LTM-10 LonTalk Module and Motherboard
... module ideal for controlling devices that may be upgraded or modified after installation, e.g., complex sensors, motor controllers, or user interfaces. The integral MIP firmware allows the module to be used as an applications processor or as a network interface for another host processor. Any host w ...
... module ideal for controlling devices that may be upgraded or modified after installation, e.g., complex sensors, motor controllers, or user interfaces. The integral MIP firmware allows the module to be used as an applications processor or as a network interface for another host processor. Any host w ...
coverage
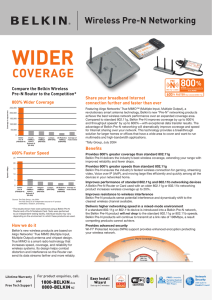
... If a standard 802.11g or 802.11b device is introduced into a Belkin Pre-N network, the Belkin Pre-N product will not drop to the standard 802.11g or 802.11b speeds. Belkin Pre-N products will continue to transmit at a link rate of 108Mbps, a result competing products cannot achieve. ...
... If a standard 802.11g or 802.11b device is introduced into a Belkin Pre-N network, the Belkin Pre-N product will not drop to the standard 802.11g or 802.11b speeds. Belkin Pre-N products will continue to transmit at a link rate of 108Mbps, a result competing products cannot achieve. ...
chap2_2ed_5July02 - Mount Holyoke College
... Routers vs. Bridges Routers + and • + arbitrary topologies can be supported, cycling is limited by TTL counters (and good routing protocols) • + provide protection against broadcast storms • - require IP address configuration (not plug and play) • - require higher packet processing • bridges do wel ...
... Routers vs. Bridges Routers + and • + arbitrary topologies can be supported, cycling is limited by TTL counters (and good routing protocols) • + provide protection against broadcast storms • - require IP address configuration (not plug and play) • - require higher packet processing • bridges do wel ...
computer network - model test paper
... guaranteed access to the token at some point. This equalizes the data transfer on the network. This is different from an Ethernet network where each workstation has equal access to grab the available bandwidth, with the possible of a node using more bandwidth than other nodes.Originally, token ring ...
... guaranteed access to the token at some point. This equalizes the data transfer on the network. This is different from an Ethernet network where each workstation has equal access to grab the available bandwidth, with the possible of a node using more bandwidth than other nodes.Originally, token ring ...
Novell IPX - Austin Community College
... In networks with hubs instead of switches, devices can communicate in only one direction at a time because they must compete for the network bandwidth. This type of communication is referred to as half-duplex communication, because it allows data to be either sent or received at one time, but not bo ...
... In networks with hubs instead of switches, devices can communicate in only one direction at a time because they must compete for the network bandwidth. This type of communication is referred to as half-duplex communication, because it allows data to be either sent or received at one time, but not bo ...
SNMP
... ACCESS read-only STATUS current DESCRIPTION "The number of input datagrams for which this entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this counter will incl ...
... ACCESS read-only STATUS current DESCRIPTION "The number of input datagrams for which this entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this counter will incl ...
ppt - Computer Science at Princeton University
... – Cute algorithmic problem: very fast lookups forwarding table destination ...
... – Cute algorithmic problem: very fast lookups forwarding table destination ...
Internetworking
... this value is smaller than the largest packet size on that network because the IP datagram needs to fit in the payload of the link-layer frame ...
... this value is smaller than the largest packet size on that network because the IP datagram needs to fit in the payload of the link-layer frame ...
Wickus and Beech`s slide
... – (UD)* Up down scheme (down to up not allowed) – (UD-DU)* if sub network is even down to up not allowed, if odd up to down not allowed – UD-(DU)* In network 0 down to up not allowed on all other networks up to down not allowed ...
... – (UD)* Up down scheme (down to up not allowed) – (UD-DU)* if sub network is even down to up not allowed, if odd up to down not allowed – UD-(DU)* In network 0 down to up not allowed on all other networks up to down not allowed ...
Optical Networking Leader Supports IEEE Standard PBB
... private line and virtual private line services, and backhauls Ethernet traffic to the IP service edge. By integrating PBB-TE, also known as IEEE standard 802.1Qay, into the Fujitsu packet optical networking portfolio, service providers can construct a single universal optical infrastructure that agg ...
... private line and virtual private line services, and backhauls Ethernet traffic to the IP service edge. By integrating PBB-TE, also known as IEEE standard 802.1Qay, into the Fujitsu packet optical networking portfolio, service providers can construct a single universal optical infrastructure that agg ...
lockheed-jan05 - Princeton University
... • Reasons why this is typically not done – Delay-based routing unsuccessful in the early days – Oscillation as routers adapt to out-of-date information – Most Internet transfers are very short-lived ...
... • Reasons why this is typically not done – Delay-based routing unsuccessful in the early days – Oscillation as routers adapt to out-of-date information – Most Internet transfers are very short-lived ...
ppt
... Link-state advertisements only in area each nodes has detailed area topology; only know direction (shortest path) to nets in other areas. ...
... Link-state advertisements only in area each nodes has detailed area topology; only know direction (shortest path) to nets in other areas. ...
ppt
... – transfer data packet and invoke handler to extract it from the network and integrate with on-going computation ...
... – transfer data packet and invoke handler to extract it from the network and integrate with on-going computation ...
VOIP Reports.pdf - 123SeminarsOnly.com
... back into an analog wave form.." The transmission of sound over a packet switched network in this manner is an order of magnitude more efficient than the transmission of sound over a circuit switched network. As mentioned before, VoIP saves bandwidth also by sending only the conversation data and no ...
... back into an analog wave form.." The transmission of sound over a packet switched network in this manner is an order of magnitude more efficient than the transmission of sound over a circuit switched network. As mentioned before, VoIP saves bandwidth also by sending only the conversation data and no ...
Lecture 10: Sorting networks
... How fast can we sort in parallel? Two arguments for an Ω(log n) lower bound: 1. Simulating a sorting network on a sequential machine gives a comparison based algorithm, so Ω(n log n) comparisons or comparators are needed. Since we can do at most n/2 comparisons at each depth in the network, the tot ...
... How fast can we sort in parallel? Two arguments for an Ω(log n) lower bound: 1. Simulating a sorting network on a sequential machine gives a comparison based algorithm, so Ω(n log n) comparisons or comparators are needed. Since we can do at most n/2 comparisons at each depth in the network, the tot ...
PCs on Control Networks 2
... for the network), it will send an election packet. This will force the election for a Master Browser. This can generate substantial amounts of broadcast traffic, as all eligible PC’s are required to respond with their capabilities to participate in the election. ...
... for the network), it will send an election packet. This will force the election for a Master Browser. This can generate substantial amounts of broadcast traffic, as all eligible PC’s are required to respond with their capabilities to participate in the election. ...
Cooperative Internet Access Sharing in Wireless Mesh
... have resulted in a set of solutions for ensuring satisfactory levels of reliability and sustainability of the user-provided Internet access sharing. The completed and the ongoing research is focused on algorithms for reliable servicing of multi-service traffic, with different packet delay tolerance, ...
... have resulted in a set of solutions for ensuring satisfactory levels of reliability and sustainability of the user-provided Internet access sharing. The completed and the ongoing research is focused on algorithms for reliable servicing of multi-service traffic, with different packet delay tolerance, ...
3rd Edition: Chapter 3
... LS packet dissemination topology map at each node route computation using Dijkstra’s algorithm ...
... LS packet dissemination topology map at each node route computation using Dijkstra’s algorithm ...
Communications and Networks
... MAN a metropolitan area network Is a high-speed network that connects local area network in a metropolitan area such as a city or town and handles the bulk of communications activity across that region. MAN typically includes one or more LANs, but covers a smaller geographic area than a WAN. Its ...
... MAN a metropolitan area network Is a high-speed network that connects local area network in a metropolitan area such as a city or town and handles the bulk of communications activity across that region. MAN typically includes one or more LANs, but covers a smaller geographic area than a WAN. Its ...