OSI Network Layer
... fragmenting the packet or fragmentation: the process of an intermediary device usually a router - will need to split up a packet when forwarding it from one media to a media with a smaller MTU 思科网络技术学院理事会. ...
... fragmenting the packet or fragmentation: the process of an intermediary device usually a router - will need to split up a packet when forwarding it from one media to a media with a smaller MTU 思科网络技术学院理事会. ...
20.4 Universal Service in a Heterogeneous World
... A large organization with diverse networking requirements needs multiple physical networks If the organization chooses the type of network that is best for each task, the organization will have several types of networks ...
... A large organization with diverse networking requirements needs multiple physical networks If the organization chooses the type of network that is best for each task, the organization will have several types of networks ...
2 DEvelopment tools - INFN-LNF
... levels of programming, from device drivers to file system and LAN. From the standpoint of a user's process there is no difference between a local call and a call from the network and hence all resources on all network nodes are transparently available everywhere on the network. FlexCtrl strongly use ...
... levels of programming, from device drivers to file system and LAN. From the standpoint of a user's process there is no difference between a local call and a call from the network and hence all resources on all network nodes are transparently available everywhere on the network. FlexCtrl strongly use ...
WE-P1 Custom HMI for Commercial SCADA
... levels of programming, from device drivers to file system and LAN. From the standpoint of a user's process there is no difference between a local call and a call from the network and hence all resources on all network nodes are transparently available everywhere on the network. FlexCtrl strongly use ...
... levels of programming, from device drivers to file system and LAN. From the standpoint of a user's process there is no difference between a local call and a call from the network and hence all resources on all network nodes are transparently available everywhere on the network. FlexCtrl strongly use ...
Ad hoc on-demand Distance Vector Routing Protocol Based on Load Balance
... all other RREQ coming in this interval. After σt time, it calls the optimization function to determine the best path to select and send RREP. It also stores some other relatively inferior paths as backup paths, which may be used if there is some network failure, thereby avoiding energy and time wast ...
... all other RREQ coming in this interval. After σt time, it calls the optimization function to determine the best path to select and send RREP. It also stores some other relatively inferior paths as backup paths, which may be used if there is some network failure, thereby avoiding energy and time wast ...
Cybersecurity in ALICE Detector Control System - Indico
... On gateways the standard Windows user interface is replaced by custom shell (TSSHELL) User cannot interact with the operating system anymore Only actions granted to user can be performed (standard users can only start the PVSSII UI) ...
... On gateways the standard Windows user interface is replaced by custom shell (TSSHELL) User cannot interact with the operating system anymore Only actions granted to user can be performed (standard users can only start the PVSSII UI) ...
olug_june_2013_linux_kvm
... requires a modified QEMU although work is underway to get the required changes upstream. ...
... requires a modified QEMU although work is underway to get the required changes upstream. ...
presentation source
... • Remember: 90 Mbps Sparc 20 to Sparc 20 • Scenario: Two machines doing FTP (to /dev/null) – Machine A: Sun Ultra-1 running Solaris 2.5.1, 155 Mbps fiber ATM NIC ...
... • Remember: 90 Mbps Sparc 20 to Sparc 20 • Scenario: Two machines doing FTP (to /dev/null) – Machine A: Sun Ultra-1 running Solaris 2.5.1, 155 Mbps fiber ATM NIC ...
wireless mesh networks
... Fig. Wireless Mesh Network Motivation The idea of exploiting multiple channels is appealing in wireless mesh networks because of their high capacity requirements to support backbone traffic. Goal To reduce interference of the wireless mesh networks by using multi-channel. ...
... Fig. Wireless Mesh Network Motivation The idea of exploiting multiple channels is appealing in wireless mesh networks because of their high capacity requirements to support backbone traffic. Goal To reduce interference of the wireless mesh networks by using multi-channel. ...
Token Ring
... designed for a limited geographic area such as a building or a campus. Although a LAN can be used as an isolated network, most LANs today are also linked to a wide area network (WAN) or the Internet. A computer connected via a LAN to the Internet needs all the 5 layers of the TCP/IP model. The three ...
... designed for a limited geographic area such as a building or a campus. Although a LAN can be used as an isolated network, most LANs today are also linked to a wide area network (WAN) or the Internet. A computer connected via a LAN to the Internet needs all the 5 layers of the TCP/IP model. The three ...
4.new-mj-hawaii
... univ-to-univ traffic) and visibility into Internet BGP for the first time since NSFnet ...
... univ-to-univ traffic) and visibility into Internet BGP for the first time since NSFnet ...
Wi-Fi EOC Slave Quick Start Guide
... The slave lets you access your network from virtually anywhere within the operating range of your wireless network. However, the operating distance or range of your wireless connection can vary significantly depending on the physical placement of your slave. For example, the thickness and number of ...
... The slave lets you access your network from virtually anywhere within the operating range of your wireless network. However, the operating distance or range of your wireless connection can vary significantly depending on the physical placement of your slave. For example, the thickness and number of ...
What Is a Network?
... collaborators are on a network. Individuals creating separate parts of an annual report or a business plan, for example, can either transmit their data files to a central resource for compilation or use a workgroup software application to create and modify the entire document, without any exchang ...
... collaborators are on a network. Individuals creating separate parts of an annual report or a business plan, for example, can either transmit their data files to a central resource for compilation or use a workgroup software application to create and modify the entire document, without any exchang ...
Protection and Fault Recovery at Internet Peering Points
... A LinkTrace Message (LTM) is sent to a multicast MAC address; payload contains a target unicast MAC address Each MIP at the same MD level responds with a LinkTrace Response (LTR). Message is then forwarded to the next hop until it reaches the destination MAC Originating MEP collects all the LTR mess ...
... A LinkTrace Message (LTM) is sent to a multicast MAC address; payload contains a target unicast MAC address Each MIP at the same MD level responds with a LinkTrace Response (LTR). Message is then forwarded to the next hop until it reaches the destination MAC Originating MEP collects all the LTR mess ...
LECTURE 10
... Each MS has to still wait for a period of DIFS Each MS chooses a random time of back-off within a contention window Each MS decrements the back-off. Once the back-off value becomes zero, if the medium is idle, the MS can transmit The MS with the smallest back-off time will get to transmit All other ...
... Each MS has to still wait for a period of DIFS Each MS chooses a random time of back-off within a contention window Each MS decrements the back-off. Once the back-off value becomes zero, if the medium is idle, the MS can transmit The MS with the smallest back-off time will get to transmit All other ...
Chapter 7
... means transmission in an unsequenced frame. Protocol: A value to indicate the upper-layer protocol that will receive the data. Data: The network layer PDU, typically an IPv4 packet. FCS: Contains a 16-bit (or 32-bit) error detection code. ...
... means transmission in an unsequenced frame. Protocol: A value to indicate the upper-layer protocol that will receive the data. Data: The network layer PDU, typically an IPv4 packet. FCS: Contains a 16-bit (or 32-bit) error detection code. ...
OmniSwitch 6850E Datasheet
... The Alcatel-Lucent OmniSwitch™ 6850E Stackable LAN Switch (SLS) family offers advanced stackable gigabit Ethernet switches for the enterprise networks. The OmniSwitch 6850E is available in 24 and 48 port configurations and provides wire-rate layer-2 and layer-3 switching simultaneously for IPv4 and ...
... The Alcatel-Lucent OmniSwitch™ 6850E Stackable LAN Switch (SLS) family offers advanced stackable gigabit Ethernet switches for the enterprise networks. The OmniSwitch 6850E is available in 24 and 48 port configurations and provides wire-rate layer-2 and layer-3 switching simultaneously for IPv4 and ...
Internet services
... • Internet is a global public communication system. It accommodates many various user services referred as Internet services. • The most frequently used Internet services: – Internet Electronic Mail Service – Remote access to file systems and file transfer service – Remote session service - remote t ...
... • Internet is a global public communication system. It accommodates many various user services referred as Internet services. • The most frequently used Internet services: – Internet Electronic Mail Service – Remote access to file systems and file transfer service – Remote session service - remote t ...
Document
... – But this is all done on top of IP, which is connectionless, so we’ll need to implement quite a bit of extra logic in TCP to get the connection-oriented characteristics out of an underlying connectionless medium ...
... – But this is all done on top of IP, which is connectionless, so we’ll need to implement quite a bit of extra logic in TCP to get the connection-oriented characteristics out of an underlying connectionless medium ...
Lecture 1 - Project Open
... -Why digital? - and how conventional analog media (voice, images, video) are converted to digital. -Modulation and modems. -The different kinds of communication networks supporting the Internet; protocol stacks. ...
... -Why digital? - and how conventional analog media (voice, images, video) are converted to digital. -Modulation and modems. -The different kinds of communication networks supporting the Internet; protocol stacks. ...
AR-M207
... Printing/Scanning Expansion Kit allows easy printer sharing through your office network. The AR-NB3 also gives you PCL 6/5e printer language emulations. For compatibility with more fonts and better graphics handling, PostScript 3 emulation is available with the optional AR-PK1N PS3 Expansion Kit. ...
... Printing/Scanning Expansion Kit allows easy printer sharing through your office network. The AR-NB3 also gives you PCL 6/5e printer language emulations. For compatibility with more fonts and better graphics handling, PostScript 3 emulation is available with the optional AR-PK1N PS3 Expansion Kit. ...
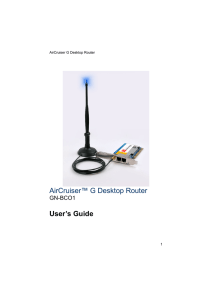
AirCruiser™ G Desktop Router User`s Guide
... The antenna that comes included with the AirCruiser G Desktop Router is unlike any other - there is a blue LED atop the tip which will flash at intervals – fast flashing indicates faster transmissions. It has a beefed up 3dBi gain compared with the 2dBi antennas that are bundled with most standard r ...
... The antenna that comes included with the AirCruiser G Desktop Router is unlike any other - there is a blue LED atop the tip which will flash at intervals – fast flashing indicates faster transmissions. It has a beefed up 3dBi gain compared with the 2dBi antennas that are bundled with most standard r ...
Follow this link to Network
... implemented as a coaxial cable (ThinLAN) or using telephonestyle twisted pair cabling (Ethertwist). The characteristics of an Ethernet network are illustrated in the slide. Ethernet allows multiple stations to access the transmission medium without prior coordination, using a carrier sense access me ...
... implemented as a coaxial cable (ThinLAN) or using telephonestyle twisted pair cabling (Ethertwist). The characteristics of an Ethernet network are illustrated in the slide. Ethernet allows multiple stations to access the transmission medium without prior coordination, using a carrier sense access me ...