III. Dummy section heading for formatting
... may serve as a role model for defining a new internetworking architecture which permits multiple virtualized networks to run concurrently over a common infrastructure but without interference. The current IP based Internet may then simply be one of possibly many different networks all sharing a comm ...
... may serve as a role model for defining a new internetworking architecture which permits multiple virtualized networks to run concurrently over a common infrastructure but without interference. The current IP based Internet may then simply be one of possibly many different networks all sharing a comm ...
computer network - CCRI Faculty Web
... by far the most widely implemented. Standards are important because they assure that equipment that is made by different companies will be able to work together. ...
... by far the most widely implemented. Standards are important because they assure that equipment that is made by different companies will be able to work together. ...
PDF
... Mobile AdHoc Network (MANET) is a wireless network with a set of mobile nodes that can communicate with each other with no access point and without any fixed infrastructure. But mobile devices usually have limited resources (battery power, memory, CPU) which limit their transmission range. Hence, in ...
... Mobile AdHoc Network (MANET) is a wireless network with a set of mobile nodes that can communicate with each other with no access point and without any fixed infrastructure. But mobile devices usually have limited resources (battery power, memory, CPU) which limit their transmission range. Hence, in ...
The Basics of HOME NETWORKS
... Wired Equivalent Privacy (WEP) is a protocol used for encrypting packets on a wireless network. It uses a 64-bit (or 256bit, depending on the vendor) shared key algorithm. Using WEP will increase the protection on your data, but doing so will reduce the effective data rates. Truly secure? Nope! www. ...
... Wired Equivalent Privacy (WEP) is a protocol used for encrypting packets on a wireless network. It uses a 64-bit (or 256bit, depending on the vendor) shared key algorithm. Using WEP will increase the protection on your data, but doing so will reduce the effective data rates. Truly secure? Nope! www. ...
Provider Nomination Process
... b. Behavioral Health providers should go to www.ubhonline.com or call United Behavioral Health at 800-333-8724. 2. Your provider will be responsible for working with the Network Management Department. A returned application does not mean the provider has been accepted into the network. The credentia ...
... b. Behavioral Health providers should go to www.ubhonline.com or call United Behavioral Health at 800-333-8724. 2. Your provider will be responsible for working with the Network Management Department. A returned application does not mean the provider has been accepted into the network. The credentia ...
Provider Referrals to UnitedHealthcare
... b. Behavioral Health providers should go to www.ubhonline.com or call United Behavioral Health at 800-333-8724. 2. Your provider will be responsible for working with the Network Management Department. A returned application does not mean the provider has been accepted into the network. The credentia ...
... b. Behavioral Health providers should go to www.ubhonline.com or call United Behavioral Health at 800-333-8724. 2. Your provider will be responsible for working with the Network Management Department. A returned application does not mean the provider has been accepted into the network. The credentia ...
IP Addressing - School of Computing
... pairs so that the translation can be performed in reverse when answering packets arrive from the Internet. NAT’s use of port number mapping multiplexes several conversations onto the same IP address so that a single external address can be shared by many internal hosts. In some cases, a site can get ...
... pairs so that the translation can be performed in reverse when answering packets arrive from the Internet. NAT’s use of port number mapping multiplexes several conversations onto the same IP address so that a single external address can be shared by many internal hosts. In some cases, a site can get ...
part 5
... classes, encoded in IP’s ToS bits These bits can be set by ISP edge routers, handled by internal routers according to ISP ...
... classes, encoded in IP’s ToS bits These bits can be set by ISP edge routers, handled by internal routers according to ISP ...
PPT - Boston University
... The QuO Connection integrates the individual QoS agreements for the Network, Client, and Server, ...
... The QuO Connection integrates the individual QoS agreements for the Network, Client, and Server, ...
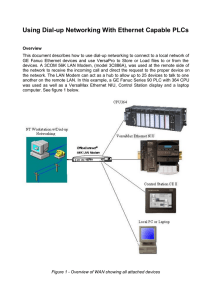
Using Dial-up Networking With Ethernet Capable PLCs
... The configuration starts with the dial-up PC. If Dial-up Networking is not already installed on the PC you will need to install it now before proceeding. Once installed, create a new entry in the phone book using your PC’s modem as the dial-out device. Specify a user name and password for authentica ...
... The configuration starts with the dial-up PC. If Dial-up Networking is not already installed on the PC you will need to install it now before proceeding. Once installed, create a new entry in the phone book using your PC’s modem as the dial-out device. Specify a user name and password for authentica ...
Why Network Computers?
... computers to access the resource it has. For example, if a printer is connected to computer A and computer B wants to print to that printer, computer A must be turned on. A computer network is referred to as client/server if (at least) one of the computers is used to "serve" other computers referre ...
... computers to access the resource it has. For example, if a printer is connected to computer A and computer B wants to print to that printer, computer A must be turned on. A computer network is referred to as client/server if (at least) one of the computers is used to "serve" other computers referre ...
List six access technologies
... unicast communications. Some offer reliable delivery (on a per-hop or per-link basis) as in WiFi (802.11) via retransmissions or redundancy codes [this is different from the end-to-end reliable TCP service]. For shared media (as in Ethernet, WiFi) the medium access control (MAC) protocol is particul ...
... unicast communications. Some offer reliable delivery (on a per-hop or per-link basis) as in WiFi (802.11) via retransmissions or redundancy codes [this is different from the end-to-end reliable TCP service]. For shared media (as in Ethernet, WiFi) the medium access control (MAC) protocol is particul ...
Internet In A Slice - Princeton University
... Reply from server to egress, routed through overlay back to client Note: switching egress nodes breaks connections ...
... Reply from server to egress, routed through overlay back to client Note: switching egress nodes breaks connections ...
networking standards and the osi model
... • EIA (Electronic Industries Alliance) is a trade organization composed of representatives from electronics manufacturing firms across the United States ...
... • EIA (Electronic Industries Alliance) is a trade organization composed of representatives from electronics manufacturing firms across the United States ...
Network Segmentation Through Policy Abstraction
... Test and development environments are usually topologically flat and most ACLs are set to Any-Any-Any (Any source IP address, over Any port, to Any destination IP address.) It has always been up to the network security team within operations to devise those policies and move them through a burdensom ...
... Test and development environments are usually topologically flat and most ACLs are set to Any-Any-Any (Any source IP address, over Any port, to Any destination IP address.) It has always been up to the network security team within operations to devise those policies and move them through a burdensom ...
Computer Networks
... service interface: operations on this protocol peer-to-peer interface: messages exchanged ...
... service interface: operations on this protocol peer-to-peer interface: messages exchanged ...
lecture2
... • Layers are the different components that need to be designed/implemented when designing/implementing networks. • Each layer responsible for a set of functions. • Top layer relies on services provided by bottom layer. • Layer makes it service available to higher layer through an interface. ...
... • Layers are the different components that need to be designed/implemented when designing/implementing networks. • Each layer responsible for a set of functions. • Top layer relies on services provided by bottom layer. • Layer makes it service available to higher layer through an interface. ...
MPLS
... and to meet policy requirements imposed by the network operator Traffic Engineering ensure available spare link capacity for re-routing traffic on failure In case of single failure the network traffic is spread across network backup links The LSPs are created independently, specifying different path ...
... and to meet policy requirements imposed by the network operator Traffic Engineering ensure available spare link capacity for re-routing traffic on failure In case of single failure the network traffic is spread across network backup links The LSPs are created independently, specifying different path ...
- Aditya College of Engineering
... connect the individual networks at different locations into one extended network. If a sales person in New York need access to a product database in Singapore. The data are stored on powerful computers called servers, are centrally housed and maintained by a system administrator. The employees have ...
... connect the individual networks at different locations into one extended network. If a sales person in New York need access to a product database in Singapore. The data are stored on powerful computers called servers, are centrally housed and maintained by a system administrator. The employees have ...
Slides - Williams Computer Science
... ranging from mobile client nodes connected via wireless links to an optical backbone networks with advanced services built into the network structure, as well as data center computing power offering cloud services ...
... ranging from mobile client nodes connected via wireless links to an optical backbone networks with advanced services built into the network structure, as well as data center computing power offering cloud services ...
packet switching
... Packet Switching (continued) • Network devices called routers read the destination address and determine how to expeditiously route packets through the networks, based on routing algorithms that are designed to minimize latency • Routers are also designed to minimize hops, the number of times a pac ...
... Packet Switching (continued) • Network devices called routers read the destination address and determine how to expeditiously route packets through the networks, based on routing algorithms that are designed to minimize latency • Routers are also designed to minimize hops, the number of times a pac ...
prj2-review
... • Overlay network – A network built on top of one or more existing networks – adds an additional layer of indirection/virtualization – changes properties in one or more areas of underlying network ...
... • Overlay network – A network built on top of one or more existing networks – adds an additional layer of indirection/virtualization – changes properties in one or more areas of underlying network ...
NFV(16) - Docbox
... – Debates on tools and limitations – Prioritization by members of data modeling work ...
... – Debates on tools and limitations – Prioritization by members of data modeling work ...