PPT - Pages
... – Demultiplexing to higher layer protocols – TCP = 6, ICMP = 1, UDP = 17… – Ensures some degree of header integrity ...
... – Demultiplexing to higher layer protocols – TCP = 6, ICMP = 1, UDP = 17… – Ensures some degree of header integrity ...
Finance Evolution
... MPLS was used for its intended purpose and at intended scale • Goal was to switch packets to support rapidly expanding global networks – MPLS is “wildly successful” (RFC 5218) in that its use has exceeded its original design goal thru development of numerous extensions – From service provider perspe ...
... MPLS was used for its intended purpose and at intended scale • Goal was to switch packets to support rapidly expanding global networks – MPLS is “wildly successful” (RFC 5218) in that its use has exceeded its original design goal thru development of numerous extensions – From service provider perspe ...
Slide 1
... address. This is usually done when the interface is configured at bootstrap time, to initialize its IP stack. It helps to check for a duplicate IP address. • Arp command – try out yourself in windows/unix. Khaled Mahbub, IICT, BUET, 2008 ...
... address. This is usually done when the interface is configured at bootstrap time, to initialize its IP stack. It helps to check for a duplicate IP address. • Arp command – try out yourself in windows/unix. Khaled Mahbub, IICT, BUET, 2008 ...
Network Infrastructure Insecurity
... Default ACL’s are typically poor Authentication mechanisms still not fully implemented – CA based authentication still only part there DoS ...
... Default ACL’s are typically poor Authentication mechanisms still not fully implemented – CA based authentication still only part there DoS ...
IMS
... methods, all of which are using the standard Internet Protocol(IP). Direct IMS terminals (mobile phones, computers, ...), can register directly into an IMS network, even when they are roaming in another network or country (the visited network). Fixed access (e.g., DSL, Cable Modems, Ethernet ...), m ...
... methods, all of which are using the standard Internet Protocol(IP). Direct IMS terminals (mobile phones, computers, ...), can register directly into an IMS network, even when they are roaming in another network or country (the visited network). Fixed access (e.g., DSL, Cable Modems, Ethernet ...), m ...
Measurement and Analysis of TCP Throughput Collapse in Cluster-based Storage Systems
... To ensure that the throughput collapse shown in Figure 2 is not an isolated instance, we study Incast on the three storage clusters described in §3.2. Figure 3 indicates that both the Procurve and S50 environments experience up to an order of magnitude drop in goodput (throughput as observed by the ...
... To ensure that the throughput collapse shown in Figure 2 is not an isolated instance, we study Incast on the three storage clusters described in §3.2. Figure 3 indicates that both the Procurve and S50 environments experience up to an order of magnitude drop in goodput (throughput as observed by the ...
1 - Cisco Support Community
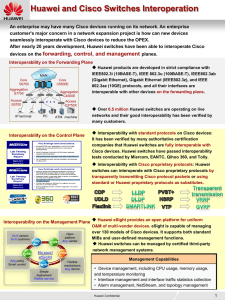
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
Applications
... network services. • RTP is commonly used in Internet telephony applications. RTP does not in itself guarantee realtime delivery of multimedia data. • RTP combines its data transport with a control protocol (RTCP), which makes it possible to monitor data delivery for large multicast networks. ...
... network services. • RTP is commonly used in Internet telephony applications. RTP does not in itself guarantee realtime delivery of multimedia data. • RTP combines its data transport with a control protocol (RTCP), which makes it possible to monitor data delivery for large multicast networks. ...
Slide 1
... RIP 2 fields or using authentication, this value is set to 2. Routing Domain: An identifier of the routing daemon, to which this packet belongs. Address-Family Identifier (AFI)—Specifies the address family used. RIP is designed to carry routing information for several different protocols. Each entry ...
... RIP 2 fields or using authentication, this value is set to 2. Routing Domain: An identifier of the routing daemon, to which this packet belongs. Address-Family Identifier (AFI)—Specifies the address family used. RIP is designed to carry routing information for several different protocols. Each entry ...
ppt - Suraj @ LUMS
... Areas where there is only one exit point, or the exit point is not a function of the external destination Stub area does not need to know the topology of the rest of the AS ...
... Areas where there is only one exit point, or the exit point is not a function of the external destination Stub area does not need to know the topology of the rest of the AS ...
Ch4_3ed
... subnet portion of address of arbitrary length address format: a.b.c.d/x, where x is # bits in subnet portion of address ...
... subnet portion of address of arbitrary length address format: a.b.c.d/x, where x is # bits in subnet portion of address ...
lecture11
... To use the Internet as a private Wide Area Network, organizations may have to address two issues : First, networks often communicate using a variety of protocols, such as IPX and NetBEUI, but the Internet can only handle TCP/IP traffic. So VPN may need to provide a way to pass non-TCP/IP protocols f ...
... To use the Internet as a private Wide Area Network, organizations may have to address two issues : First, networks often communicate using a variety of protocols, such as IPX and NetBEUI, but the Internet can only handle TCP/IP traffic. So VPN may need to provide a way to pass non-TCP/IP protocols f ...
4th Edition: Chapter 1
... What’s the Internet: “nuts and bolts” view protocols control sending, ...
... What’s the Internet: “nuts and bolts” view protocols control sending, ...
Tier-1 ISP
... relationship of complex system’s pieces layered reference model for discussion modularization eases maintenance, updating of system change of implementation of layer’s service transparent to rest of system e.g., change in gate procedure doesn’t affect rest of system layering considered har ...
... relationship of complex system’s pieces layered reference model for discussion modularization eases maintenance, updating of system change of implementation of layer’s service transparent to rest of system e.g., change in gate procedure doesn’t affect rest of system layering considered har ...
356961: Internet Protocols
... ISO/OSI reference model Category 5 unshielded twisted pair cable is better than category 3 cable. Finding path from one node to another in a large network is a transport layer function. It is impossible to send 3000 bits/second through a wire which has a bandwidth of 1000 Hz. ...
... ISO/OSI reference model Category 5 unshielded twisted pair cable is better than category 3 cable. Finding path from one node to another in a large network is a transport layer function. It is impossible to send 3000 bits/second through a wire which has a bandwidth of 1000 Hz. ...
IP: Adressing, ARP, and Routing
... When all machines receive the ARP request broadcast, they can store the address mapping in their cache. Do they? ARP is used when an IP to physical address mapping changes to notify hosts on the network of the change ARP messages are encapsulated in MAC frames. A special value in the type field of t ...
... When all machines receive the ARP request broadcast, they can store the address mapping in their cache. Do they? ARP is used when an IP to physical address mapping changes to notify hosts on the network of the change ARP messages are encapsulated in MAC frames. A special value in the type field of t ...
ppt
... LS packet dissemination Topology map at each node Route computation using Dijkstra’s algorithm OSPF advertisement carries one entry per neighbor ...
... LS packet dissemination Topology map at each node Route computation using Dijkstra’s algorithm OSPF advertisement carries one entry per neighbor ...
Difficulties in Simulating the Internet
... tervention to maintain critical network properties such as stability becomes a recipe for disaster. A third key property is that the Internet changes in drastic ways over time. For example, we mentioned above that in Dec. 2000, the network included 100 million computers. But in Jan. 1997, four years ...
... tervention to maintain critical network properties such as stability becomes a recipe for disaster. A third key property is that the Internet changes in drastic ways over time. For example, we mentioned above that in Dec. 2000, the network included 100 million computers. But in Jan. 1997, four years ...
Polygraph: Automatically Generating Signatures for
... Defining traffic workloads MobileNode architecture Trace file format ...
... Defining traffic workloads MobileNode architecture Trace file format ...
Managing Soft-errors in Transactional Systems
... We developed a preliminary implementation of the proposed approach and conducted an early experimental evaluation. We implemented all of the modules in C++ The network layer, in particular, was designed and implemented to be platform-independent: it can run transparently on both message-passing and ...
... We developed a preliminary implementation of the proposed approach and conducted an early experimental evaluation. We implemented all of the modules in C++ The network layer, in particular, was designed and implemented to be platform-independent: it can run transparently on both message-passing and ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).