Chapter 15 Local Area Network Overview
... • Set of devices and LANs connected by layer 2 switches have flat address space — Allusers share common MAC broadcast address — If any device issues broadcast frame, that frame is delivered to all devices attached to network connected by layer 2 switches and/or bridges — In large network, broadcast ...
... • Set of devices and LANs connected by layer 2 switches have flat address space — Allusers share common MAC broadcast address — If any device issues broadcast frame, that frame is delivered to all devices attached to network connected by layer 2 switches and/or bridges — In large network, broadcast ...
Module 1: Overview of Microsoft ISA Server
... improve the speed at which users on your internal network can access Internet resources. You can also deploy ISA Server as a reverse caching server to improve the speed at which external users can access selected Web resources that you make available to the Internet. In addition, you can distribute ...
... improve the speed at which users on your internal network can access Internet resources. You can also deploy ISA Server as a reverse caching server to improve the speed at which external users can access selected Web resources that you make available to the Internet. In addition, you can distribute ...
www.cs.kau.se
... • Has no support for multi-homing – Difficult to build link or path-level redundancy ...
... • Has no support for multi-homing – Difficult to build link or path-level redundancy ...
Classification and Evaluation of Multicast-Based Mobility Support in All-IP Cellular Networks
... protocols which are optimized for small groups and for economical usage of the scarce wireless resources. Alternatively, the access point might be selected as the multicast endpoint and act as a multicast proxy. This option facilitates the usage of optimized signaling protocols on the wireless link. ...
... protocols which are optimized for small groups and for economical usage of the scarce wireless resources. Alternatively, the access point might be selected as the multicast endpoint and act as a multicast proxy. This option facilitates the usage of optimized signaling protocols on the wireless link. ...
E-Class Network Security Appliance Series
... protect the network automatically and seamlessly, while inspecting hundreds of thousands of connections simultaneously across all ports, with near zero latency and unlimited stream size. Flexible deployment as either a traditional gateway or as an inline solution allows administrators to keep their ...
... protect the network automatically and seamlessly, while inspecting hundreds of thousands of connections simultaneously across all ports, with near zero latency and unlimited stream size. Flexible deployment as either a traditional gateway or as an inline solution allows administrators to keep their ...
Memory Requirements
... the affected area receive the LSP and run the SPF algorithm. This can help isolate an unstable link to a specific area in the routing domain. In the figure, there are three separate routing domains: Area 1, Area 0, and Area 51. – If a network in Area 51 goes down, the LSP with the information about ...
... the affected area receive the LSP and run the SPF algorithm. This can help isolate an unstable link to a specific area in the routing domain. In the figure, there are three separate routing domains: Area 1, Area 0, and Area 51. – If a network in Area 51 goes down, the LSP with the information about ...
downloading
... c. Remove one of the links in the bundle. What happens? 8. Suppose you wanted to load balance the traffic from the two VLANs across both aggregation switches. How can you achieve this? (Only done if MSTP is supported). a. Configure MSTP using Appendix G. b. Verify status of each spanning tree instan ...
... c. Remove one of the links in the bundle. What happens? 8. Suppose you wanted to load balance the traffic from the two VLANs across both aggregation switches. How can you achieve this? (Only done if MSTP is supported). a. Configure MSTP using Appendix G. b. Verify status of each spanning tree instan ...
M.Tech - Telecommunication Networks
... To understand how TCP/IP Protocol suite is designed and implemented INSTRUCTIONAL OBJECTIVES * To learn about internetworking, in-detailed * To learn about TCP/IP Architecture & Protocols ...
... To understand how TCP/IP Protocol suite is designed and implemented INSTRUCTIONAL OBJECTIVES * To learn about internetworking, in-detailed * To learn about TCP/IP Architecture & Protocols ...
Network VI
... Default Route: the IPv4 default route as 0.0.0.0. The default route is used as a "catch all" route when a more specific route is not available. The use of this address also reserves all addresses in the 0.0.0.0 0.255.255.255 (0.0.0.0 /8) address block. Loopback: One such reserved address is the ...
... Default Route: the IPv4 default route as 0.0.0.0. The default route is used as a "catch all" route when a more specific route is not available. The use of this address also reserves all addresses in the 0.0.0.0 0.255.255.255 (0.0.0.0 /8) address block. Loopback: One such reserved address is the ...
Designing Protection System of LAN Security Bachelor’s Thesis (UAS)
... Designing Protection System of LAN Security ABSTRACT Local Area Network (LAN) refers to the local area coverage of a computer network. In general, communication data packets which can be transmitted between any two network nodes based on broadcast transmission have been widely used in local area net ...
... Designing Protection System of LAN Security ABSTRACT Local Area Network (LAN) refers to the local area coverage of a computer network. In general, communication data packets which can be transmitted between any two network nodes based on broadcast transmission have been widely used in local area net ...
Overview of the ORBIT Radio Grid Testbed for Evaluation of Next
... Software packages and libraries have been developed to support both application/protocol evaluations. These include common libraries for traffic generation, measurement collection etc. and also provide easy hooks to enable "expert" users to develop their own applications, protocol stacks, MAC layer ...
... Software packages and libraries have been developed to support both application/protocol evaluations. These include common libraries for traffic generation, measurement collection etc. and also provide easy hooks to enable "expert" users to develop their own applications, protocol stacks, MAC layer ...
notes
... • Application Layer – contains higher-level protocols – DNS – Domain Name Service • Maps host names onto their network addresses ...
... • Application Layer – contains higher-level protocols – DNS – Domain Name Service • Maps host names onto their network addresses ...
Sample Test 4 with solutions
... ____ 49. The technique of breaking a message into individual packets, sending the packets along the best route available, and then reassembling the data is called ____. a. packet catching c. packet switching b. packet building d. packet swapping ____ 50. One popular use of the ____ network standard ...
... ____ 49. The technique of breaking a message into individual packets, sending the packets along the best route available, and then reassembling the data is called ____. a. packet catching c. packet switching b. packet building d. packet swapping ____ 50. One popular use of the ____ network standard ...
Week_Eleven_ppt
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
Systems Analysis and Design
... We own and operate NCREN (NC Research and Education Network) One of the most advanced statewide research and education networks in the country Provide Internet, video and related services to University of North Carolina’s 16 campus system, Duke, Wake Forest, etc. ...
... We own and operate NCREN (NC Research and Education Network) One of the most advanced statewide research and education networks in the country Provide Internet, video and related services to University of North Carolina’s 16 campus system, Duke, Wake Forest, etc. ...
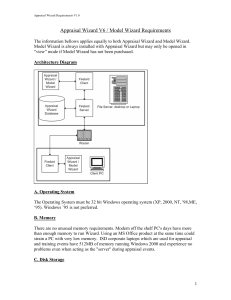
Appraisal Wizard Requirements
... The TCP / IP protocol should be installed. It is rare to find a PC that does not have this since it is used for internet / intranet access. When multiple laptops are being networked together so that Appraisal Wizard users can operate together in the same database, the TCP/IP protocol is used to comm ...
... The TCP / IP protocol should be installed. It is rare to find a PC that does not have this since it is used for internet / intranet access. When multiple laptops are being networked together so that Appraisal Wizard users can operate together in the same database, the TCP/IP protocol is used to comm ...
HP 3500 and 3500 yl Switch Series
... Monitors 10 types of network traffic; and sends a warning when an anomaly that can be potentially caused by malicious attacks is detected • Port security Allows access only to specified MAC addresses, which can be learned or specified by the administrator • MAC address lockout Helps prevent certain ...
... Monitors 10 types of network traffic; and sends a warning when an anomaly that can be potentially caused by malicious attacks is detected • Port security Allows access only to specified MAC addresses, which can be learned or specified by the administrator • MAC address lockout Helps prevent certain ...
Link Layer - dbmanagement.info
... 802.3 Ethernet Standards: Link & Physical Layers many different Ethernet standards common MAC protocol and frame format ...
... 802.3 Ethernet Standards: Link & Physical Layers many different Ethernet standards common MAC protocol and frame format ...
PPT - WordPress.com
... that are not restricted to a physical switch segment. - The devices or users in a VLAN can be grouped by function, department, and application, regardless of their physical segment location. - A VLAN creates a single broadcast domain that is not restricted to a physical segment and is treated like a ...
... that are not restricted to a physical switch segment. - The devices or users in a VLAN can be grouped by function, department, and application, regardless of their physical segment location. - A VLAN creates a single broadcast domain that is not restricted to a physical segment and is treated like a ...
HEAnet`s UCLP Contact
... network topology (that's why the system is called User Controled Lighpath Provisioning). ...
... network topology (that's why the system is called User Controled Lighpath Provisioning). ...
Firewall
... (C) A firewall is not always a single computer. For example, a firewall may consist of a pair of filtering routers and one or more proxy servers running on one or more bastion hosts, all connected to a small, dedicated LAN between the two routers. The external router blocks attacks that use IP to br ...
... (C) A firewall is not always a single computer. For example, a firewall may consist of a pair of filtering routers and one or more proxy servers running on one or more bastion hosts, all connected to a small, dedicated LAN between the two routers. The external router blocks attacks that use IP to br ...
Module 11: TCP/IP Transport and Application Layer
... Registered port numbers are those registered for vendor-specific applications. Most of these are above 1024. ...
... Registered port numbers are those registered for vendor-specific applications. Most of these are above 1024. ...
3GPP2 “Evolving to Future Wireless Technology”
... Network comprising a variety of interworking access systems connected to a common packet-based core network Various access systems (e.g. 3G cellular, a new radio Interface, W-LAN, Short range radio, and wired access, etc.) will be connected via flexible core networks. User can be connected via a ...
... Network comprising a variety of interworking access systems connected to a common packet-based core network Various access systems (e.g. 3G cellular, a new radio Interface, W-LAN, Short range radio, and wired access, etc.) will be connected via flexible core networks. User can be connected via a ...