Network
... have: More advanced micro-processors; More memory. It allows many users to share services Clients: computer that request services. Can be workstations, PCs, or Software applications. Usually one user per client. Peer: May request and provide services. Usually use Peer-to-peer networks. Has Equiv ...
... have: More advanced micro-processors; More memory. It allows many users to share services Clients: computer that request services. Can be workstations, PCs, or Software applications. Usually one user per client. Peer: May request and provide services. Usually use Peer-to-peer networks. Has Equiv ...
Network+ Guide to Networks 6th Edition
... Network Design (cont’d.) • CARP (Common Address Redundancy Protocol) – Allows pool of computers to share IP addresses – Master computer receives request • Parcels out request to one of several group computers ...
... Network Design (cont’d.) • CARP (Common Address Redundancy Protocol) – Allows pool of computers to share IP addresses – Master computer receives request • Parcels out request to one of several group computers ...
ZIGZAG: An Efficient Peer-to-Peer Scheme for Media Streaming
... Each node X in a layer-j cluster periodically communicates with its layer-j cl ustermates, its children and parent on the multicast tree For peers within a cluster, the exchanged information is the peer degree If the recipient is the cluster head, X also sends a list L = {[X1,d1],[X2,d 2],..}, where ...
... Each node X in a layer-j cluster periodically communicates with its layer-j cl ustermates, its children and parent on the multicast tree For peers within a cluster, the exchanged information is the peer degree If the recipient is the cluster head, X also sends a list L = {[X1,d1],[X2,d 2],..}, where ...
LAN Systems
... – Aggregate throughputs and real-time support for multimedia applications. Network Technology CSE3020 - 2006 ...
... – Aggregate throughputs and real-time support for multimedia applications. Network Technology CSE3020 - 2006 ...
slides
... IP addressing: introduction Q: how are interfaces actually connected? A: we’ll learn about that in chapter 5, 6. ...
... IP addressing: introduction Q: how are interfaces actually connected? A: we’ll learn about that in chapter 5, 6. ...
ppt
... Simple case: socket name is the same as physical address. No mapping, we just need to break our message into frames…maybe Physical Layer – typically low bandwidth, serial, byte oriented Data link layer – read/write interface to the application frames: destination address, data, checksum. N ...
... Simple case: socket name is the same as physical address. No mapping, we just need to break our message into frames…maybe Physical Layer – typically low bandwidth, serial, byte oriented Data link layer – read/write interface to the application frames: destination address, data, checksum. N ...
Chapter 1. Introduction to Data Communications
... Approaches of Using ATM in Backbone • LAN Emulation (LANE) – Breaking LAN frame into 48-byte long blocks and transmit them in an ATM cell – Called encapsulation and done by edge switches – Reassembling done at the destination edge switch and LAN frame is sent to the LAN – Requires translating of MA ...
... Approaches of Using ATM in Backbone • LAN Emulation (LANE) – Breaking LAN frame into 48-byte long blocks and transmit them in an ATM cell – Called encapsulation and done by edge switches – Reassembling done at the destination edge switch and LAN frame is sent to the LAN – Requires translating of MA ...
Discovering Computers Fundamentals, 2012 Edition Your Interactive Guide
... An intranet is an internal network that uses Internet technologies ...
... An intranet is an internal network that uses Internet technologies ...
Slide 1
... – Supports various types of authentication besides a shared secret, such as username/password – Dynamically changes keys as session continues – Cryptographic method to check integrity – Frame counter to prevent replay attacks ...
... – Supports various types of authentication besides a shared secret, such as username/password – Dynamically changes keys as session continues – Cryptographic method to check integrity – Frame counter to prevent replay attacks ...
Internet Operation
... Inter-‐router link does not require global address inside AS ± OSPFv3 uses link-‐local address to exchange LSAs ± only loopback interface needs to configure global address ...
... Inter-‐router link does not require global address inside AS ± OSPFv3 uses link-‐local address to exchange LSAs ± only loopback interface needs to configure global address ...
CCNA3 Chap 2 Study Answers
... How is shared memory buffering better than port-based memory buffering? Port-based memory buffering has a separate buffer of fixed capacity for each incoming port. Shared memory buffering puts all incoming frames into the same buffer so that the memory can be allocated dynamically as required. This ...
... How is shared memory buffering better than port-based memory buffering? Port-based memory buffering has a separate buffer of fixed capacity for each incoming port. Shared memory buffering puts all incoming frames into the same buffer so that the memory can be allocated dynamically as required. This ...
Networking Chapter 18
... – Enter static IP address, subnet mask, IP addresses of the default gateway, DNS servers if necessary – Configure the DHCP server – Provide static addresses for local PCs if necessary ...
... – Enter static IP address, subnet mask, IP addresses of the default gateway, DNS servers if necessary – Configure the DHCP server – Provide static addresses for local PCs if necessary ...
Securing Data using Pre-filtering and Traceback Method
... Regular expressions (RegEx) have been widely used in a variety of network and security applications. A Prefiltering Approach to Regular Expression Matching monitoring of network traffic based on application protocols. The RegEx matching problem can be defined as follows: given a set R of RegExes, at ...
... Regular expressions (RegEx) have been widely used in a variety of network and security applications. A Prefiltering Approach to Regular Expression Matching monitoring of network traffic based on application protocols. The RegEx matching problem can be defined as follows: given a set R of RegExes, at ...
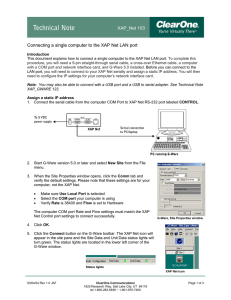
Connecting a Single Computer to the XAP Net LAN Port
... Connecting a single computer to the XAP Net LAN port Introduction This document explains how to connect a single computer to the XAP Net LAN port. To complete this procedure, you will need a 9-pin straight-through serial cable, a cross-over Ethernet cable, a computer with a COM port and network inte ...
... Connecting a single computer to the XAP Net LAN port Introduction This document explains how to connect a single computer to the XAP Net LAN port. To complete this procedure, you will need a 9-pin straight-through serial cable, a cross-over Ethernet cable, a computer with a COM port and network inte ...
Figure 7.8(a) - Fordham University Computer and Information
... – Offers voice services as well as data communication at rates of 0.5 to 2.4 Mbps – Now 4G (up to 10 times faster than 3G) Invitation to Computer Science, 5th Edition ...
... – Offers voice services as well as data communication at rates of 0.5 to 2.4 Mbps – Now 4G (up to 10 times faster than 3G) Invitation to Computer Science, 5th Edition ...
Adventures in Computer Security - Applied Crypto Group at Stanford
... Attacker sends RST packet to reset connection • Need to guess seq. # for an existing connection – Naively, success prob. is 1/232 for 32-bit seq. number – Most systems allow for a large window of acceptable seq. #’s much higher success probability ...
... Attacker sends RST packet to reset connection • Need to guess seq. # for an existing connection – Naively, success prob. is 1/232 for 32-bit seq. number – Most systems allow for a large window of acceptable seq. #’s much higher success probability ...
Sixth International Conference on Formal Engineering Methods
... Machine learning for the people - what does it mean for you? AI Engage - humans and machines solving important problems for humanity Want to Fuel the Future? Join us. Join a first-rate researcher network at the forefront of creative solutions to critical technological challenges. Working in research ...
... Machine learning for the people - what does it mean for you? AI Engage - humans and machines solving important problems for humanity Want to Fuel the Future? Join us. Join a first-rate researcher network at the forefront of creative solutions to critical technological challenges. Working in research ...
File: IIB ACCEPTABLE USE POLICY for Internet/Online
... For the purposes of this policy, the term “network” is defined to be any computers linked together by wire, wireless, fiber, or other connection, including district computers, dial-in access to district computers, or computers of the HCCA. Computers and computer networks shall be used solely for aca ...
... For the purposes of this policy, the term “network” is defined to be any computers linked together by wire, wireless, fiber, or other connection, including district computers, dial-in access to district computers, or computers of the HCCA. Computers and computer networks shall be used solely for aca ...
1 - Amazon Web Services
... 1: Wizards & UTO Tool commercial equivalent e.g., CISCO IPCS, Juniper CESAC used to (re) configure network management parameters using state meta data harvested by heartbeat beacon mechanism that is Telco PSAP standard from computer devices on TCP/IP networks described by heartbeat message counterpa ...
... 1: Wizards & UTO Tool commercial equivalent e.g., CISCO IPCS, Juniper CESAC used to (re) configure network management parameters using state meta data harvested by heartbeat beacon mechanism that is Telco PSAP standard from computer devices on TCP/IP networks described by heartbeat message counterpa ...
(1.8 MB)
... • When the LAN control is enabled, serial RS-232C commands may not be transmitted. • You can’t control the LAN/serial RS-232C commands for about 10 seconds after turning on the main power of the projector. • When commands for LAN control and for RS-232C control are issued at the same time, the LA ...
... • When the LAN control is enabled, serial RS-232C commands may not be transmitted. • You can’t control the LAN/serial RS-232C commands for about 10 seconds after turning on the main power of the projector. • When commands for LAN control and for RS-232C control are issued at the same time, the LA ...
PAGE 818. The following new Section is added after Section... 684 NETWORK DEVICES.
... connections. 3. Verify proper voltages for all power supplies and related power circuits. 4. Connect devices to the power sources. 5. Verify all connections, including correct installation of communication and power cables. 6. Verify the network connection to the device server through ping and telne ...
... connections. 3. Verify proper voltages for all power supplies and related power circuits. 4. Connect devices to the power sources. 5. Verify all connections, including correct installation of communication and power cables. 6. Verify the network connection to the device server through ping and telne ...