FANUC 16i/18i/21i Ethernet Settings
... The embedded Ethernet function can be used by selecting one of two types of devices: the embedded Ethernet port and PCMCIA Ethernet card. The PCMCIA Ethernet card is to be inserted into the memory card slot to the left of the front LCD for temporary communication. NOTE 1 Use the PCMCIA Ethernet card ...
... The embedded Ethernet function can be used by selecting one of two types of devices: the embedded Ethernet port and PCMCIA Ethernet card. The PCMCIA Ethernet card is to be inserted into the memory card slot to the left of the front LCD for temporary communication. NOTE 1 Use the PCMCIA Ethernet card ...
Estimating Available Capacity of a Network Connection
... changing bottleneck bandwidth due to path changes. But, bandwidth available on a network path, may often be less than the bottleneck bandwidth, and may also go to zero, due to cross traffic in the path. Our measure differs from these previous work, as we account for the capacity lost due to cross tr ...
... changing bottleneck bandwidth due to path changes. But, bandwidth available on a network path, may often be less than the bottleneck bandwidth, and may also go to zero, due to cross traffic in the path. Our measure differs from these previous work, as we account for the capacity lost due to cross tr ...
Ethernet Switches
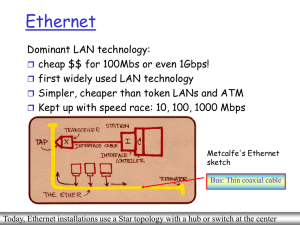
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
module21-mcast
... Build a single distribution tree that is shared by all senders Does not use Solution 2 (because it is too expensive) Selects one router as a “core” (also called “rendezvous point”) All receivers build a shortest path to the core reverse shortest path / reverse path forwarding ...
... Build a single distribution tree that is shared by all senders Does not use Solution 2 (because it is too expensive) Selects one router as a “core” (also called “rendezvous point”) All receivers build a shortest path to the core reverse shortest path / reverse path forwarding ...
topological database - YSU Computer Science & Information Systems
... prunes database of alternative paths and creates loop-free shortest path to all networks ...
... prunes database of alternative paths and creates loop-free shortest path to all networks ...
DSL-504T ADSL Router User’s Guide
... is encouraged to try to correct the interference by one or more of the following measures: - Reorient or relocate the receiving antenna. - Increase the separation between the equipment and receiver. - Connect the equipment into an outlet on a circuit different from that to which the receiver is conn ...
... is encouraged to try to correct the interference by one or more of the following measures: - Reorient or relocate the receiving antenna. - Increase the separation between the equipment and receiver. - Connect the equipment into an outlet on a circuit different from that to which the receiver is conn ...
View
... x.y.z.t defines one of the addresses and the /n defines the mask The first address in the block can be found by setting the rightmost 32 − n bits to 0s The last address in the block can be found by setting the rightmost 32 − n bits to 1s. ...
... x.y.z.t defines one of the addresses and the /n defines the mask The first address in the block can be found by setting the rightmost 32 − n bits to 0s The last address in the block can be found by setting the rightmost 32 − n bits to 1s. ...
TCP in Wireless Networks
... spurious timeouts in wireless networks, to the best of our knowledge, such a method has not yet been proposed in the literature. This may have been due to the fact that the standard way of calculating the RTO value by (1) to (3) has been widely implemented. It will not be easy, if possible at all, t ...
... spurious timeouts in wireless networks, to the best of our knowledge, such a method has not yet been proposed in the literature. This may have been due to the fact that the standard way of calculating the RTO value by (1) to (3) has been widely implemented. It will not be easy, if possible at all, t ...
X31-20050926-029 R2 QCOM 3GPP2 Packet Data Network
... • Simpler CAP-LMHA interface – Air interface changes do not affect LMHA, so no development impact of air interface enhancements – No tight coupling for signaling such as flow control – LMHA becomes a general purpose router => cost effective ...
... • Simpler CAP-LMHA interface – Air interface changes do not affect LMHA, so no development impact of air interface enhancements – No tight coupling for signaling such as flow control – LMHA becomes a general purpose router => cost effective ...
ECx Ethernet Control Guide
... computer can take up to 2 minutes to become effective. After making changes, be sure to allow sufficient time for the system to assign IP addresses and establish communication between all the components. If network communication is not established after allowing sufficient time for IP addressing, th ...
... computer can take up to 2 minutes to become effective. After making changes, be sure to allow sufficient time for the system to assign IP addresses and establish communication between all the components. If network communication is not established after allowing sufficient time for IP addressing, th ...
Broadxent BritePort 8120 Manual
... agrees to be bound by the terms and conditions of this Agreement. 9. Limitations on Using, Copying, and Modifying the Software Except to the extent expressly permitted by this Agreement or by the laws of the jurisdiction where you acquired the Software, you may not use, copy or modify the Software. ...
... agrees to be bound by the terms and conditions of this Agreement. 9. Limitations on Using, Copying, and Modifying the Software Except to the extent expressly permitted by this Agreement or by the laws of the jurisdiction where you acquired the Software, you may not use, copy or modify the Software. ...
router commands briefly explained
... access-list 900 deny sap any 3378 -1 access-list 900 permit sap any all -1 int eth 0 ipx access-group 900 out WAN Configurations Commands Networking over WAN is the main functionality of a router. The most common use of a router is for the WAN connectivity. Here is a list of the commands for the di ...
... access-list 900 deny sap any 3378 -1 access-list 900 permit sap any all -1 int eth 0 ipx access-group 900 out WAN Configurations Commands Networking over WAN is the main functionality of a router. The most common use of a router is for the WAN connectivity. Here is a list of the commands for the di ...
Chapter 7 Lecture Presentation
... Packet networks very different than telephone networks Individual packet streams are highly bursty ...
... Packet networks very different than telephone networks Individual packet streams are highly bursty ...
Packet-Switching Networks
... Packet networks very different than telephone networks Individual packet streams are highly bursty ...
... Packet networks very different than telephone networks Individual packet streams are highly bursty ...
An Introduction to TCP/IP
... gateway sends them on to the Internet for routing to some other computer in the world. Data coming in from the Internet are directed to the gateway, which then sends them to the correct recipient on the local network. ...
... gateway sends them on to the Internet for routing to some other computer in the world. Data coming in from the Internet are directed to the gateway, which then sends them to the correct recipient on the local network. ...
Lab Exercise – ICMP
... The length of 20 bytes is for a typical IPv4 header with no IP option fields. ...
... The length of 20 bytes is for a typical IPv4 header with no IP option fields. ...
Wireless Networks
... Internet, millions of computers use (variants of) this protocol optimized TCP protocol for mobile hosts splitting of the TCP connection at, e.g., the foreign agent into 2 TCP connections, no real end-to-end connection any longer hosts in the fixed part of the net do not notice the characterist ...
... Internet, millions of computers use (variants of) this protocol optimized TCP protocol for mobile hosts splitting of the TCP connection at, e.g., the foreign agent into 2 TCP connections, no real end-to-end connection any longer hosts in the fixed part of the net do not notice the characterist ...
BOSNST - Openwall
... A new model for conceptualizing and describing network security tools • How to apply this model to existing tools • How to use this model to rapidly build new tools ...
... A new model for conceptualizing and describing network security tools • How to apply this model to existing tools • How to use this model to rapidly build new tools ...
Tema 1: Tecnologías de red. - GRC
... Lots of opportunities for small groups to delay things Original idea of RFC standards-track progression: Proposed Standard (PS) = kind of works Draft Standard (DS) = solid, interoperability tested (2 interoperable implementations for each feature), but not necessarily widely used Standard ...
... Lots of opportunities for small groups to delay things Original idea of RFC standards-track progression: Proposed Standard (PS) = kind of works Draft Standard (DS) = solid, interoperability tested (2 interoperable implementations for each feature), but not necessarily widely used Standard ...
Avaya Virtual Services Platform 8000 Series
... 8000 Series is the first incarnation of a new concept in data networking, the compact form-factor (CFF) Ethernet Switch. The CFF concept seeks to address the needs of businesses that range from the mid-market all the way up to mid-to-large Enterprises, with highly flexible deployment capabilities. T ...
... 8000 Series is the first incarnation of a new concept in data networking, the compact form-factor (CFF) Ethernet Switch. The CFF concept seeks to address the needs of businesses that range from the mid-market all the way up to mid-to-large Enterprises, with highly flexible deployment capabilities. T ...
TPOT: Translucent Proxying of TCP
... specific set of destination addresses. The proxy responds to the client request, masquerading as the remote web server. Scalability is achieved by partitioning client requests into separate hash buckets based on the destination address, effectively mapping web servers to multiple caches attached to ...
... specific set of destination addresses. The proxy responds to the client request, masquerading as the remote web server. Scalability is achieved by partitioning client requests into separate hash buckets based on the destination address, effectively mapping web servers to multiple caches attached to ...
No Slide Title
... The web server provides the web service. Bob uses a web browser, which is a web client, to request and receive web service. The HyperText Transfer Protocol (HTTP) is used by the web server and browser. ...
... The web server provides the web service. Bob uses a web browser, which is a web client, to request and receive web service. The HyperText Transfer Protocol (HTTP) is used by the web server and browser. ...
CCNA1 Complete Lecture Set Mod 1 to 11
... systems are now commonly installed in place of traditional voice systems, which further adds to the need for bandwidth. Bandwidth is like the width of a pipe. A network of pipes brings fresh water to homes and businesses and carries waste water away. Therefore, the water is like the data, and the pi ...
... systems are now commonly installed in place of traditional voice systems, which further adds to the need for bandwidth. Bandwidth is like the width of a pipe. A network of pipes brings fresh water to homes and businesses and carries waste water away. Therefore, the water is like the data, and the pi ...
20060718-bpc
... NLR PacketNet between NC and GT Not all that interesting, since both sites attach to the same NLR router in Atlanta ...
... NLR PacketNet between NC and GT Not all that interesting, since both sites attach to the same NLR router in Atlanta ...