Routing in IPv6 over Low-Power Wireless Personal Area Networks
... There are three types of LoWPANs [7–9]: Ad-Hoc LoWPANs, Simple LoWPANs, and Extended LoWPANs. Adhoc LoWPANs are infrastructure less and not connected to the internet, a Simple LoWPANs is connected through one LoWPANs edge router to another Internet Protocol (IP) network. Extended LoWPANs have the Lo ...
... There are three types of LoWPANs [7–9]: Ad-Hoc LoWPANs, Simple LoWPANs, and Extended LoWPANs. Adhoc LoWPANs are infrastructure less and not connected to the internet, a Simple LoWPANs is connected through one LoWPANs edge router to another Internet Protocol (IP) network. Extended LoWPANs have the Lo ...
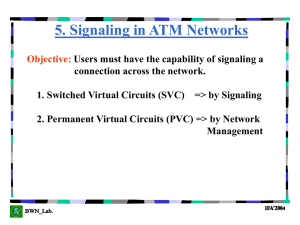
ATM End User
... UNI 3.1 only allowed the root the option of adding leaves to an existing point-to-multipoint connection. This was deemed restrictive and would not provide the flexibility for applications to take full advantage of this capability. Therefore, UNI Signaling 4.0 added a capability for leaves to join a ...
... UNI 3.1 only allowed the root the option of adding leaves to an existing point-to-multipoint connection. This was deemed restrictive and would not provide the flexibility for applications to take full advantage of this capability. Therefore, UNI Signaling 4.0 added a capability for leaves to join a ...
Communication-and-Security-in-M2M
... Application Registration • Involves local registration of an M2M application with the local SCL. • Purpose : allow the M2M application to use M2M services offered by the local SCL. As a result, the local SCL obtains context information on the registered applications. • Kmc obtained from the Kmr roo ...
... Application Registration • Involves local registration of an M2M application with the local SCL. • Purpose : allow the M2M application to use M2M services offered by the local SCL. As a result, the local SCL obtains context information on the registered applications. • Kmc obtained from the Kmr roo ...
Powerpoint
... The agent function may be located anywhere along the path, including within the sender or receiver ...
... The agent function may be located anywhere along the path, including within the sender or receiver ...
vRealize Operations Management Pack for Storage Devices 6.0.3
... A vSphere API for Storage Awareness (VASA) provider is registered as a storage provider with the vCenter Server host for your adapter instance. VASA providers gather information from arrays that support the environment and provide the data to vCenter Server system. If the VASA provider is not regist ...
... A vSphere API for Storage Awareness (VASA) provider is registered as a storage provider with the vCenter Server host for your adapter instance. VASA providers gather information from arrays that support the environment and provide the data to vCenter Server system. If the VASA provider is not regist ...
Powerpoint
... • routers compute routing tables dynamically based on information provided by other routers in the network • routers communicate topology to each other via different protocols • routers then compute one or more next hops for each destination - trying to calculate the most optimal path ...
... • routers compute routing tables dynamically based on information provided by other routers in the network • routers communicate topology to each other via different protocols • routers then compute one or more next hops for each destination - trying to calculate the most optimal path ...
Document
... except the one it arrived at Sometimes useful o Robust algorithm: e.g. military applications o Broadcast o Comparison purposes: always shortest path Selective flooding o Use only those lines that are going approximately in right direction o Still working? Network layer -- May 2004 ...
... except the one it arrived at Sometimes useful o Robust algorithm: e.g. military applications o Broadcast o Comparison purposes: always shortest path Selective flooding o Use only those lines that are going approximately in right direction o Still working? Network layer -- May 2004 ...
X-Plane to GPS
... situations it might not. The alternative is to uncheck “Broadcast configuration to entire subnet” and manually enter the IP address of the computer running X-Plane in the “Simulator IP address” field. You can find this address by selecting the X-Plane menu item Settings->Net Connections and looking ...
... situations it might not. The alternative is to uncheck “Broadcast configuration to entire subnet” and manually enter the IP address of the computer running X-Plane in the “Simulator IP address” field. You can find this address by selecting the X-Plane menu item Settings->Net Connections and looking ...
Chapter 5: Data Link Layer, MAC protocols, and Local Area Networks
... Link Layer: Introduction Some terminology: hosts and routers are nodes communication channels that ...
... Link Layer: Introduction Some terminology: hosts and routers are nodes communication channels that ...
Boswarthick_for_IIR_Dubai - Docbox
... Allow the quick creation and deployment of innovative new blended services on demand Provide flexible dimensioning, easily scaleable Allow advanced centralized network control, for charging, O&M and more Attract the third party service providers without loosing control of the network Open interfaces ...
... Allow the quick creation and deployment of innovative new blended services on demand Provide flexible dimensioning, easily scaleable Allow advanced centralized network control, for charging, O&M and more Attract the third party service providers without loosing control of the network Open interfaces ...
Module 2 - OoCities
... Q20: Telnet protocol used for logging into remote hosts. (Answer: True). Q21: One of the most important applications that were developed on the ARPANET was TELNET in 1970. (Answer: False – It was e-mail). Q22: ______________(a hacker) had written the e-mail, he was the first used the symbol “@” to s ...
... Q20: Telnet protocol used for logging into remote hosts. (Answer: True). Q21: One of the most important applications that were developed on the ARPANET was TELNET in 1970. (Answer: False – It was e-mail). Q22: ______________(a hacker) had written the e-mail, he was the first used the symbol “@” to s ...
20_otherlink
... just like Ethernet needs destination Ethernet address IP/ATM address translation done by ATM ARP (Address Resolution Protocol) ARP server in ATM network performs broadcast of ATM ARP translation request to all connected ATM devices hosts can register their ATM addresses with server to avoid lo ...
... just like Ethernet needs destination Ethernet address IP/ATM address translation done by ATM ARP (Address Resolution Protocol) ARP server in ATM network performs broadcast of ATM ARP translation request to all connected ATM devices hosts can register their ATM addresses with server to avoid lo ...
RIP version 1
... can prevent routers from sending routing updates through a router interface, but the router continues to listen and use routing updates from that neighbor. Keeping routing update messages from being sent through a router interface prevents other systems on that network from learning about routes dyn ...
... can prevent routers from sending routing updates through a router interface, but the router continues to listen and use routing updates from that neighbor. Keeping routing update messages from being sent through a router interface prevents other systems on that network from learning about routes dyn ...
Avaya Data Ports List for Products
... called a socket (discussed later). Therefore, each data stream is uniquely identified with two sockets. Source and destination sockets must be known by the source before a data stream can be sent to the destination. Some destination ports are “open” to receive data streams and are called “listening” ...
... called a socket (discussed later). Therefore, each data stream is uniquely identified with two sockets. Source and destination sockets must be known by the source before a data stream can be sent to the destination. Some destination ports are “open” to receive data streams and are called “listening” ...
PowerPoint Presentation - requirements for delivering MPLS
... • Will add application scenarios based on comments • Stitching LSPs • CE-PE: C-TE LSPs • PE-PE: non-TE LSPs (LDP) • PE-CE: C-TE LSPs ...
... • Will add application scenarios based on comments • Stitching LSPs • CE-PE: C-TE LSPs • PE-PE: non-TE LSPs (LDP) • PE-CE: C-TE LSPs ...
PPT Version - Internet Engineering Task Force
... • bottleneck policers: active research area since 1999 ...
... • bottleneck policers: active research area since 1999 ...
Ip Addressing and Subnetting Workbook v1_2.pmd
... When you take a single network such as 192.100.10.0 and divide it into five smaller networks (192.100.10.16, 192.100.10.32, 192.100.10.48, 192.100.10.64, 192.100.10.80) the outside world still sees the network as 192.100.10.0, but the internal computers and routers see five smaller subnetworks. Each ...
... When you take a single network such as 192.100.10.0 and divide it into five smaller networks (192.100.10.16, 192.100.10.32, 192.100.10.48, 192.100.10.64, 192.100.10.80) the outside world still sees the network as 192.100.10.0, but the internal computers and routers see five smaller subnetworks. Each ...
Chapter 3: Wireless Access Point Web Management
... rather than at the farthest corner of a wireless network. Multiple TPL-310AP adapters can be used to cover larger areas without increasing wireless radiation and through the use of powerline as your network backbone with no additional wiring required. In addition, any Ethernet-enabled device may be ...
... rather than at the farthest corner of a wireless network. Multiple TPL-310AP adapters can be used to cover larger areas without increasing wireless radiation and through the use of powerline as your network backbone with no additional wiring required. In addition, any Ethernet-enabled device may be ...
vSphere-5.5 L2 Starting on Monday
... Creating or Editing Backup Jobs Setting the Retention Policy Managing Backup Jobs - Editing a Backup Job - Cloning a Backup Job Enabling or Disabling a Backup Job - Locking and Unlocking a Backup Restoring Backups Deleting a Backup ...
... Creating or Editing Backup Jobs Setting the Retention Policy Managing Backup Jobs - Editing a Backup Job - Cloning a Backup Job Enabling or Disabling a Backup Job - Locking and Unlocking a Backup Restoring Backups Deleting a Backup ...
Case Studies on IP-based Interconnection for Voice Services
... for IPvIC. If, however, operators cannot agree to a common solution or if some operators refuse to offer IPvIC at all, there might be a need for regulatory intervention. The second aspect of relevance is the time frame for the migration to IPvIC. Operators may migrate their voice telephony networks ...
... for IPvIC. If, however, operators cannot agree to a common solution or if some operators refuse to offer IPvIC at all, there might be a need for regulatory intervention. The second aspect of relevance is the time frame for the migration to IPvIC. Operators may migrate their voice telephony networks ...
Windows 3.1 Setup for
... Click on Next > (again) to make your computer a member of WORKGROUP Click on Finish In the Network Settings Change window, click on Yes to restart your computer ...
... Click on Next > (again) to make your computer a member of WORKGROUP Click on Finish In the Network Settings Change window, click on Yes to restart your computer ...
The OSI Model
... routing protocol based on link state routing. Its domain is also an autonomous system Dividing an AS into areas to handle routing efficiently and in a timely manner ...
... routing protocol based on link state routing. Its domain is also an autonomous system Dividing an AS into areas to handle routing efficiently and in a timely manner ...
DICENTIS Wireless Conference System
... 9. Ethernet cable/PoE+: - Is used for connection to the Ethernet. - PoE+ is used for powering the DCNM-WAP. 10. Ethernet network switch: - Is used for routing of the system data via Ethernet. 11. HD Conference Dome: is used to capture the video of a participant speaking. 12. Coax cable: transports t ...
... 9. Ethernet cable/PoE+: - Is used for connection to the Ethernet. - PoE+ is used for powering the DCNM-WAP. 10. Ethernet network switch: - Is used for routing of the system data via Ethernet. 11. HD Conference Dome: is used to capture the video of a participant speaking. 12. Coax cable: transports t ...
From Overlays to Clouds - Distributed Systems and Networks Lab
... • Can the Internet be an underlying network for a live TV service? – Live channel transport (Business to Business) – The virtual cable company (Business to Consumer) – Next Generation TV (Interactivity) ...
... • Can the Internet be an underlying network for a live TV service? – Live channel transport (Business to Business) – The virtual cable company (Business to Consumer) – Next Generation TV (Interactivity) ...