Route Optimization
... (Optional) Parameter used to specify the RIP seed metric for the redistributed route. When you are redistributing into RIP, this value is not specified and no value is specified using the defaultmetric router configuration command, then the default metric is 0, which is interpreted as infinity, and ...
... (Optional) Parameter used to specify the RIP seed metric for the redistributed route. When you are redistributing into RIP, this value is not specified and no value is specified using the defaultmetric router configuration command, then the default metric is 0, which is interpreted as infinity, and ...
Routing Concept
... Routing Algorithm: Static Route • Manually configuration routing table • Can’t react dynamically to network change such as router’s crash • Work well with small network or simple topology • Unix hosts use command route to add an entry point to point connection route to this way only, no need for up ...
... Routing Algorithm: Static Route • Manually configuration routing table • Can’t react dynamically to network change such as router’s crash • Work well with small network or simple topology • Unix hosts use command route to add an entry point to point connection route to this way only, no need for up ...
MuON: Epidemic Based Mutual Anonymity
... Unlinkability of initiator and responder means that the initiator and responder cannot be identified as communicating with each other, even though they can be identified as participating in some communication. Different approaches have successfully achieved various forms of anonymity. In the simples ...
... Unlinkability of initiator and responder means that the initiator and responder cannot be identified as communicating with each other, even though they can be identified as participating in some communication. Different approaches have successfully achieved various forms of anonymity. In the simples ...
Applying SDN Architecture to 5G Slicing
... (NBI), they offer client entities (applications, users, tenants) the ability to interact with network control and to manage-control (i.e. program) services. The extent of management-control rights and capabilities depends on the role of the respective entity using an NBI. The term virtualization is ...
... (NBI), they offer client entities (applications, users, tenants) the ability to interact with network control and to manage-control (i.e. program) services. The extent of management-control rights and capabilities depends on the role of the respective entity using an NBI. The term virtualization is ...
Introduction Uses of Computer Networks
... An ISP (Internet Service Provider) network is also a WAN. Customers buy connectivity from the ISP to use it. ...
... An ISP (Internet Service Provider) network is also a WAN. Customers buy connectivity from the ISP to use it. ...
- Lecturer
... introduces lawsuits and seeks legal changes – CDs, mp3 players introduce restrictions and become more expensive ...
... introduces lawsuits and seeks legal changes – CDs, mp3 players introduce restrictions and become more expensive ...
USB/IP - a Peripheral Bus Extension for Device Sharing
... uses the low-level control protocols of the peripheral devices, which are the same as those of locally attached devices. These protocols, which are defined by several standards, are independent of the operating system implementation. By using these protocols for sharing, computers with different ope ...
... uses the low-level control protocols of the peripheral devices, which are the same as those of locally attached devices. These protocols, which are defined by several standards, are independent of the operating system implementation. By using these protocols for sharing, computers with different ope ...
Multimedia Streaming File
... Today’s Internet multimedia applications use application-level techniques to mitigate (as best possible) effects of delay, loss Multimedia Networking - Dr. Hussein Al-Bahadili ...
... Today’s Internet multimedia applications use application-level techniques to mitigate (as best possible) effects of delay, loss Multimedia Networking - Dr. Hussein Al-Bahadili ...
Industrial Ethernet Switching
... plant or machines must be optimally utilized and any downtimes must be minimized. All the production and management processes must perfectly interact. ...
... plant or machines must be optimally utilized and any downtimes must be minimized. All the production and management processes must perfectly interact. ...
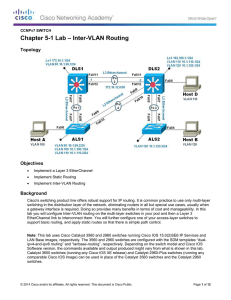
Lab 5-1 Inter-VLAN Routing
... Cisco's switching product line offers robust support for IP routing. It is common practice to use only multi-layer switching in the distribution layer of the network, eliminating routers in all but special use cases, usually when a gateway interface is required. Doing so provides many benefits in te ...
... Cisco's switching product line offers robust support for IP routing. It is common practice to use only multi-layer switching in the distribution layer of the network, eliminating routers in all but special use cases, usually when a gateway interface is required. Doing so provides many benefits in te ...
Understanding Carrier Ethernet Throughput
... are two main protocols at the transport layer for the IP protocol suite — the transport control protocol (TCP) and the user datagram protocol (UDP). These two protocols are the basis of all modern data communications. Depending on the application, it will either use TCP or UDP. UDP, a more basic tra ...
... are two main protocols at the transport layer for the IP protocol suite — the transport control protocol (TCP) and the user datagram protocol (UDP). These two protocols are the basis of all modern data communications. Depending on the application, it will either use TCP or UDP. UDP, a more basic tra ...
a survey of integrating ip mobility protocols and mobile ad hoc
... integrate fixed and mobile networks. The most known standard for IP mobility support is Mobile IP [1], which is the best and the most frequently adopted solution for supporting IP macro-mobility. It is proposed by IETF to enable the mobile node to access Internet and roam freely between different su ...
... integrate fixed and mobile networks. The most known standard for IP mobility support is Mobile IP [1], which is the best and the most frequently adopted solution for supporting IP macro-mobility. It is proposed by IETF to enable the mobile node to access Internet and roam freely between different su ...
PDF
... You must remove the ASA-configured name for Management 0/0; if it is configured on the ASA, then the IPS address must be on the same network as the ASA, and that excludes any networks already configured on other ASA interfaces. If the name is not configured, then the IPS address can be on any networ ...
... You must remove the ASA-configured name for Management 0/0; if it is configured on the ASA, then the IPS address must be on the same network as the ASA, and that excludes any networks already configured on other ASA interfaces. If the name is not configured, then the IPS address can be on any networ ...
W301A User Guide
... W301A is a wireless Access Point based on the latest IEEE802.11n standard while at the same time being backwards compatible with IEEE802.11b/g devices. Adopting the advanced “Multiple in and Multiple out” (MIMO) technology, it can provide a maximum of 300Mbps stable transmitting rate for wireless us ...
... W301A is a wireless Access Point based on the latest IEEE802.11n standard while at the same time being backwards compatible with IEEE802.11b/g devices. Adopting the advanced “Multiple in and Multiple out” (MIMO) technology, it can provide a maximum of 300Mbps stable transmitting rate for wireless us ...
Detecting Good Neighbor Nodes and Finding
... An Ad Hoc Network (MANET) is a wireless network consisting of mobile nodes, which can communicate with each other without any infrastructure support. In these networks, nodes typically cooperate with each other, by forwarding packets for nodes which are not in the communication range of the source n ...
... An Ad Hoc Network (MANET) is a wireless network consisting of mobile nodes, which can communicate with each other without any infrastructure support. In these networks, nodes typically cooperate with each other, by forwarding packets for nodes which are not in the communication range of the source n ...
Slide 1
... • 1st-Generation VPN – IPsec – IP Address-Based Tunnels – All-or-Nothing Network Access for Employees ...
... • 1st-Generation VPN – IPsec – IP Address-Based Tunnels – All-or-Nothing Network Access for Employees ...
Slide 1
... Sends an update about network 10.1.0.0 out the Serial 0/0/0 interface with a metric of 1 Sends an update about network 10.2.0.0 out the FastEthernet 0/0 interface with a metric of 1 Receives an update from R2 about network 10.3.0.0 on Serial 0/0/0 with a metric of 1 Stores network 10.3.0.0 i ...
... Sends an update about network 10.1.0.0 out the Serial 0/0/0 interface with a metric of 1 Sends an update about network 10.2.0.0 out the FastEthernet 0/0 interface with a metric of 1 Receives an update from R2 about network 10.3.0.0 on Serial 0/0/0 with a metric of 1 Stores network 10.3.0.0 i ...
Huawei S1700 Switch Data Sheet
... user access and are cost-effective. The S1700/S1720 MAC address table supports up to 8K/16K of MAC addresses, making it easy to expand networks and deploy new services. The S1700 support layer 3 static routingforwarding which include IPv4 and IPv6 protocols. ...
... user access and are cost-effective. The S1700/S1720 MAC address table supports up to 8K/16K of MAC addresses, making it easy to expand networks and deploy new services. The S1700 support layer 3 static routingforwarding which include IPv4 and IPv6 protocols. ...
Keywords - multi-touch, RFID, interactive, front-side
... messages to each node in the network, the individual network nodes forward packets to and from each other. It typically refers to any set of networks where all devices have equal status on a network and are free to associate with any other ad hoc network device in link range. In the Windows operatin ...
... messages to each node in the network, the individual network nodes forward packets to and from each other. It typically refers to any set of networks where all devices have equal status on a network and are free to associate with any other ad hoc network device in link range. In the Windows operatin ...
UbiCom Book Figures - Queen Mary University of London
... • Mobile devices boot from ROM & load data more slowly. • On the other hand, ROM memory uses less power ...
... • Mobile devices boot from ROM & load data more slowly. • On the other hand, ROM memory uses less power ...
Sockets Interface Java (C)
... Address plan and VLAN configuration Routing and NAT DNS server DHCP server Securing the network – ACL ...
... Address plan and VLAN configuration Routing and NAT DNS server DHCP server Securing the network – ACL ...
Power over Ethernet (PoE)
... • VTP Client allows only the acceptance of VLAN’s from the server. Information is not stored in memory. • VTP Transparent mode allows the creation or deletion of VLAN’s of local significance only. VLAN information is stored in switch memory. Will pass VTP information to other switches within the sam ...
... • VTP Client allows only the acceptance of VLAN’s from the server. Information is not stored in memory. • VTP Transparent mode allows the creation or deletion of VLAN’s of local significance only. VLAN information is stored in switch memory. Will pass VTP information to other switches within the sam ...