momina-RIP
... protocols on internal networks. Helps routers dynamically adapt to changes of network connections by communicating information about which networks each router can reach and how far away those networks are. Its made obsolete by OSPF and IS-IS. Also sometimes called Rest in Pieces. ...
... protocols on internal networks. Helps routers dynamically adapt to changes of network connections by communicating information about which networks each router can reach and how far away those networks are. Its made obsolete by OSPF and IS-IS. Also sometimes called Rest in Pieces. ...
information technology
... PLMN Interfaces, GSM Addresses and Identifiers, Network Aspects in GSM, Mobility Management, GSM Frequency Allocation, Personal Communications Service, Authentication and Security. Short Message Service- Mobile Computing over SMS, Value added services through SMS, Accessing the SMS Bearer. GPRS: GPR ...
... PLMN Interfaces, GSM Addresses and Identifiers, Network Aspects in GSM, Mobility Management, GSM Frequency Allocation, Personal Communications Service, Authentication and Security. Short Message Service- Mobile Computing over SMS, Value added services through SMS, Accessing the SMS Bearer. GPRS: GPR ...
Dell SonicWALL Application Risk Management Report (SWARM)
... First, to give you a general understanding of the threats your network, and your business faces today. Second, to give you an understanding of how a Cisco PIX 515E like yours performed when tested at Dell SonicWALL Laboratories against the same threats that your Cisco firewall faces every day, in or ...
... First, to give you a general understanding of the threats your network, and your business faces today. Second, to give you an understanding of how a Cisco PIX 515E like yours performed when tested at Dell SonicWALL Laboratories against the same threats that your Cisco firewall faces every day, in or ...
Ethane Taking Control of the Enterprise
... Yet the current solutions are weak, making enterprise network management both expensive and error-prone. ◦ 62% of network downtime in multi-vendor networks comes from human-error ◦ 80% of IT budgets is spent on maintenance and operations . ...
... Yet the current solutions are weak, making enterprise network management both expensive and error-prone. ◦ 62% of network downtime in multi-vendor networks comes from human-error ◦ 80% of IT budgets is spent on maintenance and operations . ...
DEPLOYMENT IPV6 OVER IPV4 NETWORK INFRASTRUCTURE Tien Dung Hoang
... writing, each group of 4 octets (16 bits) is represented as unsigned integer which is written in hexadecimal form and separated by colons (:). With 128 bits are used, IPv6 will have 2128 ~ 340,282,366,920,938,463,463,374,607,431,768,211,456 ~ 3.4 * 1038 IPv6 addresses. It is 296 times more than IPv4 ...
... writing, each group of 4 octets (16 bits) is represented as unsigned integer which is written in hexadecimal form and separated by colons (:). With 128 bits are used, IPv6 will have 2128 ~ 340,282,366,920,938,463,463,374,607,431,768,211,456 ~ 3.4 * 1038 IPv6 addresses. It is 296 times more than IPv4 ...
chapter1 - Computer Science Division
... Web, VoIP, email, games, e-commerce, file sharing communication services provided to apps: reliable data delivery from source to destination “best effort” (unreliable) data delivery Introduction ...
... Web, VoIP, email, games, e-commerce, file sharing communication services provided to apps: reliable data delivery from source to destination “best effort” (unreliable) data delivery Introduction ...
Lecture 1
... • Number of hops traversed (store-and-forward delay) • The “competition” for bandwidth the packet encounters (congestion). It may have to sit & wait in router queues. – In practice this boils down to 70 msec ...
... • Number of hops traversed (store-and-forward delay) • The “competition” for bandwidth the packet encounters (congestion). It may have to sit & wait in router queues. – In practice this boils down to 70 msec ...
LoRaWAN - LoRa Alliance
... Bi-directional end-devices (Class A): End-devices of Class A allow for bi-directional communications whereby each end-device’s uplink transmission is followed by two short downlink receive windows. The transmission slot scheduled by the end-device is based on its own communication needs with a small ...
... Bi-directional end-devices (Class A): End-devices of Class A allow for bi-directional communications whereby each end-device’s uplink transmission is followed by two short downlink receive windows. The transmission slot scheduled by the end-device is based on its own communication needs with a small ...
Chapter 1: Foundation - UW Courses Web Server
... Interface exported by the network Since most network protocols are implemented (those in the high protocol stack) in software and nearly all computer systems implement their network protocols as part of the operating system, when we refer to the interface “exported by the network”, we are generally ...
... Interface exported by the network Since most network protocols are implemented (those in the high protocol stack) in software and nearly all computer systems implement their network protocols as part of the operating system, when we refer to the interface “exported by the network”, we are generally ...
Week_Ten_Network_ppt
... 3. PPP carries packets from many different protocol suites using NCP. The NCP sends packets to negotiate the needed settings. Is all data encrypted? No Encryption is used to simply verify the passwords. ...
... 3. PPP carries packets from many different protocol suites using NCP. The NCP sends packets to negotiate the needed settings. Is all data encrypted? No Encryption is used to simply verify the passwords. ...
gdfgdfgfggdf - personal.kent.edu
... Enforce password-based authorization for LAN and WAN access and teach users how to choose difficult-to-decrypt passwords Take the time to develop, publish, and enforce a security policy for users in your organization Maintain restricted access to network equipment rooms and data centers ...
... Enforce password-based authorization for LAN and WAN access and teach users how to choose difficult-to-decrypt passwords Take the time to develop, publish, and enforce a security policy for users in your organization Maintain restricted access to network equipment rooms and data centers ...
1.TNS01%20Review%20of%20Network%20%26%20Communi..
... series of rules and conventions called protocols. The processes on each machine that communicate at a given layer are called peer-to-peer processes. ...
... series of rules and conventions called protocols. The processes on each machine that communicate at a given layer are called peer-to-peer processes. ...
slides - The Fengs
... multiple attacking hosts – Easy to thwart • Vary source of attack by altering frequency of packets • Attack from many sources • Still can’t turn attacker’s off…Must notify upstream ISP to stop ...
... multiple attacking hosts – Easy to thwart • Vary source of attack by altering frequency of packets • Attack from many sources • Still can’t turn attacker’s off…Must notify upstream ISP to stop ...
A study of Network topology using hubs and switches
... (SOHO) applications typically use a single switch, or an all-purpose converged device such as a gateway access to small office/home broadband services such as DSL router or cable Wi-Fi router. In most of these cases, the end-user device contains a router and components that interface to the particul ...
... (SOHO) applications typically use a single switch, or an all-purpose converged device such as a gateway access to small office/home broadband services such as DSL router or cable Wi-Fi router. In most of these cases, the end-user device contains a router and components that interface to the particul ...
paper
... wireless networks with multihome clients provide worldwide internet access by combining various wireless technologies [3]. Mobile devices with multiple wireless interfaces such as cellular and Wi-Fi are widely available in the markets. Therefore, when such a user equipment having access to such mult ...
... wireless networks with multihome clients provide worldwide internet access by combining various wireless technologies [3]. Mobile devices with multiple wireless interfaces such as cellular and Wi-Fi are widely available in the markets. Therefore, when such a user equipment having access to such mult ...
15-overlay
... • Traditional networks route packets looking only at destination • Also, maybe source fields (e.g. multicast) ...
... • Traditional networks route packets looking only at destination • Also, maybe source fields (e.g. multicast) ...
Intro to PHP
... PHP superglobals $_GET and $_POST are used to collect form data When the user fills out the form and clicks the ‘submit’ button, the form data is sent to the PHP file for processing The form data is sent with an HTTP Post or HTTP Get ...
... PHP superglobals $_GET and $_POST are used to collect form data When the user fills out the form and clicks the ‘submit’ button, the form data is sent to the PHP file for processing The form data is sent with an HTTP Post or HTTP Get ...
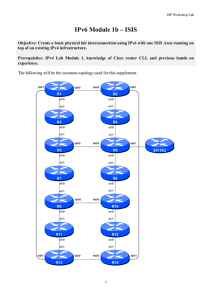
Module 01 - IPv6 ISIS and iBGP
... This workshop will adopt the recommendations of RFC6164 and use a /127 mask for each point-to-point link – even though the link still has a /64 reserved for it. With this revised system, the address plan for IPv6 is greatly simplified. ISPs assign a single /48 for their network infrastructure, and t ...
... This workshop will adopt the recommendations of RFC6164 and use a /127 mask for each point-to-point link – even though the link still has a /64 reserved for it. With this revised system, the address plan for IPv6 is greatly simplified. ISPs assign a single /48 for their network infrastructure, and t ...
FRF.6 - Broadband Forum
... By using this MIB, a customer's network management system (NMS) can monitor its PVCs, UNI ports, and NNI ports. SVCs may be added in the future following the adoption by the Forum of SVC Implementation Agreements. The MIB models an abstract Frame Relay network to the customer. Management of the actu ...
... By using this MIB, a customer's network management system (NMS) can monitor its PVCs, UNI ports, and NNI ports. SVCs may be added in the future following the adoption by the Forum of SVC Implementation Agreements. The MIB models an abstract Frame Relay network to the customer. Management of the actu ...
A+ Guide to Managing and Maintaining Your PC, 7e
... – Enter static IP address, subnet mask, IP addresses of the default gateway, DNS servers if necessary – Configure the DHCP server – Provide static addresses for local PCs if necessary ...
... – Enter static IP address, subnet mask, IP addresses of the default gateway, DNS servers if necessary – Configure the DHCP server – Provide static addresses for local PCs if necessary ...
A Survey on Denial of Service Attacks
... compromise a website, causing the resources normally issued by the website those no longer for clients of that website. Distributed Denial of Service (DDOS) attacks are based on traffic volume based attacks from huge number of compromised hosts. These hosts or resources, known as ‘zombies’, form a w ...
... compromise a website, causing the resources normally issued by the website those no longer for clients of that website. Distributed Denial of Service (DDOS) attacks are based on traffic volume based attacks from huge number of compromised hosts. These hosts or resources, known as ‘zombies’, form a w ...
Ad hoc wireless multicast routing
... If two communications nodes are within radio range of each other these connections can be direct ...
... If two communications nodes are within radio range of each other these connections can be direct ...
Document
... routing tables on each router • To accomplish the summarization, you need to determine how many bits to unmask or unsubnet in order to make the networks appear as one big address block • The routing protocol must transmit the network prefix along with the network address during route advertisements ...
... routing tables on each router • To accomplish the summarization, you need to determine how many bits to unmask or unsubnet in order to make the networks appear as one big address block • The routing protocol must transmit the network prefix along with the network address during route advertisements ...