Routing - University of Pittsburgh
... route computation using Dijkstra’s algorithm OSPF advertisement carries one entry per neighbor ...
... route computation using Dijkstra’s algorithm OSPF advertisement carries one entry per neighbor ...
07.ciulli - Future Internet Assembly
... [Q2] What is the benefit for an SME to be active in NFV and SDN standardization? SDN & NFV have their hype today, but consolidated specifications are still to come ([open] interfaces, detailed architecture, etc.) Standards here are still a intricate jungle… difficult to predict where things wil ...
... [Q2] What is the benefit for an SME to be active in NFV and SDN standardization? SDN & NFV have their hype today, but consolidated specifications are still to come ([open] interfaces, detailed architecture, etc.) Standards here are still a intricate jungle… difficult to predict where things wil ...
Sidh
... build specifically to simulate the Berkeley MICA Mote hardware platform running applications built on TinyOS. In the name of efficiency TOSIM uses an inaccurate probabilistic bit error model for the wireless medium. This is sufficient when evaluating a high level application, but not when evaluating ...
... build specifically to simulate the Berkeley MICA Mote hardware platform running applications built on TinyOS. In the name of efficiency TOSIM uses an inaccurate probabilistic bit error model for the wireless medium. This is sufficient when evaluating a high level application, but not when evaluating ...
NAME: UKURA EMMANUEL BEMSEN DEPTARTMENT
... Hubs: A central point of connection between media segments enabling network extension to accommodate more PC’s. Bridges: used to connect two different LANs or two segments of the same LAN by forwarding traffic between segments. Multiplexer: used to share a communication line among a number of ...
... Hubs: A central point of connection between media segments enabling network extension to accommodate more PC’s. Bridges: used to connect two different LANs or two segments of the same LAN by forwarding traffic between segments. Multiplexer: used to share a communication line among a number of ...
detailed concept of integrated services digital network
... and The basic advantage of ISDN is to facilitate Exchange Termination (ET) on the the user with multiple digital channels provider's site. which can operate concurrently through the same one copper wire pair. It provides high 3.2 ISDN SERVICES data rate because of digital scheme which is The two dif ...
... and The basic advantage of ISDN is to facilitate Exchange Termination (ET) on the the user with multiple digital channels provider's site. which can operate concurrently through the same one copper wire pair. It provides high 3.2 ISDN SERVICES data rate because of digital scheme which is The two dif ...
Wireless Expands M D to More of the Plant
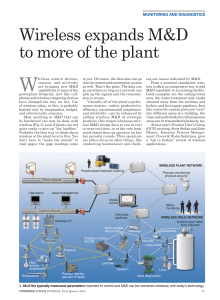
... and the solutions, or what you actually do with the monitored points. The links and infrastructure (Fig 2) are industrial, ruggedized versions of similar equipment you use at home or in the office. Each field device has an antenna which transmits a signal through an industrial-grade point accessing ...
... and the solutions, or what you actually do with the monitored points. The links and infrastructure (Fig 2) are industrial, ruggedized versions of similar equipment you use at home or in the office. Each field device has an antenna which transmits a signal through an industrial-grade point accessing ...
Internet 2
... (since this node has PDP context information, including the dynamically allocated IP address of MS). ...
... (since this node has PDP context information, including the dynamically allocated IP address of MS). ...
NENA Emergency Services IP Network Design for NG9-1
... Patents may cover the specifications, techniques, or network interface/system characteristics disclosed herein. No license expressed or implied is hereby granted. This document shall not be construed as a suggestion to any manufacturer to modify or change any of its products, nor does this document ...
... Patents may cover the specifications, techniques, or network interface/system characteristics disclosed herein. No license expressed or implied is hereby granted. This document shall not be construed as a suggestion to any manufacturer to modify or change any of its products, nor does this document ...
MAPPING DIRECTED NETWORKS∗ 1. Background and notation
... and studied using the tools of linear algebra. Perhaps most notably, spectral information involving eigenvectors or, more generally, singular vectors, can be used for data mining tasks such as clustering, reordering and discovering various types of substructure [2, 7, 11, 15]. We focus here on the c ...
... and studied using the tools of linear algebra. Perhaps most notably, spectral information involving eigenvectors or, more generally, singular vectors, can be used for data mining tasks such as clustering, reordering and discovering various types of substructure [2, 7, 11, 15]. We focus here on the c ...
8 - 1 - WVU College of Business and Economics
... Approaches of Using ATM in Backbone • LAN Emulation (LANE) – Breaking LAN frame into 48-byte long blocks and transmit them in an ATM cell – Called encapsulation and done by edge switches – Reassembling done at the destination edge switch and LAN frame is sent to the LAN – Requires translating of MA ...
... Approaches of Using ATM in Backbone • LAN Emulation (LANE) – Breaking LAN frame into 48-byte long blocks and transmit them in an ATM cell – Called encapsulation and done by edge switches – Reassembling done at the destination edge switch and LAN frame is sent to the LAN – Requires translating of MA ...
ppt
... Slice: a set of d vservers, each on a different node A node can concurrently support many slices (experiments) Figure 3-15. The basic organization of a PlanetLab node. Tanenbaum & Van Steen, Distributed Systems: Principles and Paradigms, 2e, (c) 2007 Prentice-Hall, Inc. All rights reserved. 0-13-239 ...
... Slice: a set of d vservers, each on a different node A node can concurrently support many slices (experiments) Figure 3-15. The basic organization of a PlanetLab node. Tanenbaum & Van Steen, Distributed Systems: Principles and Paradigms, 2e, (c) 2007 Prentice-Hall, Inc. All rights reserved. 0-13-239 ...
Implementation Options for the Distribution System in the 802.11
... desktop computer Amre El-Hoiydi, CSEM ...
... desktop computer Amre El-Hoiydi, CSEM ...
Generic and Automatic Address Configuration for Data Center Networks
... for hardware and the standard TCP/IP protocol suite for inter-server communication. This choice provides the best performance to price trade-off [2]. All the servers are connected via network switches to form a large distributed system. Before the servers and switches can provide any useful services ...
... for hardware and the standard TCP/IP protocol suite for inter-server communication. This choice provides the best performance to price trade-off [2]. All the servers are connected via network switches to form a large distributed system. Before the servers and switches can provide any useful services ...
Fault Classification in double circuit transmission lines using ANN
... Line-Line to ground fault - 10-17%, Line-Line fault – 8-10%,three phase – 2-3%.The causes of temporary faults include lightning, conductors slapping together in the wind, tree branches that fall across conductors and then fall or burn off and insulator flashovers caused by pollution. Faults that are ...
... Line-Line to ground fault - 10-17%, Line-Line fault – 8-10%,three phase – 2-3%.The causes of temporary faults include lightning, conductors slapping together in the wind, tree branches that fall across conductors and then fall or burn off and insulator flashovers caused by pollution. Faults that are ...
Junos OS: The Power of One Operating System
... for customers to manage and operate its networking and security platforms in multivendor networks. Junos OS provides multiple open interfaces, such as RADIUS, NETCONF/XML and DMI, for policy control, network management, and integration to other operations systems. The time tested interoperability an ...
... for customers to manage and operate its networking and security platforms in multivendor networks. Junos OS provides multiple open interfaces, such as RADIUS, NETCONF/XML and DMI, for policy control, network management, and integration to other operations systems. The time tested interoperability an ...
Clean Slate Design for the Internet
... A clean separation between the substrate and an open programming environment A simple hardware substrate that generalizes, subsumes and simplifies the current substrate ...
... A clean separation between the substrate and an open programming environment A simple hardware substrate that generalizes, subsumes and simplifies the current substrate ...
No Slide Title
... proprietary solutions in equipment), but there is no IEEEsupported reachability solution available. Handovers between different WLANs require Mobile IP (which offers also reachability). Unfortunately, Mobile IP includes a non-transparent mechanism (Discovering Careof Address) that must be implemente ...
... proprietary solutions in equipment), but there is no IEEEsupported reachability solution available. Handovers between different WLANs require Mobile IP (which offers also reachability). Unfortunately, Mobile IP includes a non-transparent mechanism (Discovering Careof Address) that must be implemente ...
3. Centralized versus Distributed Mobility
... host-based solution. On the other hand, localized routing with PMIPv6 [RFC6705] addresses only a part of the problem where both the MN and the correspondent node (CN) are attached to the same MAG, and it is not applicable when the CN does not behave like an MN.) PS2: Divergence from other evolutiona ...
... host-based solution. On the other hand, localized routing with PMIPv6 [RFC6705] addresses only a part of the problem where both the MN and the correspondent node (CN) are attached to the same MAG, and it is not applicable when the CN does not behave like an MN.) PS2: Divergence from other evolutiona ...
An Embedded Dynamic Security Networking
... the openness of wireless radiation has brought a huge security risk to the wireless network. So it is a very important development bottleneck that how to achieve security under fast networking. In reference [1], LiuJun has put forward a cognitive wireless ad-hoc network topology control algorithm wh ...
... the openness of wireless radiation has brought a huge security risk to the wireless network. So it is a very important development bottleneck that how to achieve security under fast networking. In reference [1], LiuJun has put forward a cognitive wireless ad-hoc network topology control algorithm wh ...
Detecting Spam at the Network Level
... constantly flooded with unsolicited messages is that spam is profitable. As such, spam detection is likely to remain an “open battlefield” in the coming years. Nowadays, the most common countermeasures against spam are spam filters. Mail servers usually host the core of spam filtering operations: to ...
... constantly flooded with unsolicited messages is that spam is profitable. As such, spam detection is likely to remain an “open battlefield” in the coming years. Nowadays, the most common countermeasures against spam are spam filters. Mail servers usually host the core of spam filtering operations: to ...
Chapter 13
... Resides on particular computer or server (the host) and monitors activity only on that system Also known as system integrity verifiers Benchmark/monitor status of key system files Triggers alert when file attributes change, new files are created, or existing files are deleted Managed HIDPS ...
... Resides on particular computer or server (the host) and monitors activity only on that system Also known as system integrity verifiers Benchmark/monitor status of key system files Triggers alert when file attributes change, new files are created, or existing files are deleted Managed HIDPS ...
Clean Slate Design for the Internet
... • Most complexity is about routing: picking paths, managing location, identity and access. • The current network controls the routing. • Routing doesn’t belong in the boxes. • If we control routing, we can innovate. Uh-oh, looks like another GENI talk… ...
... • Most complexity is about routing: picking paths, managing location, identity and access. • The current network controls the routing. • Routing doesn’t belong in the boxes. • If we control routing, we can innovate. Uh-oh, looks like another GENI talk… ...
QoS Terminology and Parameters
... QOS: Quality of Service (QoS) implies the ability to differentiate traffic streams and to define a level of performance for those traffic streams across a network. When heavily utilized networks are carrying various types of traffic for different users, QoS is a mean of offering better service May-1 ...
... QOS: Quality of Service (QoS) implies the ability to differentiate traffic streams and to define a level of performance for those traffic streams across a network. When heavily utilized networks are carrying various types of traffic for different users, QoS is a mean of offering better service May-1 ...
Ad-hoc networks
... Example of a basic routing algorithm Routing protocols IP configuring Security ...
... Example of a basic routing algorithm Routing protocols IP configuring Security ...
Chapter 5
... (There is also a “don’t fragment bit” that can be set). Fragment offset contains the offset (in 8-byte units) of current fragment in the original datagram. Total length is changed to be the size of the fragment. Panwar, Mao, Ryoo, Li: TCP/IP Essentials ...
... (There is also a “don’t fragment bit” that can be set). Fragment offset contains the offset (in 8-byte units) of current fragment in the original datagram. Total length is changed to be the size of the fragment. Panwar, Mao, Ryoo, Li: TCP/IP Essentials ...