Oracle_ch3 - Gonzaga University Student Web Server
... • Mark a column as unused and then delete it at a later time • Rename a table • Truncate a table • Drop a table Dr. Chen, Oracle Database System (Oracle) ...
... • Mark a column as unused and then delete it at a later time • Rename a table • Truncate a table • Drop a table Dr. Chen, Oracle Database System (Oracle) ...
Ensuring transaction integrity
... Data dictionary facilities • Data dictionary = system tables that store metadata • Users usually can view some of these tables, using SELECT statements that can generate reports about system usage, user privileges etc, • Users are restricted from updating them, sine the DBMS maintains them and depe ...
... Data dictionary facilities • Data dictionary = system tables that store metadata • Users usually can view some of these tables, using SELECT statements that can generate reports about system usage, user privileges etc, • Users are restricted from updating them, sine the DBMS maintains them and depe ...
Introduction to Structured Query Language Version 4.66 Copyright 1996-2001, James Hoffman
... each other, because the unique OwnerID column will be used throughout the database to track the owners, rather than the names. A foreign key is a column in a table where that column is a primary key of another table, which means that any data in a foreign key column must have corresponding data in t ...
... each other, because the unique OwnerID column will be used throughout the database to track the owners, rather than the names. A foreign key is a column in a table where that column is a primary key of another table, which means that any data in a foreign key column must have corresponding data in t ...
Embedded SQL
... contain any SQL statement other than a query and can have a known number of placeholders. Prepare once, run many times (with different values in input host variables). Lecture 15 ...
... contain any SQL statement other than a query and can have a known number of placeholders. Prepare once, run many times (with different values in input host variables). Lecture 15 ...
Chapter Prerequisites
... Follow the instructions on screen. Particularly, if you have not specified your own password differently, the password for user “system” is “manager.” Once the script completes successfully, leave the current SQL*Plus session open and use it to perform this chapter's exercises in the order that they ...
... Follow the instructions on screen. Particularly, if you have not specified your own password differently, the password for user “system” is “manager.” Once the script completes successfully, leave the current SQL*Plus session open and use it to perform this chapter's exercises in the order that they ...
Chapter 4
... Follow the instructions on screen. Particularly, if you have not specified your own password differently, the password for user “system” is “manager.” Once the script completes successfully, leave the current SQL*Plus session open and use it to perform this chapter's exercises in the order that they ...
... Follow the instructions on screen. Particularly, if you have not specified your own password differently, the password for user “system” is “manager.” Once the script completes successfully, leave the current SQL*Plus session open and use it to perform this chapter's exercises in the order that they ...
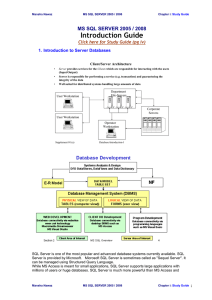
Introduction to Database Systems
... Connecting SQL to the Host Language 1. Embedded SQL is a standard for combining SQL with seven languages. 2. CLI (Call-Level Interface ) is a different approach to connecting from a host language to an SQL database. • SQL/CLI • JDBC (Java Database Connectivity ) is a way to connect Java with an SQL ...
... Connecting SQL to the Host Language 1. Embedded SQL is a standard for combining SQL with seven languages. 2. CLI (Call-Level Interface ) is a different approach to connecting from a host language to an SQL database. • SQL/CLI • JDBC (Java Database Connectivity ) is a way to connect Java with an SQL ...
- Courses - University of California, Berkeley
... • Currently no way to have multiple authors for a given book, and there is duplicate data spread over the BIBFILE table • Can we use the DBMS to help us normalize? • It is possible (but takes a bit more SQL knowledge than has been hinted at so far) – We will return to this problem later – But CONCEP ...
... • Currently no way to have multiple authors for a given book, and there is duplicate data spread over the BIBFILE table • Can we use the DBMS to help us normalize? • It is possible (but takes a bit more SQL knowledge than has been hinted at so far) – We will return to this problem later – But CONCEP ...
Chapter 2 - High Point University
... Relationship is represented by using common columns in two or more tables ...
... Relationship is represented by using common columns in two or more tables ...
Compatibility, compilation and execution of PL/SQL code on the
... Database management system IBM DB2 10.1 is designed for managing data in traditional relational structures, as well as a hierarchy XML. DB2 allows to operate Oracle SQL language dialects and PL / SQL (Oracle version 10g, 11g and 12c). Therefore, many applications written for Oracle database manageme ...
... Database management system IBM DB2 10.1 is designed for managing data in traditional relational structures, as well as a hierarchy XML. DB2 allows to operate Oracle SQL language dialects and PL / SQL (Oracle version 10g, 11g and 12c). Therefore, many applications written for Oracle database manageme ...
08_DBApplicationDeve.. - School of Information Technologies
... PDOStatement class: Precompiled, parameterized SQL statements: Structure is fixed after call to PDO::prepare() Values of parameters are determined at run-time Fetch and store routines are executed when PDOStatement::execute() is executed to communicate argument values with DBMS PDOStatemen ...
... PDOStatement class: Precompiled, parameterized SQL statements: Structure is fixed after call to PDO::prepare() Values of parameters are determined at run-time Fetch and store routines are executed when PDOStatement::execute() is executed to communicate argument values with DBMS PDOStatemen ...
Backup + Restore
... Modify a database recovery model 1. Alter database pubs 2. Set recovery to bulk_logged ...
... Modify a database recovery model 1. Alter database pubs 2. Set recovery to bulk_logged ...
primary key
... constraint. They test values inserted in the database, and test queries to ensure that the comparisons make sense. New domains can be created from existing data types ...
... constraint. They test values inserted in the database, and test queries to ensure that the comparisons make sense. New domains can be created from existing data types ...
SQL - La Salle University
... which the programmer uses an Application Programming Interface (API) such as ODBC (Windows) or JDBC (Java) ...
... which the programmer uses an Application Programming Interface (API) such as ODBC (Windows) or JDBC (Java) ...
Retrieving Data Using the SQL SELECT Statement
... required if you execute multiple SQL statements. • In SQL*Plus, you are required to end each SQL statement with a semicolon (;). ...
... required if you execute multiple SQL statements. • In SQL*Plus, you are required to end each SQL statement with a semicolon (;). ...
Database - bYTEBoss
... backup of your database and all transaction logs in sequence – The database is then in the same consistent state as it was at the point when the transaction log was backed up for the very last time – When you recover a database using a Full Database Backup, SQL Server 2005 first reconstructs all dat ...
... backup of your database and all transaction logs in sequence – The database is then in the same consistent state as it was at the point when the transaction log was backed up for the very last time – When you recover a database using a Full Database Backup, SQL Server 2005 first reconstructs all dat ...
MAA / Data Guard 12c Setup Guide Creating a RAC Physical
... Implemented Maximum Availability Architecture (MAA) configuration for RAC primary database with RAC physical standby database using Oracle Data Guard and tested the configuration with objects. The goal of Maximum Availability Architecture (MAA) is to achieve optimal high availability for Oracle cust ...
... Implemented Maximum Availability Architecture (MAA) configuration for RAC primary database with RAC physical standby database using Oracle Data Guard and tested the configuration with objects. The goal of Maximum Availability Architecture (MAA) is to achieve optimal high availability for Oracle cust ...
Insert, Update and Delete in Access
... All advanced database management systems include some kind of service applications as part of the database system. For example, to use the SQL Server database, you must have an application called "SQL Server Engine" running on the computer. This application is a windows service (a hidden application ...
... All advanced database management systems include some kind of service applications as part of the database system. For example, to use the SQL Server database, you must have an application called "SQL Server Engine" running on the computer. This application is a windows service (a hidden application ...
AGINITY WORKBENCH FOR NETEZZA FUNCTIONALITY OVERVIEW
... In addition, you can drag any node from the Object Explorer tree to the SQL Editor to insert the text where the pointer is currently positioned, or at the point where the text is copied into the Query Editor (this behavior can also be customized using the Tools/Options windows). ...
... In addition, you can drag any node from the Object Explorer tree to the SQL Editor to insert the text where the pointer is currently positioned, or at the point where the text is copied into the Query Editor (this behavior can also be customized using the Tools/Options windows). ...
6. Compatibility Assessment for Migration to DB2 pureScale
... database objects and data between DB2 10.1 databases. DCW offers the following step-by-step functions to facilitate the process. 1. DCW Task Launcher– An integrated help guide, which provides step by step instructions through the conversion process. 2. Assessment Report for Conversion to DB2 pureSca ...
... database objects and data between DB2 10.1 databases. DCW offers the following step-by-step functions to facilitate the process. 1. DCW Task Launcher– An integrated help guide, which provides step by step instructions through the conversion process. 2. Assessment Report for Conversion to DB2 pureSca ...
Chapter 1
... an overarching multitenant container database. A multitenant container database (CDB) is defined as a database capable of housing one or more pluggable databases. A container is defined as a collection of data files and metadata that exist within a CDB. A pluggable database is a special type of cont ...
... an overarching multitenant container database. A multitenant container database (CDB) is defined as a database capable of housing one or more pluggable databases. A container is defined as a collection of data files and metadata that exist within a CDB. A pluggable database is a special type of cont ...
File - You have to dream before your dreams can come
... For example, your program might simply prompt users for a search condition to be used in the WHERE clause of a SELECT, UPDATE, or DELETE statement. A more complex program might allow users to choose from menus listing SQL operations, table and view names, column names, and so on. Thus, dynamic SQL ...
... For example, your program might simply prompt users for a search condition to be used in the WHERE clause of a SELECT, UPDATE, or DELETE statement. A more complex program might allow users to choose from menus listing SQL operations, table and view names, column names, and so on. Thus, dynamic SQL ...
Unle ashing the Full Potenti alof the ORA CL E DBMS byLever
... fact, the algorithm for computing hash values has changed in Oracle10g. The hash value compatible with previous releases is available in the column OLD_HASH_VALUE of the views V$SQL and V$SQLAREA. Merely the hash value is emitted to trace files. Since Statspack stuck with the “old school” hash value ...
... fact, the algorithm for computing hash values has changed in Oracle10g. The hash value compatible with previous releases is available in the column OLD_HASH_VALUE of the views V$SQL and V$SQLAREA. Merely the hash value is emitted to trace files. Since Statspack stuck with the “old school” hash value ...
Module 1: Introduction
... Forms of authorization to modify the database schema (covered in Chapter 8): Index - allows creation and deletion of indices. Resources - allows creation of new relations. Alteration - allows addition or deletion of attributes in a relation. ...
... Forms of authorization to modify the database schema (covered in Chapter 8): Index - allows creation and deletion of indices. Resources - allows creation of new relations. Alteration - allows addition or deletion of attributes in a relation. ...
DBase

dBase (also stylized dBASE) was one of the first database management systems for microcomputers, and the most successful in its day. The dBase system includes the core database engine, a query system, a forms engine, and a programming language that ties all of these components together. dBase's underlying file format, the .dbf file, is widely used in applications needing a simple format to store structured data.dBase was originally published by Ashton-Tate for microcomputer operating system CP/M in 1980, and later ported to Apple II and IBM PC computers running DOS. On the PC platform, in particular, dBase became one of the best-selling software titles for a number of years. A major upgrade was released as dBase III, and ported to a wider variety of platforms, adding UNIX, and VMS. By the mid-1980s, Ashton-Tate was one of the ""big three"" software publishers in the early business software market, the others being Lotus Development and WordPerfect.Starting in the mid-1980s, several companies produced their own variations on the dBase product and especially the dBase programming language. These included FoxBASE+(later renamed FoxPro), Clipper, and other so-called xBase products. Many of these were technically stronger than dBase, but could not push it aside in the market. This changed with the disastrous introduction of dBase IV, whose design and stability were so poor that many users switched to other products. At the same time, there was growing use of IBM-invented SQL (Structured Query Language) in database products. Another factor was user adoption of Microsoft Windows on desktop computers. The shift toward SQL and Windows put pressure on the makers of xBase products to invest in major redesign to provide new capabilities.In spite of growing pressure to evolve, in the early 1990s xBase products constituted the leading database platform for implementing business applications. The size and impact of the xBase market did not go unnoticed, and within one year, the three top xBase firms were acquired by larger software companies. Borland purchased Ashton-Tate, Microsoft bought Fox Software, and Computer Associates acquired Nantucket. However, by the following decade most of the original xBase products had faded from prominence and several disappeared. Products known as dBase still exist, owned by dBase LLC.