$doc.title
... the set of disHnct related desHnaHon or source ports TCP flag: the set of disHnct flag combinaHons used ...
... the set of disHnct related desHnaHon or source ports TCP flag: the set of disHnct flag combinaHons used ...
Presentation
... Note: The value of the PT field is 000 in all cells carrying an IP datagram fragment except for the last cell; the value is 001 in the last cell. ...
... Note: The value of the PT field is 000 in all cells carrying an IP datagram fragment except for the last cell; the value is 001 in the last cell. ...
ALPINE 3800 SERIES
... scalability, flexibility, security and management features required to build complete enterprisewide networks, including large campuses, branch offices, data centers and wiring closets. The Alpine 3800 series switches enable enterprise networks to adopt new technologies, such as wireless and Voice-o ...
... scalability, flexibility, security and management features required to build complete enterprisewide networks, including large campuses, branch offices, data centers and wiring closets. The Alpine 3800 series switches enable enterprise networks to adopt new technologies, such as wireless and Voice-o ...
1b.chapter1
... distributed applications: Web, VoIP, email, games, e-commerce, file sharing communication services provided to apps: reliable data delivery from source to destination “best effort” (unreliable) data delivery ...
... distributed applications: Web, VoIP, email, games, e-commerce, file sharing communication services provided to apps: reliable data delivery from source to destination “best effort” (unreliable) data delivery ...
Networking
... • Internet Protocol (IP) o Provides a distinct identification to any computer connected to the Internet: the IP address or Internet address ...
... • Internet Protocol (IP) o Provides a distinct identification to any computer connected to the Internet: the IP address or Internet address ...
Hyperbolic Routing in NDN World
... the Interest came. Otherwise the router looks up the name in its PIT, and if a matching entry exists, it simply records the incoming interface of this Interest in the PIT entry. In the absence of a matching PIT entry, the router will forward the Interest toward the data producer(s) based on informat ...
... the Interest came. Otherwise the router looks up the name in its PIT, and if a matching entry exists, it simply records the incoming interface of this Interest in the PIT entry. In the absence of a matching PIT entry, the router will forward the Interest toward the data producer(s) based on informat ...
3rd Edition, Chapter 5
... Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at hub: adapters detect collisions provides net management functionality ...
... Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at hub: adapters detect collisions provides net management functionality ...
Is an Alligator Better Than an Armadillo? Is an
... interconnection network were “best” for all applications and all operating environments (including hardware, software, and financial factors). Unfortunately, no such network exists. Furthermore, even for a fixed application domain and a fixed operating environment, selecting the best network may be ...
... interconnection network were “best” for all applications and all operating environments (including hardware, software, and financial factors). Unfortunately, no such network exists. Furthermore, even for a fixed application domain and a fixed operating environment, selecting the best network may be ...
ECE537-Class 9_2009 - Electrical & Computer Engineering
... • Can adjust to changes in delay and throughput • E.g. common TCP and UDP application – E-Mail – insensitive to delay changes – FTP – User expect delay proportional to file size • Sensitive to changes in throughput ...
... • Can adjust to changes in delay and throughput • E.g. common TCP and UDP application – E-Mail – insensitive to delay changes – FTP – User expect delay proportional to file size • Sensitive to changes in throughput ...
Computers Are Your Future Twelfth Edition
... • Internet Protocol (IP) o Provides a distinct identification to any computer connected to the Internet: the IP address or Internet address ...
... • Internet Protocol (IP) o Provides a distinct identification to any computer connected to the Internet: the IP address or Internet address ...
No Slide Title
... Enhanced Interior Gateway Routing Protocol (EIGRP), and Open Shortest Path First (OSPF). Routed protocols. These protocols are any network layer protocol that allows for the addressing of a host and a destination on a network, such as IP and IPX. Routers are responsible for passing a data packet ont ...
... Enhanced Interior Gateway Routing Protocol (EIGRP), and Open Shortest Path First (OSPF). Routed protocols. These protocols are any network layer protocol that allows for the addressing of a host and a destination on a network, such as IP and IPX. Routers are responsible for passing a data packet ont ...
... D-Link wireless products are based on industry standards to provide high-speed wireless connectivity that is easy to use within your home, business or public access wireless networks. D-Link wireless products provides you with access to the data you want, whenever and wherever you want it. Enjoy the ...
Joint Announcement
... Virtela Technology Services Incorporated is the smart alternative to traditional global carriers and equipment vendors for enterprise networking and virtualized IT services. The company delivers award-winning services via its Virtualized Overlay Network and Virtela Enterprise Services Cloud (ESC) pl ...
... Virtela Technology Services Incorporated is the smart alternative to traditional global carriers and equipment vendors for enterprise networking and virtualized IT services. The company delivers award-winning services via its Virtualized Overlay Network and Virtela Enterprise Services Cloud (ESC) pl ...
DocuCentre S2420 / S2220
... postage stamps and post cards. Certificate stamps stipulated by law. The reproduction of works for copyright purposes (literary works, musical works, paintings, engravings, maps, cinematographic works, photographic works, etc.) is prohibited except when they are reproduced personally, at home or wit ...
... postage stamps and post cards. Certificate stamps stipulated by law. The reproduction of works for copyright purposes (literary works, musical works, paintings, engravings, maps, cinematographic works, photographic works, etc.) is prohibited except when they are reproduced personally, at home or wit ...
Virtual Services Platform 4000
... implementation of the Shortest Path Bridging (SPB) standards of IEEE 802.1aq and IETF RFC 6329, augmented with Avaya enhancements that deliver Enterprise-specific optimization. It offers the ability to create a simplified network that can dynamically virtualize elements to empower efficient provisio ...
... implementation of the Shortest Path Bridging (SPB) standards of IEEE 802.1aq and IETF RFC 6329, augmented with Avaya enhancements that deliver Enterprise-specific optimization. It offers the ability to create a simplified network that can dynamically virtualize elements to empower efficient provisio ...
kuroseSlides-chapter1
... 1.5 Internet structure and ISPs 1.6 Delay & loss in packet-switched networks 1.7 Protocol layers, service models 1.8 History Introduction ...
... 1.5 Internet structure and ISPs 1.6 Delay & loss in packet-switched networks 1.7 Protocol layers, service models 1.8 History Introduction ...
NAT - Chair of Network Architectures and Services
... implemented on the NAT device and operates on layer 7 supports Layer 7 protocols that carry realm specific addresses in their payload • SIP, FTP ...
... implemented on the NAT device and operates on layer 7 supports Layer 7 protocols that carry realm specific addresses in their payload • SIP, FTP ...
PowerPoint Presentation - Securing a Wireless 802.11b Network
... a wireless card and some software A directional antenna will increase the range over which the attacker can access your network Directional antenna can be made from a Pringles potato chip can! Attackers drive around with their computers looking for open wireless networks ...
... a wireless card and some software A directional antenna will increase the range over which the attacker can access your network Directional antenna can be made from a Pringles potato chip can! Attackers drive around with their computers looking for open wireless networks ...
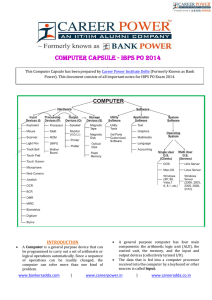
COMPUTER CAPSULE - IBPS PO 2014 . INTRODUCTION
... data from the user (input), processes the data by performing calculations and operations on it and generates the desired Output. The device which is used with a computer to display or store data is called Peripherals. The mechanical, magnetic, electronic and electrical components that comprises a co ...
... data from the user (input), processes the data by performing calculations and operations on it and generates the desired Output. The device which is used with a computer to display or store data is called Peripherals. The mechanical, magnetic, electronic and electrical components that comprises a co ...
Integration von Wägedaten in Prozesse
... lyzers, and cable performance analyzers are employed when troubleshooting network media problems. For PLC based applications, some vendors supply PC based simulation software for viewing and verifying data communicated from a weighing terminal’s PLC port. LEDs mounted to the communication PCB provid ...
... lyzers, and cable performance analyzers are employed when troubleshooting network media problems. For PLC based applications, some vendors supply PC based simulation software for viewing and verifying data communicated from a weighing terminal’s PLC port. LEDs mounted to the communication PCB provid ...
ppt - Carnegie Mellon School of Computer Science
... Each protocol layer needs to provide some hooks to upper layer protocols » Demultiplexing: identify which upper layer protocol packet belongs to » E.g., port numbers allow TCP/UDP to identify target application » Ethernet uses Type field ...
... Each protocol layer needs to provide some hooks to upper layer protocols » Demultiplexing: identify which upper layer protocol packet belongs to » E.g., port numbers allow TCP/UDP to identify target application » Ethernet uses Type field ...
Introduction to Computer Networks
... There was a big debate, of course, but telephone networks are less efficient for routing bursty data (Internet data). ...
... There was a big debate, of course, but telephone networks are less efficient for routing bursty data (Internet data). ...
IaaS * Network Virtualization
... from an access layer into a layer of distribution switches and finally onto the network core. A hierarchical approach to network design has proven to deliver the best results in terms of ...
... from an access layer into a layer of distribution switches and finally onto the network core. A hierarchical approach to network design has proven to deliver the best results in terms of ...
Deschenes
... useful to researchers, especially with respect to the execution of realistic simulations ...
... useful to researchers, especially with respect to the execution of realistic simulations ...
HTTP Protocol - School of Engineering and Advanced Technology
... side of the firewall. Typically, the server is connected to a network protected by a firewall, with the client external to the network. In this case, the client must authenticate itself to the proxy, which can then pass the request on to the server. Non-HTTP server: useful when Web browsers need to ...
... side of the firewall. Typically, the server is connected to a network protected by a firewall, with the client external to the network. In this case, the client must authenticate itself to the proxy, which can then pass the request on to the server. Non-HTTP server: useful when Web browsers need to ...