details for how to accept connection requests, as well as how to select what other Gnutella hosts to connect to, are included in the appendix 4 of the specification, but at this moment that appendix is missing in the document. ...
... As the 0.6 specification says (section 2.1) [5], the details for how to accept connection requests, as well as how to select what other Gnutella hosts to connect to, are included in the appendix 4 of the specification, but at this moment that appendix is missing in the document. ...
How to connect an Epson POS printer with
... Each has a different set of features and a different way of setting them up. ...
... Each has a different set of features and a different way of setting them up. ...
IP
Addressing
and
Forwarding
... • IdenPfy the mask automaPcally from the address – First bit of 0: class A address (/8) – First two bits of 10: class B address (/16) – First three bits of 110: class C address (/24) ...
... • IdenPfy the mask automaPcally from the address – First bit of 0: class A address (/8) – First two bits of 10: class B address (/16) – First three bits of 110: class C address (/24) ...
Top-Down Network Design
... Bandwidth, memory, and CPU usage The number of peers supported The capability to adapt to changes quickly Support for authentication ...
... Bandwidth, memory, and CPU usage The number of peers supported The capability to adapt to changes quickly Support for authentication ...
Top-Down Network Design
... Bandwidth, memory, and CPU usage The number of peers supported The capability to adapt to changes quickly Support for authentication ...
... Bandwidth, memory, and CPU usage The number of peers supported The capability to adapt to changes quickly Support for authentication ...
ZPAK II Debug Interface Module
... the ZPAK II module’s embedded web page via a browser over an Ethernet connection. The other way is via the ZPAK II console port. The following steps describe the console port method. Note: To change the ZPAK II settings from their defaults via a web browser, please consult the ZPAK II Debug Interfac ...
... the ZPAK II module’s embedded web page via a browser over an Ethernet connection. The other way is via the ZPAK II console port. The following steps describe the console port method. Note: To change the ZPAK II settings from their defaults via a web browser, please consult the ZPAK II Debug Interfac ...
Topic 16: Routing in IP over ATM networks
... The packet encapsulation has been defined in RFC1483 ([9], now obsoleted by [10]), which also takes into account the saving of virtual connections by multiplexing different protocols into a single VC. The LLC/SNAP encapsulation defined in RFC1483 is the most common encapsulation in IP over ATM netwo ...
... The packet encapsulation has been defined in RFC1483 ([9], now obsoleted by [10]), which also takes into account the saving of virtual connections by multiplexing different protocols into a single VC. The LLC/SNAP encapsulation defined in RFC1483 is the most common encapsulation in IP over ATM netwo ...
Interdomain and Policy Routing, BGP, MPLS
... Problem when both Alice and Bob are behind “NATs”. ...
... Problem when both Alice and Bob are behind “NATs”. ...
AirLive WT-2000ARM Manual
... upstream transmission rates of up to 1Mbps. It supports PPPoA (RFC 2364 PPP over ATM Adaptation Layer 5), RFC 1483/2684 encapsulation over ATM (bridged or routed) and PPP over Ethernet (RFC 2516) to establish a connection with ISP. The product also supports VC-based and LLC-based multiplexing. With ...
... upstream transmission rates of up to 1Mbps. It supports PPPoA (RFC 2364 PPP over ATM Adaptation Layer 5), RFC 1483/2684 encapsulation over ATM (bridged or routed) and PPP over Ethernet (RFC 2516) to establish a connection with ISP. The product also supports VC-based and LLC-based multiplexing. With ...
20_otherlink
... and it may also piggyback some data to the polling frame. The polled station responds either with an ACK or a data frame piggybacked to the ACK frame. An SIFS separates the polling and responding frames. Once the frame exchange sequence with the first station is done, the PC waits for a PIFS a ...
... and it may also piggyback some data to the polling frame. The polled station responds either with an ACK or a data frame piggybacked to the ACK frame. An SIFS separates the polling and responding frames. Once the frame exchange sequence with the first station is done, the PC waits for a PIFS a ...
point-to-point deep fiber access - NET-im-web
... user gets a dedicated connection that will meet future upgrade requirements and can provide unlimited and symmetric bandwidth. Other key benefits are high scalability and service transparency, which means the ability to provide any service irrespective of other users in the network. P2P fiber also o ...
... user gets a dedicated connection that will meet future upgrade requirements and can provide unlimited and symmetric bandwidth. Other key benefits are high scalability and service transparency, which means the ability to provide any service irrespective of other users in the network. P2P fiber also o ...
excellence ethernet ba e 11780579a
... between the two subscribers and be open for data transfer. For this to be possible, the system must have rules as to which subscriber takes on the active (client) role, and which takes on the passive (server) role. The behavior of each balance in the network is defined by the corresponding configura ...
... between the two subscribers and be open for data transfer. For this to be possible, the system must have rules as to which subscriber takes on the active (client) role, and which takes on the passive (server) role. The behavior of each balance in the network is defined by the corresponding configura ...
DSL-300T Manual-100 - D-Link
... D-Link offices is provided at the back of this manual, together with a copy of the Registration Card. If a Registration Card for the product in question has not been returned to a D-Link office, then a proof of purchase (such as a copy of the dated purchase invoice) must be provided when requesting ...
... D-Link offices is provided at the back of this manual, together with a copy of the Registration Card. If a Registration Card for the product in question has not been returned to a D-Link office, then a proof of purchase (such as a copy of the dated purchase invoice) must be provided when requesting ...
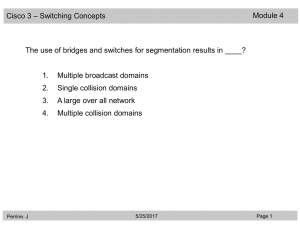
CCNA3 3.0-04 Questions Review of Switching
... After a collision occurs on a half-duplex Ethernet network, how does a transmitting host proceed? (Choose two.) ...
... After a collision occurs on a half-duplex Ethernet network, how does a transmitting host proceed? (Choose two.) ...
Lecture 1: Course Introduction and Overview
... • HW and SW Interface to computer affects overhead, latency, bandwidth • Topologies: many to chose from, but (SW) overheads make them look alike; cost issues in topologies, not FTC.W99 62 algorithms ...
... • HW and SW Interface to computer affects overhead, latency, bandwidth • Topologies: many to chose from, but (SW) overheads make them look alike; cost issues in topologies, not FTC.W99 62 algorithms ...
pptx - University of Cambridge Computer Laboratory
... • understand principles behind network layer services: – network layer service models – forwarding versus routing (versus switching) – how a router works – routing (path selection) – IPv6 ...
... • understand principles behind network layer services: – network layer service models – forwarding versus routing (versus switching) – how a router works – routing (path selection) – IPv6 ...