Efficient data structures for sparse network representation
... it prematurely. A special mark is thus utilized for slots from which an element has been removed. Such a slot is then treated as a used one during seeks and as an empty one during insertions. The chaining hash table implementation suffers only from a graceful degradation of performance when the numb ...
... it prematurely. A special mark is thus utilized for slots from which an element has been removed. Such a slot is then treated as a used one during seeks and as an empty one during insertions. The chaining hash table implementation suffers only from a graceful degradation of performance when the numb ...
Networking Security
... • Attacker may can extend an application’s SQL statement to extract or update information that the attacker is not authorized to access • Attacker will explore how the Web application interacts with the back-end database by finding a user-supplied input string that will be part of a database query ...
... • Attacker may can extend an application’s SQL statement to extract or update information that the attacker is not authorized to access • Attacker will explore how the Web application interacts with the back-end database by finding a user-supplied input string that will be part of a database query ...
PowerPoint
... Uniform distribution of search-key values, i.e., same no. of search-key values in each bucket Random distribution of search-key values, i.e., each search-key 19 value has the same possibility ...
... Uniform distribution of search-key values, i.e., same no. of search-key values in each bucket Random distribution of search-key values, i.e., each search-key 19 value has the same possibility ...
Similarity Search in High Dimension via Hashing
... • Exact vs. Approximate Answer – Approximate might be good-enough and much-faster – Time-quality trade-off ...
... • Exact vs. Approximate Answer – Approximate might be good-enough and much-faster – Time-quality trade-off ...
Data warehousing with MySQL Flat Files MySQL MS-SQL
... clients can't wait for the INSERT to complete. Many client bundled together and written in one block • Compress MyISAM tables with “myisampack” to take up much less space. • Benefit from higher performance on SELECT statements ...
... clients can't wait for the INSERT to complete. Many client bundled together and written in one block • Compress MyISAM tables with “myisampack” to take up much less space. • Benefit from higher performance on SELECT statements ...
types of searchings - SSC Recruitment Results
... Information retrieval is one of the most important applications of computers. It usually involves giving a piece of information called the key, and ask to find a record that contains other associated information. This is achieved by first going through the list to find if the given key exists or not ...
... Information retrieval is one of the most important applications of computers. It usually involves giving a piece of information called the key, and ask to find a record that contains other associated information. This is achieved by first going through the list to find if the given key exists or not ...
Algorithms
... http://www.cs.princeton.edu/introcs/13loop/Hello.java http://www.cs.princeton.edu/introcs/13loop/Hello.class http://www.cs.princeton.edu/introcs/13loop/Hello.html ...
... http://www.cs.princeton.edu/introcs/13loop/Hello.java http://www.cs.princeton.edu/introcs/13loop/Hello.class http://www.cs.princeton.edu/introcs/13loop/Hello.html ...
Data structures and performance analysis
... In addition to the code you write for data structures and the text editor plugins, you should also submit any tests that you write. Testing is a component of the grade for this assignment. You should implement your test cases using JUnit, a framework for writing test suites. JUnit has excellent Ecli ...
... In addition to the code you write for data structures and the text editor plugins, you should also submit any tests that you write. Testing is a component of the grade for this assignment. You should implement your test cases using JUnit, a framework for writing test suites. JUnit has excellent Ecli ...
Clustering for Accuracy, Performance, and Alternative
... This can be done, but it will not scale to 100 seconds, because you can no longer hold 30 billion nucleotides in memory. You will have to swap portions of the 30 billion back to disk, and read in a new ...
... This can be done, but it will not scale to 100 seconds, because you can no longer hold 30 billion nucleotides in memory. You will have to swap portions of the 30 billion back to disk, and read in a new ...
Security - The University of Texas at Dallas
... • You hear them murmur, "Let's see you use that VISA card now, Professor "I-Don't-Give-A's-To Any MBA Candidate!" ...
... • You hear them murmur, "Let's see you use that VISA card now, Professor "I-Don't-Give-A's-To Any MBA Candidate!" ...
previous-qns-and-answers
... •More evenly distributed digit positions are extracted and used for hashing purposes. ...
... •More evenly distributed digit positions are extracted and used for hashing purposes. ...
Survey of online attacks on E-Commerce sites
... both among employees, and between employees and the outside world. It is thus one possible source of data from which potential problems can be detected [2].Examples include - A statement that there is a problem with user account at a financial institute . The email ask s recipient to visit a web sit ...
... both among employees, and between employees and the outside world. It is thus one possible source of data from which potential problems can be detected [2].Examples include - A statement that there is a problem with user account at a financial institute . The email ask s recipient to visit a web sit ...
Slides
... • Choose a hash funcLon at random from a large parameterized family of hash funcLons (e.g., h(x) = ax + b, where a and b are chosen at random) • With high probability, it will be just as ...
... • Choose a hash funcLon at random from a large parameterized family of hash funcLons (e.g., h(x) = ax + b, where a and b are chosen at random) • With high probability, it will be just as ...
Exercise
... Binary search trees • Binary search trees allow for fast insertion and removal of elements • They are specially designed for fast searching • All nodes in a binary search tree fulfill the property that: Descendants to the left have smaller data values than the node data value Descendants to the ...
... Binary search trees • Binary search trees allow for fast insertion and removal of elements • They are specially designed for fast searching • All nodes in a binary search tree fulfill the property that: Descendants to the left have smaller data values than the node data value Descendants to the ...
ppt - EECG Toronto
... if (n_items == m_table_size - 1) return (false); // Table full! Need to resize. index = hash (item.key); // “Home” spot for item. ...
... if (n_items == m_table_size - 1) return (false); // Table full! Need to resize. index = hash (item.key); // “Home” spot for item. ...
Intruders and password protection
... three characters. The state of the system at any time is the identity of the most recent letter. The value on the transition from one state to another represents the probability that one letter follows another. Thus, the probability that the next letter is b, given that the current letter is a, is 0 ...
... three characters. The state of the system at any time is the identity of the most recent letter. The value on the transition from one state to another represents the probability that one letter follows another. Thus, the probability that the next letter is b, given that the current letter is a, is 0 ...
b63_midterm-version2..
... However, we want to use as little memory as possible. We can save some memory by eliminating the extra field from each ListNode. Explain how we can do this, yet still determine a word’s category in O(1) time. Hint: you can adjust the data structure in some other way, use a combination of data struct ...
... However, we want to use as little memory as possible. We can save some memory by eliminating the extra field from each ListNode. Explain how we can do this, yet still determine a word’s category in O(1) time. Hint: you can adjust the data structure in some other way, use a combination of data struct ...
Maintaining External Memory Efficient Hash Tables
... for a dynamic dictionary where the data associated with each key comprises r bits. Update operations are supported with high probability in constant time and the algorithm is stable. For the static case, Hagerup and Tholey [10] hold the space record: They show how to construct a minimal perfect has ...
... for a dynamic dictionary where the data associated with each key comprises r bits. Update operations are supported with high probability in constant time and the algorithm is stable. For the static case, Hagerup and Tholey [10] hold the space record: They show how to construct a minimal perfect has ...
Applications of Linear Programming
... Applications of Linear Programming Example 3 A 4-H member raises goats and pigs. She wants to raise no more than 16 animals, including no more than 10 goats. She spends $25 to raise a goat and $75 to raise a pig, and she has $900 available for the project. The 4-H member wishes to maximize her prof ...
... Applications of Linear Programming Example 3 A 4-H member raises goats and pigs. She wants to raise no more than 16 animals, including no more than 10 goats. She spends $25 to raise a goat and $75 to raise a pig, and she has $900 available for the project. The 4-H member wishes to maximize her prof ...
pptx - Chair of Software Engineering
... Removal: remove an occurrence (if any) of an item Wipeout: remove all occurrences of an item Search: find out if a given item is present Iteration (or “traversal”): apply a given operation to every item Various container implementations, as studied next, determine: Which of these operation ...
... Removal: remove an occurrence (if any) of an item Wipeout: remove all occurrences of an item Search: find out if a given item is present Iteration (or “traversal”): apply a given operation to every item Various container implementations, as studied next, determine: Which of these operation ...
Data Structures
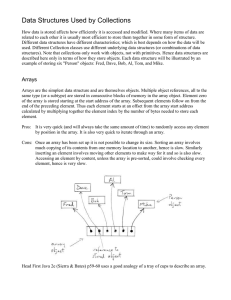
... of the array is stored starting at the start address of the array. Subsequent elements follow on from the end of the preceding element. Thus each element starts at an offset from the array start address calculated by multiplying together the element index by the number of bytes needed to store each ...
... of the array is stored starting at the start address of the array. Subsequent elements follow on from the end of the preceding element. Thus each element starts at an offset from the array start address calculated by multiplying together the element index by the number of bytes needed to store each ...
Using Hash Components
... • Generally, Key order should follow data hierarchy • Within a program, keys should follow function › The fewer the better › Save listing order until last ...
... • Generally, Key order should follow data hierarchy • Within a program, keys should follow function › The fewer the better › Save listing order until last ...
Rainbow table
A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering a plaintext password up to a certain length consisting of a limited set of characters. It is a practical example of a space/time trade-off, using less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing time and less storage than a simple lookup table with one entry per hash. Use of a key derivation function that employs a salt makes this attack infeasible.Rainbow tables are an application of an earlier, simpler algorithm by Martin Hellman.