Chapter 8 - Weber State University
... The administrative distance (AD) is used to rate the trustworthiness of routing information received on a router from a neighbor router. An administrative distance is an integer from 0 to 255, where 0 is the most trusted and 255 means no traffic will be passed via this route. If a router receives tw ...
... The administrative distance (AD) is used to rate the trustworthiness of routing information received on a router from a neighbor router. An administrative distance is an integer from 0 to 255, where 0 is the most trusted and 255 means no traffic will be passed via this route. If a router receives tw ...
Chapter 15 Local Area Networks
... compared to software-based router • Flow-based switch tries to enhance performance by identifying flows of IP packets —Same source and destination —Done by observing ongoing traffic or using a special flow label in packet header (IPv6) —Once flow is identified, predefined route can be ...
... compared to software-based router • Flow-based switch tries to enhance performance by identifying flows of IP packets —Same source and destination —Done by observing ongoing traffic or using a special flow label in packet header (IPv6) —Once flow is identified, predefined route can be ...
John V overview of architecure elements
... VLAN ids may be translated at some forwarding points depending on hardware capabilities. A network connection is a VLAN between Ethernets on Access sites. Some access may be on untagged Ethernet that is mapped to VLAN at the Access port. ...
... VLAN ids may be translated at some forwarding points depending on hardware capabilities. A network connection is a VLAN between Ethernets on Access sites. Some access may be on untagged Ethernet that is mapped to VLAN at the Access port. ...
[2016-NEW!] 200-120 New Questions and Answers -
... A switch is configured with all ports assigned to vlan 2 with full duplex FastEthernet to segment existing departmental traffic. What is the effect of adding switch ports to a new VLAN on the switch? A. B. C. D. ...
... A switch is configured with all ports assigned to vlan 2 with full duplex FastEthernet to segment existing departmental traffic. What is the effect of adding switch ports to a new VLAN on the switch? A. B. C. D. ...
Literature Review - Computer Science
... 2.1.4 Possible FireWire configurations for the Surround Sound System ........................................ 5 2.2 Ethernet AVB ................................................................................................................................. 5 2.2.1 Timing and Synchronisation ...... ...
... 2.1.4 Possible FireWire configurations for the Surround Sound System ........................................ 5 2.2 Ethernet AVB ................................................................................................................................. 5 2.2.1 Timing and Synchronisation ...... ...
1-network
... flows from sender to receiver Switching: Arriving packet is moved to the appropriate output link Call Setup: Handshake prior to routing packets (required by some ...
... flows from sender to receiver Switching: Arriving packet is moved to the appropriate output link Call Setup: Handshake prior to routing packets (required by some ...
Networking Components and Devices
... perhaps the most simple and common network device used today: the hub. ...
... perhaps the most simple and common network device used today: the hub. ...
Technology Infrastructure: The Internet and the World Wide Web
... – Independent networks should not require any internal changes to be connected to the network – Packets that do not arrive at their destinations must be retransmitted from their source network – Router computers act as receive-and-forward devices – No global control exists over the network E-Commerc ...
... – Independent networks should not require any internal changes to be connected to the network – Packets that do not arrive at their destinations must be retransmitted from their source network – Router computers act as receive-and-forward devices – No global control exists over the network E-Commerc ...
SEMESTER 1 Chapter 5
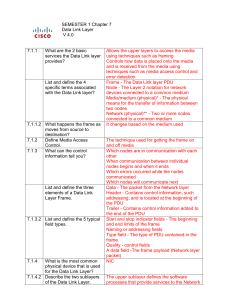
... * The Layer 2 protocol used for a particular network topology is determined by - the technology used to implement that topology. - the size of the network – - the number of hosts - the geographic scope - the services to be provided over the network. * The Data Link layer provides a means for exchang ...
... * The Layer 2 protocol used for a particular network topology is determined by - the technology used to implement that topology. - the size of the network – - the number of hosts - the geographic scope - the services to be provided over the network. * The Data Link layer provides a means for exchang ...
mobopts-4
... solved solely by existing mobility management protocols – Requires SA between mobility agents across domains – Different domains may use different M-M protocols (e.g., CMIPPMIP handover optimization) ...
... solved solely by existing mobility management protocols – Requires SA between mobility agents across domains – Different domains may use different M-M protocols (e.g., CMIPPMIP handover optimization) ...
CDD-564/LEN
... Header compression reduces the bandwidth required for Voice over Internet Protocol (VoIP) by as much as 60%. Example: A G.729 voice codec, operating at 8 kbps, requires 32 kbps bandwidth once encapsulated into an IP/UDP/RTP frame. With IP/UDP/RTP header compression, the same voice call needs only 10 ...
... Header compression reduces the bandwidth required for Voice over Internet Protocol (VoIP) by as much as 60%. Example: A G.729 voice codec, operating at 8 kbps, requires 32 kbps bandwidth once encapsulated into an IP/UDP/RTP frame. With IP/UDP/RTP header compression, the same voice call needs only 10 ...
No Slide Title
... between networks, rather than within networks. • Home networks use a wireless or wired Internet Protocol router. An IP router, such as a digital subscriber line (DSL) or a cable modem broadband router, joins the home’s LAN to the WAN of the Internet. • Broadband routers combine the functions of a ro ...
... between networks, rather than within networks. • Home networks use a wireless or wired Internet Protocol router. An IP router, such as a digital subscriber line (DSL) or a cable modem broadband router, joins the home’s LAN to the WAN of the Internet. • Broadband routers combine the functions of a ro ...
RARP / BOOTP / DHCP
... and broadcast (possibility to send a frame to all hosts on the network) the following protocols have evolved over time for the dynamic assignment of IP addresses. 1. RARP (Reverse ARP): RARP (defined in RFC903) is an early protocol for dynamic IP address assignment in Ethernet networks. RARP is seve ...
... and broadcast (possibility to send a frame to all hosts on the network) the following protocols have evolved over time for the dynamic assignment of IP addresses. 1. RARP (Reverse ARP): RARP (defined in RFC903) is an early protocol for dynamic IP address assignment in Ethernet networks. RARP is seve ...
web.cs.sunyit.edu
... Repeaters and Hubs • Repeaters – Operate in Physical OSI model layer – No means to interpret data – Regenerate signal ...
... Repeaters and Hubs • Repeaters – Operate in Physical OSI model layer – No means to interpret data – Regenerate signal ...
Document
... Network layer - responsible for creating maintaining and ending network connections. Transfers a data packet from node to node within the network. Transport layer - provides an end-to-end, error-free network connection. Makes sure the data arrives at the destination exactly as it left the source. ...
... Network layer - responsible for creating maintaining and ending network connections. Transfers a data packet from node to node within the network. Transport layer - provides an end-to-end, error-free network connection. Makes sure the data arrives at the destination exactly as it left the source. ...
a new SoC paradigm
... connect at every cycle. Moreover, the compiler pipelines the long wires to support high shared-medium clock frequency. networks. Indirect or switch-based networks offer an alternative to direct networks for scalable interconnection design. In these networks, a connection between nodes must go throug ...
... connect at every cycle. Moreover, the compiler pipelines the long wires to support high shared-medium clock frequency. networks. Indirect or switch-based networks offer an alternative to direct networks for scalable interconnection design. In these networks, a connection between nodes must go throug ...
The Cutting EDGE of IP Router Configuration
... through a database using explicit local rules. However, for many existing enterprise networks, the routers’ configuration state is the “database”1 . We believe that a detailed analysis of this configuration state should play an important role in the move toward automation. A. Target Automated Provis ...
... through a database using explicit local rules. However, for many existing enterprise networks, the routers’ configuration state is the “database”1 . We believe that a detailed analysis of this configuration state should play an important role in the move toward automation. A. Target Automated Provis ...
P4: Specifying data planes
... • Programming the control plane: that is Software-Defined Networking • A tool for third parties to program the network • A language for: • distributed computations • network middleboxes (NFV) • network operating systems ...
... • Programming the control plane: that is Software-Defined Networking • A tool for third parties to program the network • A language for: • distributed computations • network middleboxes (NFV) • network operating systems ...
Intel® Ethernet Converged Network Adapters X710 10/40 GbE
... • Enhanced QoS feature by providing weighted round-robin servicing for the Tx data • Offloads the data-sorting functionality from the Hypervisor to the network silicon, improving data throughput and CPU usage • Provides QoS feature on the Tx data by providing round-robin servicing and preventing hea ...
... • Enhanced QoS feature by providing weighted round-robin servicing for the Tx data • Offloads the data-sorting functionality from the Hypervisor to the network silicon, improving data throughput and CPU usage • Provides QoS feature on the Tx data by providing round-robin servicing and preventing hea ...
Peer-to-Peer Networks and
... Tim Caserza, -3download multiple files at once at the same time as being a server and uploading multiple files to other users. Unfortunately, the Napster centralized server scheme led to its downfall when it caught the eye of Recording Industry Association of America. The RIAA and its influence on ...
... Tim Caserza, -3download multiple files at once at the same time as being a server and uploading multiple files to other users. Unfortunately, the Napster centralized server scheme led to its downfall when it caught the eye of Recording Industry Association of America. The RIAA and its influence on ...
ns-2 Network Simulator
... A system is modeled as a set of entities that affect each other via events Each entity can have a set of states Events happen at specific points in time and trigger state changes in the system Very general technique, well-suited to modeling discrete systems and networks Simulator has an event list, ...
... A system is modeled as a set of entities that affect each other via events Each entity can have a set of states Events happen at specific points in time and trigger state changes in the system Very general technique, well-suited to modeling discrete systems and networks Simulator has an event list, ...
990204-SPAININET99-HB
... Collaborations Building peer to peer relationships Looking for similar goals/objectives and similar constituencies Mechanism: Memoranda of Understanding Signed: CANARIE, Stichting SURF, NORDUnet In process: TERENA, SingAREN, JAIRC, APAN and others ...
... Collaborations Building peer to peer relationships Looking for similar goals/objectives and similar constituencies Mechanism: Memoranda of Understanding Signed: CANARIE, Stichting SURF, NORDUnet In process: TERENA, SingAREN, JAIRC, APAN and others ...
Voice over Mobile IP
... [3] M. Handley et al., “SIP: Session Initiation Protocol,” IETF RFC 2543, March 1999. [4] C. Perkins, “IP Mobility Support,” RFC 2002, IETF, October 1996. [5] Melody Moh, Gregorie Berquin, and Yanjun Chen, “Mobile IP Telephony: Mobility Support of SIP,” Eighth International Conference on Computer Co ...
... [3] M. Handley et al., “SIP: Session Initiation Protocol,” IETF RFC 2543, March 1999. [4] C. Perkins, “IP Mobility Support,” RFC 2002, IETF, October 1996. [5] Melody Moh, Gregorie Berquin, and Yanjun Chen, “Mobile IP Telephony: Mobility Support of SIP,” Eighth International Conference on Computer Co ...



![[2016-NEW!] 200-120 New Questions and Answers -](http://s1.studyres.com/store/data/000108812_1-bba6a7d69201d6f7aa4d0f7684ac7604-300x300.png)