quality of service - Victor Tikhonov website
... that reflects or predicts the subjectively experienced quality. In this context, QoS is the acceptable cumulative effect on subscriber satisfaction of all imperfections affecting the service. Other terms with similar meaning are the quality of experience (QoE) subjective business concept, the requir ...
... that reflects or predicts the subjectively experienced quality. In this context, QoS is the acceptable cumulative effect on subscriber satisfaction of all imperfections affecting the service. Other terms with similar meaning are the quality of experience (QoE) subjective business concept, the requir ...
FAQ Sprint 3G/4G USB Modem U300
... • If a message that you must restart your computer is displayed, click Yes to restart you computer. Wait until your computer restarts to launch Sprint SmartView. Q: Where can I get the latest version of the Sprint SmartView software for my U300 USB modem? A: Users can initiate an update to the lates ...
... • If a message that you must restart your computer is displayed, click Yes to restart you computer. Wait until your computer restarts to launch Sprint SmartView. Q: Where can I get the latest version of the Sprint SmartView software for my U300 USB modem? A: Users can initiate an update to the lates ...
Internet2 DCS
... the exchange of messages to instantiate specific provisioning requests based upon the above routing and path computation functions. This is typically a RVSP-TE exchange for the GMPLS control planes. Web services based exchanges might employ a modified version of this technique or something entirel ...
... the exchange of messages to instantiate specific provisioning requests based upon the above routing and path computation functions. This is typically a RVSP-TE exchange for the GMPLS control planes. Web services based exchanges might employ a modified version of this technique or something entirel ...
Smarter Traffic Management Version 1.0 14 March 2017
... Security Classification: Non-confidential Access to and distribution of this document is restricted to the persons permitted by the security classification. This document is confidential to the Association and is subject to copyright protection. This document is to be used only for the purposes for ...
... Security Classification: Non-confidential Access to and distribution of this document is restricted to the persons permitted by the security classification. This document is confidential to the Association and is subject to copyright protection. This document is to be used only for the purposes for ...
Data Communication and Networking
... computers and other devices that use a common network language to share resources send data to and receive data from each other over a network media. The computers are said to be interconnected if they are able to exchange information. Each computer in the network is regarded as nodes. A node can al ...
... computers and other devices that use a common network language to share resources send data to and receive data from each other over a network media. The computers are said to be interconnected if they are able to exchange information. Each computer in the network is regarded as nodes. A node can al ...
Applications and Layered Architecture
... Unified view of layers, protocols, and services • Various layers: a layer groups a set of relevant functions • Peer processes (entities): the two corresponding communicating processes (entities) in a layer • Protocol: rules governing the behavior of two peer entities in that layer • Services: the f ...
... Unified view of layers, protocols, and services • Various layers: a layer groups a set of relevant functions • Peer processes (entities): the two corresponding communicating processes (entities) in a layer • Protocol: rules governing the behavior of two peer entities in that layer • Services: the f ...
Fastpass
... 1. Timeslot allocation algorithm: at the arbiter to determine when each endpoint’s packets should be sent. 2. Path assignment algorithm: at the arbiter to assign a path to each packet. 3. Fastpass Control Protocol (FCP) : A replication strategy for the central arbiter to handle network and arbiter f ...
... 1. Timeslot allocation algorithm: at the arbiter to determine when each endpoint’s packets should be sent. 2. Path assignment algorithm: at the arbiter to assign a path to each packet. 3. Fastpass Control Protocol (FCP) : A replication strategy for the central arbiter to handle network and arbiter f ...
DOS ATTACK - DSpace at CUSAT
... echo request packets and the direction of packets to IP broadcast addresses. The Internet Control Message Protocol (ICMP) is used to handle errors and exchange control messages. ICMP can be used to determine if a machine on the Internet is responding. To do this, an ICMP echo request packet is sent ...
... echo request packets and the direction of packets to IP broadcast addresses. The Internet Control Message Protocol (ICMP) is used to handle errors and exchange control messages. ICMP can be used to determine if a machine on the Internet is responding. To do this, an ICMP echo request packet is sent ...
Arctic networking properties
... • The monitor should be used to verify the "end-to-end" operation of GPRS or Tunnel connection. This is achieved by periodically pinging the defined IP address. – In Tunnel mode pinging the private Tunnel IP of M2M GW – In plaing GPRS mode pinging suitable public IP address. ...
... • The monitor should be used to verify the "end-to-end" operation of GPRS or Tunnel connection. This is achieved by periodically pinging the defined IP address. – In Tunnel mode pinging the private Tunnel IP of M2M GW – In plaing GPRS mode pinging suitable public IP address. ...
ISM 3410 Telecomm and Networking in Business
... – selects the route (if more than one is availble) the transmission will take between two devices – converts user addressing that is meaningful to network software and hardware – controls the flow of messages so that it will not over/under run of the speed of other devices – prevents the loss or dup ...
... – selects the route (if more than one is availble) the transmission will take between two devices – converts user addressing that is meaningful to network software and hardware – controls the flow of messages so that it will not over/under run of the speed of other devices – prevents the loss or dup ...
Secure Socket Layer (SSL) 1: Basic Overview
... Secure Socket Layer (SSL) is an effective method of protecting data which is sent over a local or wide area network and is now available on Brothers range of colour laser network machines. It works by encrypting data sent over a network, i.e. a print job, so anyone trying to capture it will not be a ...
... Secure Socket Layer (SSL) is an effective method of protecting data which is sent over a local or wide area network and is now available on Brothers range of colour laser network machines. It works by encrypting data sent over a network, i.e. a print job, so anyone trying to capture it will not be a ...
G805 Introduction
... – CS: TDM, PDH, SDH, OTN – CO: ATM, FR, MPLS, TCP/IP, SCTP/IP – CL: UDP/IP, IPX, Ethernet, CLNP ...
... – CS: TDM, PDH, SDH, OTN – CO: ATM, FR, MPLS, TCP/IP, SCTP/IP – CL: UDP/IP, IPX, Ethernet, CLNP ...
Hidden cost of Chromebook deployments: Up to 40 times longer to
... When purchasing computers for use in schools or businesses, cost is usually an important factor. Systems that require users to access the Internet to carry out everyday tasks can be problematic for a variety of reasons, not least of all the large amount of network traffic created by numerous machine ...
... When purchasing computers for use in schools or businesses, cost is usually an important factor. Systems that require users to access the Internet to carry out everyday tasks can be problematic for a variety of reasons, not least of all the large amount of network traffic created by numerous machine ...
ICMP - Febby Dian Anggraini
... problem; it merely reports the problem • ICMP reports on the status of the delivered packet only to the source device • It does not propagate information about network changes to routers ...
... problem; it merely reports the problem • ICMP reports on the status of the delivered packet only to the source device • It does not propagate information about network changes to routers ...
Dominating-Set-Based Routing in Ad Hoc Wireless Networks
... An ad hoc network is a collection of wireless mobile host forming a temporary network without the aid of any centralized administration or standard support services regularly available on the wide area network to which the hosts may normally be connected (Johnson and Maltz) ...
... An ad hoc network is a collection of wireless mobile host forming a temporary network without the aid of any centralized administration or standard support services regularly available on the wide area network to which the hosts may normally be connected (Johnson and Maltz) ...
3rd Edition: Chapter 1
... systems to edge router? residential access nets institutional access networks (school, ...
... systems to edge router? residential access nets institutional access networks (school, ...
PDF
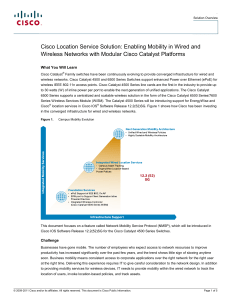
... The Cisco location service solution (also referred to as context-aware service) provides the capability to determine the physical location of a tracked entity in the network as well as additional contextual information such as the serial number of the tracked entity. The tracked entity can be a wire ...
... The Cisco location service solution (also referred to as context-aware service) provides the capability to determine the physical location of a tracked entity in the network as well as additional contextual information such as the serial number of the tracked entity. The tracked entity can be a wire ...
for overlay networks
... protocols that scale to very large groups generally ignore the layer-3 network ...
... protocols that scale to very large groups generally ignore the layer-3 network ...
Folie 1 - Open Universiteit
... Can easily install and run on students own computer (Virtual) Hardware setup for the example exercise I Start the environment ...
... Can easily install and run on students own computer (Virtual) Hardware setup for the example exercise I Start the environment ...
Document
... 5. Pass the reassembled data to the application in a usable form. Both sending and receiving computers need to perform each step in the same way so that the data will have the same structure when it is received as it did when it was sent. For example, two different protocols might each break data in ...
... 5. Pass the reassembled data to the application in a usable form. Both sending and receiving computers need to perform each step in the same way so that the data will have the same structure when it is received as it did when it was sent. For example, two different protocols might each break data in ...