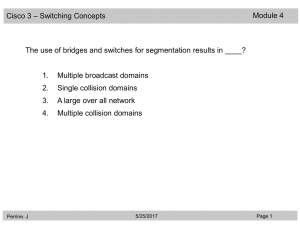
CCNA3 3.0-04 Questions Review of Switching
... After a collision occurs on a half-duplex Ethernet network, how does a transmitting host proceed? (Choose two.) ...
... After a collision occurs on a half-duplex Ethernet network, how does a transmitting host proceed? (Choose two.) ...
Figure 9 - Alcatel-Lucent Enterprise
... To benefit from this document, the reader will have a solid understanding of various networking technologies at the ACPS or similar level. ...
... To benefit from this document, the reader will have a solid understanding of various networking technologies at the ACPS or similar level. ...
Audio Gateway Handbook
... to or from the network to which it is associated. For example, a radio attached to the gateway will be programmed to transmit or receive on a particular channel or talk group. The radio will be configured for a particular modulation scheme or features, such as encryption, as needed for communication ...
... to or from the network to which it is associated. For example, a radio attached to the gateway will be programmed to transmit or receive on a particular channel or talk group. The radio will be configured for a particular modulation scheme or features, such as encryption, as needed for communication ...
ASD's Top Cyber Intrusion Mitigation Strategies
... By addressing the exploit techniques required to execute an attack, Palo Alto Networks has built modules to mitigate and interfere with the attacker’s exploit techniques. Since an exploit is always based on a chain of techniques, preventing the use of any technique in the chain will block the exploi ...
... By addressing the exploit techniques required to execute an attack, Palo Alto Networks has built modules to mitigate and interfere with the attacker’s exploit techniques. Since an exploit is always based on a chain of techniques, preventing the use of any technique in the chain will block the exploi ...
ASI5308, ASI5316, ASI6316
... supported through a standard communications protocol. CobraNet compliant devices are based on a common silicon or hardware reference design from Cirrus Logic. The Cirrus Logic website, www.cobranet.info, is dedicated to CobraNet. Wikipedia has a useful introduction to CobraNet here (http://en.wikipe ...
... supported through a standard communications protocol. CobraNet compliant devices are based on a common silicon or hardware reference design from Cirrus Logic. The Cirrus Logic website, www.cobranet.info, is dedicated to CobraNet. Wikipedia has a useful introduction to CobraNet here (http://en.wikipe ...
Topology
... • Determines to which port the destination device is connected and forwards the message to that port – This capability allows a switch to handle several conversations at one time, thereby providing the full network bandwidth to each device rather than requiring bandwidth sharing Guide to Networking ...
... • Determines to which port the destination device is connected and forwards the message to that port – This capability allows a switch to handle several conversations at one time, thereby providing the full network bandwidth to each device rather than requiring bandwidth sharing Guide to Networking ...
How to Configure BGP Tech Note Revision A
... the Redistribution Profiles tab in the Filter Type section. You might be tempted to check the “bgp” checkbox here, but bear in mind that you are redistributing a route to a directly connected network, the 203.0.113.0/24 network. In this case, you will need to check the “connect” box instead. Follow ...
... the Redistribution Profiles tab in the Filter Type section. You might be tempted to check the “bgp” checkbox here, but bear in mind that you are redistributing a route to a directly connected network, the 203.0.113.0/24 network. In this case, you will need to check the “connect” box instead. Follow ...
AZ26337342
... symmetric links because the route reply packet follows the reverse path of route request packet. As the route reply packet traverses back to the source, the nodes along the path enter the forward route into ...
... symmetric links because the route reply packet follows the reverse path of route request packet. As the route reply packet traverses back to the source, the nodes along the path enter the forward route into ...
presentation
... Differentiated Services At the Ingress/Egress nodes Classify packets via packet inspection Meter the temporal state of the packet (i.e., rate) Mark the packets’ Diffserv Code Point (DSCP) according to its class Shape the packets (drop or delay) At other nodes, Per-Hop Behavior (PHB) is appli ...
... Differentiated Services At the Ingress/Egress nodes Classify packets via packet inspection Meter the temporal state of the packet (i.e., rate) Mark the packets’ Diffserv Code Point (DSCP) according to its class Shape the packets (drop or delay) At other nodes, Per-Hop Behavior (PHB) is appli ...
CPDLC latency times
... Explanation of ground based NEMO NEMO (Network Mobility) is an extension to Mobile IPv6 that enables entire networks to attach at different points in a network and allowing every node on the Mobile Network to be reachable while moving around. This is implemented so that the Mobile Router, connecting ...
... Explanation of ground based NEMO NEMO (Network Mobility) is an extension to Mobile IPv6 that enables entire networks to attach at different points in a network and allowing every node on the Mobile Network to be reachable while moving around. This is implemented so that the Mobile Router, connecting ...
Defining Networks with the OSI Model
... of information between domain controllers, transfer of browse lists, and other common functions. TCP can only be used for one-to-one communications. • UDP is often used for one-to-many communications, using broadcast or multicast IP datagrams Protocol ...
... of information between domain controllers, transfer of browse lists, and other common functions. TCP can only be used for one-to-one communications. • UDP is often used for one-to-many communications, using broadcast or multicast IP datagrams Protocol ...
IP - High Speed Network
... Mobile tracking = Mobile registration + updating The procedure by which a network node determines the location of the MT for the delivery of incoming calls May be executed explicitly prior to call setup or may be an integral part of the call setup procedure ...
... Mobile tracking = Mobile registration + updating The procedure by which a network node determines the location of the MT for the delivery of incoming calls May be executed explicitly prior to call setup or may be an integral part of the call setup procedure ...
Chapter 1. Introduction to Data Communications
... • More complex than switches or routers • Connect two or more networks that use the same or different data link and network protocols • Some work at the application layer ...
... • More complex than switches or routers • Connect two or more networks that use the same or different data link and network protocols • Some work at the application layer ...
Lecture_5_Routing Protocols
... Link State Routing Protocol information about adjacencies (neighborship) sent to all routers only when there is a change Examples are OSPF and IS-IS ...
... Link State Routing Protocol information about adjacencies (neighborship) sent to all routers only when there is a change Examples are OSPF and IS-IS ...
White Paper - DC
... • Signals appear and disappear simply because you move your phone six inches • You can hear the other person, but they can’t hear you • Calls get “Dropped” and require re-connection • Problems are compounded by reflections inside of buildings (multipath) • Interference from other RF sources garbles ...
... • Signals appear and disappear simply because you move your phone six inches • You can hear the other person, but they can’t hear you • Calls get “Dropped” and require re-connection • Problems are compounded by reflections inside of buildings (multipath) • Interference from other RF sources garbles ...
OfficeServ 7400-GWIM User Manual
... When Setting PPTP in Windows XP/2000 In Windows XP/2000, the administrator can use DHCP client. If VPN PPTP client is connected while the DHCP client is operating, errors will be found. To prevent this problem, close the DHCP client operation on the [Start] Æ [Program] Æ [Administrative Tools] Æ [Se ...
... When Setting PPTP in Windows XP/2000 In Windows XP/2000, the administrator can use DHCP client. If VPN PPTP client is connected while the DHCP client is operating, errors will be found. To prevent this problem, close the DHCP client operation on the [Start] Æ [Program] Æ [Administrative Tools] Æ [Se ...
Layer 3 Multiprotocol Label Switching Vir-
... It also offers a guaranteed bandwidth solutions, in which customers can provide voice and data services with point-to-point guarantees with a predictable delivery at a various network conditions to address the traditional IP networking limitations. 2.3 MPLS Operation The basic idea of MPLS is to sep ...
... It also offers a guaranteed bandwidth solutions, in which customers can provide voice and data services with point-to-point guarantees with a predictable delivery at a various network conditions to address the traditional IP networking limitations. 2.3 MPLS Operation The basic idea of MPLS is to sep ...
Introduction
... Routed Protocols provide enough information in their network layer address to allow packets to be forwarded from one host to another host based on the addressing scheme. Examples: ...
... Routed Protocols provide enough information in their network layer address to allow packets to be forwarded from one host to another host based on the addressing scheme. Examples: ...
A41040105
... count and rebroadcast the RREQ. If in the path does not have the route to the destination node, the intermediate nodes having valid route towards the destination node .which replies with a unicast RREQ. Every node keeps track of a previous node. The HELLO messages are broadcasted periodically, if ne ...
... count and rebroadcast the RREQ. If in the path does not have the route to the destination node, the intermediate nodes having valid route towards the destination node .which replies with a unicast RREQ. Every node keeps track of a previous node. The HELLO messages are broadcasted periodically, if ne ...
Denial-of-Service detection in 6LoWPAN based Internet of Things
... which one device is associated or connected with a part of network or similar devices. During the bootstrapping phase, a unique identity and other security parameters are associated with each device/thing. Secure bootstrapping ensures that only authenticated devices access the network. The simplest ...
... which one device is associated or connected with a part of network or similar devices. During the bootstrapping phase, a unique identity and other security parameters are associated with each device/thing. Secure bootstrapping ensures that only authenticated devices access the network. The simplest ...
Mobile Networking
... – Applications and Supporting Protocols (Transport, Application layers) • New applications that make it possible to use services across different networks – Video data rate automatically reduced when move from WiFi to WiMax ...
... – Applications and Supporting Protocols (Transport, Application layers) • New applications that make it possible to use services across different networks – Video data rate automatically reduced when move from WiFi to WiMax ...
ppt
... • Addressing determines which packets are kept and which are packets are thrown away • Packets can be sent to: • Unicast – one destination • Multicast – group of nodes (e.g. “everyone playing Quake”) • Broadcast – everybody on wire ...
... • Addressing determines which packets are kept and which are packets are thrown away • Packets can be sent to: • Unicast – one destination • Multicast – group of nodes (e.g. “everyone playing Quake”) • Broadcast – everybody on wire ...
Troubleshooting File and Printer Sharing in Microsoft Windows XP
... locally attached printers with other computers on a home and small office network. File and printer sharing must first be enabled, and to share files you can use the Shared Documents folder, simple file sharing, or advanced file sharing. Once a folder or printer is shared, other users on the home ne ...
... locally attached printers with other computers on a home and small office network. File and printer sharing must first be enabled, and to share files you can use the Shared Documents folder, simple file sharing, or advanced file sharing. Once a folder or printer is shared, other users on the home ne ...
AW+ Next-Generation Firewall Overview
... Deep Packet Inspection (DPI) firewall The AlliedWare Plus firewall is a next-generation Deep Packet Inspection (DPI) engine that provides real-time, Layer 7 classification of network traffic. It inspects every packet that passes through, and accurately identifies in use applications, for example soc ...
... Deep Packet Inspection (DPI) firewall The AlliedWare Plus firewall is a next-generation Deep Packet Inspection (DPI) engine that provides real-time, Layer 7 classification of network traffic. It inspects every packet that passes through, and accurately identifies in use applications, for example soc ...
microsoft05 - Princeton University
... – Compile high-level spec into box configuration – But, today’s systems have a lot of complexity ...
... – Compile high-level spec into box configuration – But, today’s systems have a lot of complexity ...