Palo Alto Networks Administrator’s Guide Release 5.0
... © 2007-2013 Palo Alto Networks. All rights reserved. Palo Alto Networks, PAN-OS, and Panorama are trademarks of Palo Alto Networks, Inc. All other trademarks are the property of their respective owners. P/N 810-000107-00D ...
... © 2007-2013 Palo Alto Networks. All rights reserved. Palo Alto Networks, PAN-OS, and Panorama are trademarks of Palo Alto Networks, Inc. All other trademarks are the property of their respective owners. P/N 810-000107-00D ...
ProSafe VPN Firewall 50 FVS338 Reference Manual
... Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions, and the following disclaimer. 2. Redistributions in binary ...
... Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions, and the following disclaimer. 2. Redistributions in binary ...
Access and Communication Servers Release Notes for Cisco IOS
... Communication Servers Command Reference publications, which are located in the Cisco IOS Release 10.3 database. (Note that the two addenda are not separate documents on the CD, because the information in them has been incorporated into the electronic documents.) For printed protocol translation docu ...
... Communication Servers Command Reference publications, which are located in the Cisco IOS Release 10.3 database. (Note that the two addenda are not separate documents on the CD, because the information in them has been incorporated into the electronic documents.) For printed protocol translation docu ...
Monitoring and Troubleshooting Guide
... transfer, or otherwise revise this publication without notice. ...
... transfer, or otherwise revise this publication without notice. ...
Routing and Forwarding
... Exterior gateway protocol – carries the reachability information Advertises complete paths as an enumerated list of ASs to reach a particular network BGP could announce the routes, withdraw some router, or refuse to announce a route to a particular AS even if it has one Dr. Ramana ( I.I.T Rajasthan ...
... Exterior gateway protocol – carries the reachability information Advertises complete paths as an enumerated list of ASs to reach a particular network BGP could announce the routes, withdraw some router, or refuse to announce a route to a particular AS even if it has one Dr. Ramana ( I.I.T Rajasthan ...
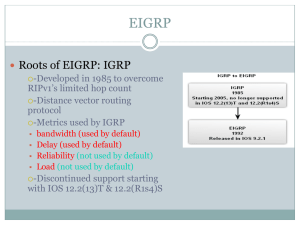
EIGRP
... routing tables for each Network layer protocol. • The IP-EIGRP module is responsible for sending and receiving EIGRP packets that are encapsulated in IP and for using DUAL to build and maintain the IP routing table. • The IPX EIGRP module is responsible for exchanging routing information about IPX n ...
... routing tables for each Network layer protocol. • The IP-EIGRP module is responsible for sending and receiving EIGRP packets that are encapsulated in IP and for using DUAL to build and maintain the IP routing table. • The IPX EIGRP module is responsible for exchanging routing information about IPX n ...
Wireless Security
... methods that the 802.11 standard defines for clients to connect to an access point. The association process can be broken down into three elements known as probe, authentication, and association. This section will explain both authentication methods. ...
... methods that the 802.11 standard defines for clients to connect to an access point. The association process can be broken down into three elements known as probe, authentication, and association. This section will explain both authentication methods. ...
WiNG 5.X How-To Guide
... When enabled on an Access Point, Auto IPsec Secure is initiated when the MINT link is established from the Access Point to the Wireless Controller. Tunnel establishment can be initiated using DHCP options or static controller host entries defined directly on the Access Point during pre-stating or wi ...
... When enabled on an Access Point, Auto IPsec Secure is initiated when the MINT link is established from the Access Point to the Wireless Controller. Tunnel establishment can be initiated using DHCP options or static controller host entries defined directly on the Access Point during pre-stating or wi ...
vPath - Cisco Communities
... topology. Example, If the firewall is plugged into the Internet connection and then the load balancer into firewall, the path of traffic must always flow in that ...
... topology. Example, If the firewall is plugged into the Internet connection and then the load balancer into firewall, the path of traffic must always flow in that ...
Vipersat CDM-570/570L
... ©2012 by Comtech EF Data, Inc. All rights reserved. No part of this manual may be copied or reproduced without prior written permission of Comtech EF Data, Inc. IMPORTANT NOTE: The information contained in this document supersedes all previously published information regarding this product. Product ...
... ©2012 by Comtech EF Data, Inc. All rights reserved. No part of this manual may be copied or reproduced without prior written permission of Comtech EF Data, Inc. IMPORTANT NOTE: The information contained in this document supersedes all previously published information regarding this product. Product ...
TCP
... • Decisions by IESG (as of Feb. 2001, 14 elected members) • IAB stimulates IETF / IESG actions – Members elected by “Internet Society“ (ISOC) ...
... • Decisions by IESG (as of Feb. 2001, 14 elected members) • IAB stimulates IETF / IESG actions – Members elected by “Internet Society“ (ISOC) ...
Setup - Cybarcode, Inc.
... operate in a standard network environment, such as Novell NetWare, Artisoft LANtastic, IBM LAN Server, or Microsoft LAN Manager. In these environments, FMT1000 Series computers can load and run most network-aware DOS applications. Data may be collected through bar code readers such as wands, las ...
... operate in a standard network environment, such as Novell NetWare, Artisoft LANtastic, IBM LAN Server, or Microsoft LAN Manager. In these environments, FMT1000 Series computers can load and run most network-aware DOS applications. Data may be collected through bar code readers such as wands, las ...
trunk - Victoria College
... – An ISL-configured router allows interVLAN communication – Non-ISL devices that receive ISL frames might consider them to be errors as the size of the frame exceeds the maximum transmission unit (MTU) size • MTU for Ethernet is 1500 bytes www.ciscopress.com ...
... – An ISL-configured router allows interVLAN communication – Non-ISL devices that receive ISL frames might consider them to be errors as the size of the frame exceeds the maximum transmission unit (MTU) size • MTU for Ethernet is 1500 bytes www.ciscopress.com ...
Voice over IP
... Different NAT Behaviors... Mainly for stateless UDP sessions like RTP streams Symmetric NAT: one entry only for a specific 5-uple
Full-Cone NAT: one entry only a for a 3-uple
Restricted-Cone NAT: on ...
... Different NAT Behaviors... Mainly for stateless UDP sessions like RTP streams Symmetric NAT: one entry only for a specific 5-uple
Ubuntu Server Guide
... 2 https://launchpad.net/~ubuntu-core-doc 3 https://launchpad.net/~ubuntu-server 4 https://help.ubuntu.com/community/ 5 https://code.launchpad.net/serverguide 6 https://code.launchpad.net/ubuntu-docs ...
... 2 https://launchpad.net/~ubuntu-core-doc 3 https://launchpad.net/~ubuntu-server 4 https://help.ubuntu.com/community/ 5 https://code.launchpad.net/serverguide 6 https://code.launchpad.net/ubuntu-docs ...
EMC Infrastructure for Microsoft Private Cloud
... while providing an easy-to-manage environment. This solution provides a simplified architecture to host different business applications, ensuring that each business line’s information is separated from that of the others. It greatly simplifies the environment and reduces operational and management c ...
... while providing an easy-to-manage environment. This solution provides a simplified architecture to host different business applications, ensuring that each business line’s information is separated from that of the others. It greatly simplifies the environment and reduces operational and management c ...
Advanced Routing - Fortinet Document Library
... routes. BGP is the only routing protocol to use TCP for a transport protocol. Open Shortest Path First (OSPF) provides background on the specific protocol explaining terms used and how the protocol works, as well as providing some troubleshooting information and examples on configuring the protocols ...
... routes. BGP is the only routing protocol to use TCP for a transport protocol. Open Shortest Path First (OSPF) provides background on the specific protocol explaining terms used and how the protocol works, as well as providing some troubleshooting information and examples on configuring the protocols ...
CPS Operations Guide
... In CPS, the active and standby strategy applies only to the secondary (02) load balancers. Recall that the four load balancers are in the system are these: ...
... In CPS, the active and standby strategy applies only to the secondary (02) load balancers. Recall that the four load balancers are in the system are these: ...
2 Huawei LTE PTT Broadband Trunking Solution
... Similar to the public mobile communications network, the trunking communications network is also developed from the analog technology to the digital technology and from only having voice services to having voice and data services. The 1G trunking communications network is an analog system that uses ...
... Similar to the public mobile communications network, the trunking communications network is also developed from the analog technology to the digital technology and from only having voice services to having voice and data services. The 1G trunking communications network is an analog system that uses ...
CCNPv5 Module 5 Lesson 10
... authentication, a NTP access group can be created and a basic IP ACL applied to it To control access to NTP services, use the ntp access-group command in global configuration mode The access group options are scanned in the following order, from least restrictive to most restrictive: 1. peer: Allows ...
... authentication, a NTP access group can be created and a basic IP ACL applied to it To control access to NTP services, use the ntp access-group command in global configuration mode The access group options are scanned in the following order, from least restrictive to most restrictive: 1. peer: Allows ...
3rd Edition, Chapter 5
... 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully utilize channel ...
... 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully utilize channel ...
PDF - ZTE Deutschland GmbH
... Competition is the driver for innovation and developments. Hurdles are the obstacles to develop technologies with freedom, i.e. technology neutrality for frequencies. This has to be liberalized in Belarus. Other markets with open policy have proven the huge positive value to end users and to the ent ...
... Competition is the driver for innovation and developments. Hurdles are the obstacles to develop technologies with freedom, i.e. technology neutrality for frequencies. This has to be liberalized in Belarus. Other markets with open policy have proven the huge positive value to end users and to the ent ...
Business Ready Branch Solutions for Enterprise and Small
... surveillance cameras, cash registers, kiosks, and inventory scanners all require the connection to the corporate network over the LAN. This assortment of devices requires simplified connectivity tailored to the demands of each device. For example, devices such as IP telephones or cameras may be powe ...
... surveillance cameras, cash registers, kiosks, and inventory scanners all require the connection to the corporate network over the LAN. This assortment of devices requires simplified connectivity tailored to the demands of each device. For example, devices such as IP telephones or cameras may be powe ...