
PPT Version
... path computation may be made by PCE physically distinct from the computed path path computed by PCE may be complete: full explicit path of strict hops partial: mix of strict & loose hops (may be an abstract node such as an AS) PCE path computation can be used in conjunction with other path ...
... path computation may be made by PCE physically distinct from the computed path path computed by PCE may be complete: full explicit path of strict hops partial: mix of strict & loose hops (may be an abstract node such as an AS) PCE path computation can be used in conjunction with other path ...
Description
... A service request is used to change the ECM state from ECM-IDLE to ECM-CONNECTED and to establish radio and S1-U bearers during the transfer of uplink and downlink data. When the UE is in ECM-IDLE mode, it initiates a service request procedure in the ...
... A service request is used to change the ECM state from ECM-IDLE to ECM-CONNECTED and to establish radio and S1-U bearers during the transfer of uplink and downlink data. When the UE is in ECM-IDLE mode, it initiates a service request procedure in the ...
BreezeMAX PRO 5000 CPE
... This user manual is delivered subject to the following conditions and restrictions: This manual contains proprietary information belonging to Alvarion Ltd. Such information is supplied solely for the purpose of assisting properly authorized users of the respective Alvarion products. No part of i ...
... This user manual is delivered subject to the following conditions and restrictions: This manual contains proprietary information belonging to Alvarion Ltd. Such information is supplied solely for the purpose of assisting properly authorized users of the respective Alvarion products. No part of i ...
chapter5
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
McAfee.com Virus Scan Online
... information possible about the trace and the servers and networks on that trace. This requires a great deal of interaction between Visual Trace and various servers on the Web. McAfee.com operates some of these servers, and some of these servers are operated by public or quasi-public entities. Server ...
... information possible about the trace and the servers and networks on that trace. This requires a great deal of interaction between Visual Trace and various servers on the Web. McAfee.com operates some of these servers, and some of these servers are operated by public or quasi-public entities. Server ...
Cisco Application Centric Infrastructure and Cisco Application Virtual
... separate the organizational and forwarding requirements of a tenant. Within each VRF instance, a bridge domain is created. A bridge domain is a Layer 2 namespace in which you define the various subnets. You assign all the subnets and default gateways within the bridge domain. By using separate forwa ...
... separate the organizational and forwarding requirements of a tenant. Within each VRF instance, a bridge domain is created. A bridge domain is a Layer 2 namespace in which you define the various subnets. You assign all the subnets and default gateways within the bridge domain. By using separate forwa ...
Tapestry: A Resilient Global-scale Overlay for Service Deployment
... The first generation of peer-to-peer (P2P) systems included file-sharing and storage applications: Napster, Gnutella, MojoNation, and Freenet. Napster uses central directory servers to locate files. Gnutella provides a similar, but distributed service using scoped broadcast queries, limiting scalabi ...
... The first generation of peer-to-peer (P2P) systems included file-sharing and storage applications: Napster, Gnutella, MojoNation, and Freenet. Napster uses central directory servers to locate files. Gnutella provides a similar, but distributed service using scoped broadcast queries, limiting scalabi ...
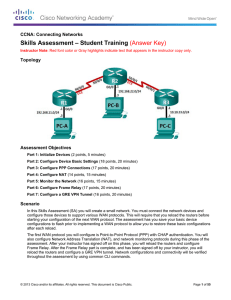
Skills Assessment – Student Training (Answer Key)
... Instructor Note: For the student version of this exam, the instructor should build the network and connect devices prior to the student starting the exam. This will save time and reduce wear on cables and equipment. The student will need to initialize and reload devices. Scoring is adjusted accordin ...
... Instructor Note: For the student version of this exam, the instructor should build the network and connect devices prior to the student starting the exam. This will save time and reduce wear on cables and equipment. The student will need to initialize and reload devices. Scoring is adjusted accordin ...
“The Tenet Architecture for Tiered Sensor Networks.”
... and vice versa. The requirement to support master-to-master communication allows, but does not require, the construction of distributed applications on the masters. Addressability requires much less of motes, however; a mote must be able to communicate with at least one master (assuming the network ...
... and vice versa. The requirement to support master-to-master communication allows, but does not require, the construction of distributed applications on the masters. Addressability requires much less of motes, however; a mote must be able to communicate with at least one master (assuming the network ...
Figure 20 - Zoonsuite
... Status Page Definitions ................................................................................................................ 33 Profiles Page Definitions .............................................................................................................. 36 DECT Page Definition ...
... Status Page Definitions ................................................................................................................ 33 Profiles Page Definitions .............................................................................................................. 36 DECT Page Definition ...
Elektronischer Hšrsaal - univ
... • do not maintain state after SYN at server • encode cipher in sequence number from server to client • Client must reflect it check integrity; if okay, generate state from ACK – Only requires changes at the server – Not specified in RFC - no specification change needed – See http://cr.yp.to/syncoo ...
... • do not maintain state after SYN at server • encode cipher in sequence number from server to client • Client must reflect it check integrity; if okay, generate state from ACK – Only requires changes at the server – Not specified in RFC - no specification change needed – See http://cr.yp.to/syncoo ...
TCP Congestion Control
... • do not maintain state after SYN at server • encode cipher in sequence number from server to client • Client must reflect it check integrity; if okay, generate state from ACK – Only requires changes at the server – Not specified in RFC - no specification change needed – See http://cr.yp.to/syncoo ...
... • do not maintain state after SYN at server • encode cipher in sequence number from server to client • Client must reflect it check integrity; if okay, generate state from ACK – Only requires changes at the server – Not specified in RFC - no specification change needed – See http://cr.yp.to/syncoo ...
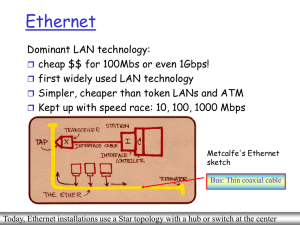
Ethernet Switches
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
Slide 1
... • This is very effective at avoiding collisions, but has time overhead to exchange RTS and CTS messages – Often used for sending large data files – May establish threshold, so only files larger than threshold are allowed to use RTS/CTS INFO 331 chapter 6 ...
... • This is very effective at avoiding collisions, but has time overhead to exchange RTS and CTS messages – Often used for sending large data files – May establish threshold, so only files larger than threshold are allowed to use RTS/CTS INFO 331 chapter 6 ...
Configure Inter-VLAN Routing
... Inter-VLAN routing is the process of routing information between VLANs Inter-VLAN routing requires the use of a router or a layer 3 switch Traditional inter-VLAN routing Requires multiple router interfaces that are each connected to separate VLANs ...
... Inter-VLAN routing is the process of routing information between VLANs Inter-VLAN routing requires the use of a router or a layer 3 switch Traditional inter-VLAN routing Requires multiple router interfaces that are each connected to separate VLANs ...
The Tenet Architecture for Tiered Sensor Networks
... and vice versa. The requirement to support master-to-master communication allows, but does not require, the construction of distributed applications on the masters. Addressability requires much less of motes, however; a mote must be able to communicate with at least one master (assuming the network ...
... and vice versa. The requirement to support master-to-master communication allows, but does not require, the construction of distributed applications on the masters. Addressability requires much less of motes, however; a mote must be able to communicate with at least one master (assuming the network ...
Flooding Attacks by Exploiting Persistent Forwarding Loops jxia, lgao, tfei
... prefixes. Due to security and privacy concerns posed by networks owned by governmental and military agencies, we filter out their prefixes according to WHOIS [4]. After filtering, 5.24 million fine-grained prefixes are traced. To reduce the overhead of our measurement, we perform traceroute to two I ...
... prefixes. Due to security and privacy concerns posed by networks owned by governmental and military agencies, we filter out their prefixes according to WHOIS [4]. After filtering, 5.24 million fine-grained prefixes are traced. To reduce the overhead of our measurement, we perform traceroute to two I ...
Microsoft.Realtests.70-642.v2014-01
... Your company has a single Active Directory domain named oaktree.com. All servers run Windows Server 2008. You have a public DNS server named Server1, and an e-mail server named Server2. Client computers outside the company domain are unable to send e-mail messages to oaktree.com. You verify that the ...
... Your company has a single Active Directory domain named oaktree.com. All servers run Windows Server 2008. You have a public DNS server named Server1, and an e-mail server named Server2. Client computers outside the company domain are unable to send e-mail messages to oaktree.com. You verify that the ...
A Traffic-aware Power Management Protocol for
... hoc and sensor network routing protocols employing a sleep mode in the literature, cluster-based and flat. Both of them achieve energy efficiency by employing different topology management techniques. This section presents a brief review of these two classes of routing to provide a better understand ...
... hoc and sensor network routing protocols employing a sleep mode in the literature, cluster-based and flat. Both of them achieve energy efficiency by employing different topology management techniques. This section presents a brief review of these two classes of routing to provide a better understand ...
Tapestry: A Resilient Global-scale Overlay for Service - IC
... The first generation of peer-to-peer (P2P) systems included file-sharing and storage applications: Napster, Gnutella, Mojo Nation, and Freenet. Napster uses central directory servers to locate files. Gnutella provides a similar, but distributed service using scoped broadcast queries, limiting scalab ...
... The first generation of peer-to-peer (P2P) systems included file-sharing and storage applications: Napster, Gnutella, Mojo Nation, and Freenet. Napster uses central directory servers to locate files. Gnutella provides a similar, but distributed service using scoped broadcast queries, limiting scalab ...
here - Campaign[x]
... reduces energy costs Integrates with borderless services: access control, identity, location Phase 1: Network devices (IP phones, access points, and cameras) ...
... reduces energy costs Integrates with borderless services: access control, identity, location Phase 1: Network devices (IP phones, access points, and cameras) ...
PDF
... The increase in 3G and 4G mobile wireless broadband usage is an indication of even more dramatic growth, which is expected to result from the introduction of High-Speed Packet Access (HSPA), Evolved High-Speed Packet Access (HSPA+), and LTE technologies. To meet the demand and deliver services that ...
... The increase in 3G and 4G mobile wireless broadband usage is an indication of even more dramatic growth, which is expected to result from the introduction of High-Speed Packet Access (HSPA), Evolved High-Speed Packet Access (HSPA+), and LTE technologies. To meet the demand and deliver services that ...
OSPFN - Named Data Networking (NDN)
... same or different prefixes). Moreover, since OSPF provides only a single best path to each destination, we added a configured multipath feature to allow users to specify which links to use when the best route fails to bring back data. Even though OSPFN does not support full-fledged dynamic multipath ...
... same or different prefixes). Moreover, since OSPF provides only a single best path to each destination, we added a configured multipath feature to allow users to specify which links to use when the best route fails to bring back data. Even though OSPFN does not support full-fledged dynamic multipath ...
TKN Performance Evaluation of a QoS-Aware Handover Mechanism S. Sroka and H. Karl
... hardware are easily and cheaply available from the mass market for data communication. However, it is not clear whether this IP-based protocol family will be able to fulfill all the requirements that are currently placed on mobile communication systems. In particular, current GSM-type solutions prov ...
... hardware are easily and cheaply available from the mass market for data communication. However, it is not clear whether this IP-based protocol family will be able to fulfill all the requirements that are currently placed on mobile communication systems. In particular, current GSM-type solutions prov ...
The OAM Jigsaw Puzzle
... responsible for the OAM control plane. It transmits and receives OAM messages that do not require excessive CPU utilization and receives notifications from the FlexOAM mechanism in the packet processor. ...
... responsible for the OAM control plane. It transmits and receives OAM messages that do not require excessive CPU utilization and receives notifications from the FlexOAM mechanism in the packet processor. ...















![here - Campaign[x]](http://s1.studyres.com/store/data/008744944_1-0f4fd57a8eb108cf9826822f0ba0b000-300x300.png)



