Lecture19 - The University of Texas at Dallas
... strict layers as the OSI model. • TCP/IP does recognize four broad layers of functionality which are derived from the operating scope of their contained protocols, namely the scope of the software application, the end-to-end transport connection, the internetworking range, and lastly the scope of th ...
... strict layers as the OSI model. • TCP/IP does recognize four broad layers of functionality which are derived from the operating scope of their contained protocols, namely the scope of the software application, the end-to-end transport connection, the internetworking range, and lastly the scope of th ...
Topologies
... hosts • Hosts are not part of any layer • Operate at all layers • Symbols not standardized – Bear a resemblance to device ...
... hosts • Hosts are not part of any layer • Operate at all layers • Symbols not standardized – Bear a resemblance to device ...
TDC 463-98-501/502, Summer II 2002 1-3
... Timing/Procedrue: when data should be sent and how fast it can be sent. TDC 463-98-501/502, Summer II 2002 ...
... Timing/Procedrue: when data should be sent and how fast it can be sent. TDC 463-98-501/502, Summer II 2002 ...
Split-TCP: State of the Union Address
... There are over 150 tuning parameters in the “stock” NS TCP code. If they were all just binary parameters that’s still 2150 possible ...
... There are over 150 tuning parameters in the “stock” NS TCP code. If they were all just binary parameters that’s still 2150 possible ...
Lecture 14
... network # and allocate the IP addresses with that network # to several physical networks ...
... network # and allocate the IP addresses with that network # to several physical networks ...
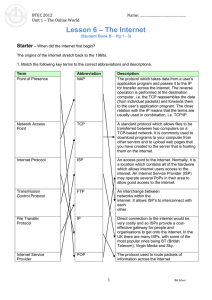
U1L6_The_Internet
... application program and passes it to the IP for transfer across the internet. The reverse operation is performed at the destination computer, i.e. the TCP reassembles the data (from individual packets) and forwards them to the user’s application program. The close relation with the IP means that the ...
... application program and passes it to the IP for transfer across the internet. The reverse operation is performed at the destination computer, i.e. the TCP reassembles the data (from individual packets) and forwards them to the user’s application program. The close relation with the IP means that the ...
Computer Networking viva IT-3
... A3 An internet architecture in which routers connect multiple physical networks. Q4 Is internet a virtual network ? A4 yes An internet is a single virtual network that interconnects all hosts and through which communication is possible ;its under lying architecture is both hidden and irrelevant. Q5 ...
... A3 An internet architecture in which routers connect multiple physical networks. Q4 Is internet a virtual network ? A4 yes An internet is a single virtual network that interconnects all hosts and through which communication is possible ;its under lying architecture is both hidden and irrelevant. Q5 ...
Certification Exercise 2
... LAN Transmission Equipment 1. In which OSI layer does a repeater operate? a) Network b) Physical c) Data Link d) Transport 2. What does the last three octets of the MAC address 00 B0 D0 5A E1 B5 identify? a) the Device ID b) the type of device c) the manufacturer of the device d) the network address ...
... LAN Transmission Equipment 1. In which OSI layer does a repeater operate? a) Network b) Physical c) Data Link d) Transport 2. What does the last three octets of the MAC address 00 B0 D0 5A E1 B5 identify? a) the Device ID b) the type of device c) the manufacturer of the device d) the network address ...
Chapter 1: Introducing Networks
... 5. Which of the following best describes the Data Link layer? a. Provides the electrical and mechanical transmission of data b. Handles link control and uses the MAC address on the NIC c. Establishes, maintains, and manages sessions between applications d. Translates, encrypts, or prepares data from ...
... 5. Which of the following best describes the Data Link layer? a. Provides the electrical and mechanical transmission of data b. Handles link control and uses the MAC address on the NIC c. Establishes, maintains, and manages sessions between applications d. Translates, encrypts, or prepares data from ...
ECE 526
... IP Forwarding • Routing Table ─ Found in both hosts and routers ─ Stores destination, mask, next hop ...
... IP Forwarding • Routing Table ─ Found in both hosts and routers ─ Stores destination, mask, next hop ...
Computer Networks Sample Questions
... 10. Your company has several computers, which store sensitive data that should not be accessed by everyone on the network. Which network model will most appropriate? a. peer-t0-peer. b. workgroup network. c. client/server network. d. server based with each computer acting as both client and server. ...
... 10. Your company has several computers, which store sensitive data that should not be accessed by everyone on the network. Which network model will most appropriate? a. peer-t0-peer. b. workgroup network. c. client/server network. d. server based with each computer acting as both client and server. ...
Fragmentation and IP Forwarding
... length fragment 16-bit identifier flgs offset time to upper header layer live checksum ...
... length fragment 16-bit identifier flgs offset time to upper header layer live checksum ...
, or - Geoff Huston
... – No signalled connection between link level conditions and transport services – Universal abstraction of a common simple packet transmission service that has been adapted to operate efficiently over wires, modems, Frame Relay, ATM, Ethernet, broadcast radio, packet radio, satellite circuits, SDH, f ...
... – No signalled connection between link level conditions and transport services – Universal abstraction of a common simple packet transmission service that has been adapted to operate efficiently over wires, modems, Frame Relay, ATM, Ethernet, broadcast radio, packet radio, satellite circuits, SDH, f ...
3rd Edition: Chapter 2
... learn about transport layer protocols in the Internet: UDP: connectionless transport TCP: connection-oriented transport TCP congestion control ...
... learn about transport layer protocols in the Internet: UDP: connectionless transport TCP: connection-oriented transport TCP congestion control ...
(CCNA) 3.Transport Layer Protocols
... and receivers to exchange information about their availability or ability to communicate with one another, “best effort” delivery. (Type supported by IP, UDP). Not reliable, but faster and may be good enough. Also upper layer apps may worry about errors and reliability processing, so no need to do i ...
... and receivers to exchange information about their availability or ability to communicate with one another, “best effort” delivery. (Type supported by IP, UDP). Not reliable, but faster and may be good enough. Also upper layer apps may worry about errors and reliability processing, so no need to do i ...
Internet Protocol
... Internet employs TCP/IP protocol stack. Most of the applications require reliable transmission layer (mostly TCP). Wireless network must support existing applications. Packet loss can occur because of random errors as well as due to congestion. Decreases efficiency due to TCP’s Congestion ...
... Internet employs TCP/IP protocol stack. Most of the applications require reliable transmission layer (mostly TCP). Wireless network must support existing applications. Packet loss can occur because of random errors as well as due to congestion. Decreases efficiency due to TCP’s Congestion ...
Wireless and Mobile System Infrastructure
... Internet employs TCP/IP protocol stack. Most of the applications require reliable transmission layer (mostly TCP). Wireless network must support existing applications. Packet loss can occur because of random errors as well as due to congestion. Decreases efficiency due to TCP’s Congestion ...
... Internet employs TCP/IP protocol stack. Most of the applications require reliable transmission layer (mostly TCP). Wireless network must support existing applications. Packet loss can occur because of random errors as well as due to congestion. Decreases efficiency due to TCP’s Congestion ...
Data Communications and Computer Networks
... Physical characteristics of interfaces and media Representation of bits Data rate (transmission rate) Synchronization of bits ...
... Physical characteristics of interfaces and media Representation of bits Data rate (transmission rate) Synchronization of bits ...
transparencies
... • Maximum Amount of data per unit time that a path can provide to an application given the current utilization, protocol in use, operating system and end-host capability [GGF NMWG Hierarchy document] This is metric involves more than just the network element ...
... • Maximum Amount of data per unit time that a path can provide to an application given the current utilization, protocol in use, operating system and end-host capability [GGF NMWG Hierarchy document] This is metric involves more than just the network element ...
A Big Test Result - Knowledge Systems Institute
... • Data that is sent from one LAN to another along any of several available paths is said to be routed. • The protocols that support multipath LAN-to-LAN communications are known as routable protocols. • Because routable protocols can be used to tie several LANs together and create new wide-area envi ...
... • Data that is sent from one LAN to another along any of several available paths is said to be routed. • The protocols that support multipath LAN-to-LAN communications are known as routable protocols. • Because routable protocols can be used to tie several LANs together and create new wide-area envi ...
Introduction
... • Framing: LLC defines PDU similar to HDLC. Header contains flow and error control functions • LLC Header also defines upper layer protocol at source and dest. that uses LLC called DSAP & SSAP (not used by IP) • Other fields including access methods have been moved to MAC layer. Physical layer is me ...
... • Framing: LLC defines PDU similar to HDLC. Header contains flow and error control functions • LLC Header also defines upper layer protocol at source and dest. that uses LLC called DSAP & SSAP (not used by IP) • Other fields including access methods have been moved to MAC layer. Physical layer is me ...
lecture03
... Network Effects • A product or service exhibits network effects if its value to any single user is strongly positively correlated with the total number of users. Communication ...
... Network Effects • A product or service exhibits network effects if its value to any single user is strongly positively correlated with the total number of users. Communication ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).