Physical plane for Intelligent Network Capability Set 2
... The SN can control IN-based services and engage in flexible information interactions with users. The SN communicates directly with one or more SSPs, each with a point-to-point signalling and transport connection. Functionally, the SN contains an SCF, SDF, SRF, and an SSF/CCF. This SSF/CCF is closely ...
... The SN can control IN-based services and engage in flexible information interactions with users. The SN communicates directly with one or more SSPs, each with a point-to-point signalling and transport connection. Functionally, the SN contains an SCF, SDF, SRF, and an SSF/CCF. This SSF/CCF is closely ...
Defending Network-Based Services Against Denial of Service Attacks
... end hosts or multicast enabled subnets [6] [8]. Rate limiting can be effective against state overload attacks that involve one or more attack hosts within the same subnet. However, rate limiting without knowledge about which join requests are valid can have an adverse effect on legitimate join reque ...
... end hosts or multicast enabled subnets [6] [8]. Rate limiting can be effective against state overload attacks that involve one or more attack hosts within the same subnet. However, rate limiting without knowledge about which join requests are valid can have an adverse effect on legitimate join reque ...
Network Topologies and Technologies
... A logical bus topology can be implemented as a physical bus (although this topology is now obsolete). When a logical bus is implemented as a physical star using wired Ethernet, the center of the star is an Ethernet hub. Whatever the physical topology is, data transmitted from a computer is received ...
... A logical bus topology can be implemented as a physical bus (although this topology is now obsolete). When a logical bus is implemented as a physical star using wired Ethernet, the center of the star is an Ethernet hub. Whatever the physical topology is, data transmitted from a computer is received ...
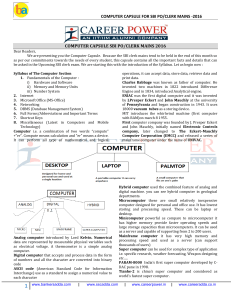
computer capsule for sbi po/clerk mains -2016
... An Arithmetic Logic Unit (ALU) is a digital circuit that performs integer arithmetic and logical operations. The ALU is a fundamental building block of the central processing unit of a computer Control Unit is responsible for controlling the overall operations of computer. It coordinates the sequenc ...
... An Arithmetic Logic Unit (ALU) is a digital circuit that performs integer arithmetic and logical operations. The ALU is a fundamental building block of the central processing unit of a computer Control Unit is responsible for controlling the overall operations of computer. It coordinates the sequenc ...
computer network interview questions with answers
... redundancy methods are parity check, cyclic redundancy check (CRC), and checksum. 42.Define parity check. Ans: In parity check, a parity bit is added to every data unit so that the total number of 1s is even (or odd for odd parity).Simple parity check can detect all single bit errors. It can detect ...
... redundancy methods are parity check, cyclic redundancy check (CRC), and checksum. 42.Define parity check. Ans: In parity check, a parity bit is added to every data unit so that the total number of 1s is even (or odd for odd parity).Simple parity check can detect all single bit errors. It can detect ...
15-744: Computer Networking
... • E.g. www.cmu.edu • Globally unique (can correspond to multiple hosts) ...
... • E.g. www.cmu.edu • Globally unique (can correspond to multiple hosts) ...
Digital Audio Snake
... outputs, the system can accommodate additional tiers of addresses allowing an unlimited amount of input channels. This is achieved by the user turning off eight channels of inputs and turning on an upper tier of channels. Catalyst software allows you to route any input to any number of outputs. You ...
... outputs, the system can accommodate additional tiers of addresses allowing an unlimited amount of input channels. This is achieved by the user turning off eight channels of inputs and turning on an upper tier of channels. Catalyst software allows you to route any input to any number of outputs. You ...
Cisco ME 6500 Series Ethernet Switch
... in identifying user’s MAC and IP address and port number, hence preventing attacks from malicious users. Malicious attacks can jeopardize the functionality of the network by compromising the switch CPU, MAC table, etc. Features such as Port Security and Per-VLAN MAC Limiting restrict the number of M ...
... in identifying user’s MAC and IP address and port number, hence preventing attacks from malicious users. Malicious attacks can jeopardize the functionality of the network by compromising the switch CPU, MAC table, etc. Features such as Port Security and Per-VLAN MAC Limiting restrict the number of M ...
DFL-M510 A3_Manual V1.02 - D-Link
... CHAPTER 1: GETTING STARTED WITH THE DFL-M510 The DFL-M5 10 is a transparent network device. To ensure there is no disruption to your network, it can be installed in In-Line mode with a hardware bypass function enabled. The hardware bypass ensures that if the DFL-M510 crashes, or experiences a power ...
... CHAPTER 1: GETTING STARTED WITH THE DFL-M510 The DFL-M5 10 is a transparent network device. To ensure there is no disruption to your network, it can be installed in In-Line mode with a hardware bypass function enabled. The hardware bypass ensures that if the DFL-M510 crashes, or experiences a power ...
Paper Title (use style: paper title)
... defined yet a common strategy to allocate one-to-many and many-to-many multicast addresses. While multicast routers are capable to distinguish between ASM and SSM pool of addresses, they are unfortunately unable to trigger an optimal multicast routing protocol (i.e. unidirectional or bi-directional) ...
... defined yet a common strategy to allocate one-to-many and many-to-many multicast addresses. While multicast routers are capable to distinguish between ASM and SSM pool of addresses, they are unfortunately unable to trigger an optimal multicast routing protocol (i.e. unidirectional or bi-directional) ...
Internet Firewalls:
... be able to break into your network by completely bypassing your firewall, if he can find a ``helpful'' employee inside who can be fooled into giving access to a modem pool. Before deciding this isn't a problem in your organization, ask yourself how much trouble a contractor has getting logged into t ...
... be able to break into your network by completely bypassing your firewall, if he can find a ``helpful'' employee inside who can be fooled into giving access to a modem pool. Before deciding this isn't a problem in your organization, ask yourself how much trouble a contractor has getting logged into t ...
Towards an In-depth Understanding of Deep Packet Inspection
... training particularly in ICS packet analysis and attribution, vulnerability analysis, penetration testing, and challenge materials for cyber competitions. The rest of the paper is organized into three parts. First, we present a literature review of ICS protocols and technologies, deep packet inspect ...
... training particularly in ICS packet analysis and attribution, vulnerability analysis, penetration testing, and challenge materials for cyber competitions. The rest of the paper is organized into three parts. First, we present a literature review of ICS protocols and technologies, deep packet inspect ...
Manual D-Link AirPlus Xtreme G DWL-G810
... A WLAN is a computer network that transmits and receives data with radio signals instead of wires. WLANs are used increasingly in both home and office environments, and public areas such as airports, coffee shops and universities. Innovative ways to utilize WLAN technology are helping people to work ...
... A WLAN is a computer network that transmits and receives data with radio signals instead of wires. WLANs are used increasingly in both home and office environments, and public areas such as airports, coffee shops and universities. Innovative ways to utilize WLAN technology are helping people to work ...
Multimedia - Computer Science, Stony Brook University
... simultaneous users? option 2: store/serve multiple copies of videos at multiple geographically distributed sites (CDN) enter deep: push CDN servers deep into many access networks • close to users • used by Akamai, 1700 locations ...
... simultaneous users? option 2: store/serve multiple copies of videos at multiple geographically distributed sites (CDN) enter deep: push CDN servers deep into many access networks • close to users • used by Akamai, 1700 locations ...
A BingBee Phone Network - Computer Science
... serverless SIP. This paper also mentions how SIP has risen in popularity in recent years and how peer to peer networks are essential for supporting distributed services. SIP or “Session Initiation Protocol is an application-layer control (signalling) protocol for creating, modifying, and terminating ...
... serverless SIP. This paper also mentions how SIP has risen in popularity in recent years and how peer to peer networks are essential for supporting distributed services. SIP or “Session Initiation Protocol is an application-layer control (signalling) protocol for creating, modifying, and terminating ...
Voice Over IP
... •Associating a telephone number to a voice port •For instance, if a call comes in for 408 555-3737, the router needs to know that this phone is connected to FXS VIC 2/0/0. •Cisco IOS uses objects called dial peers to accomplish this task •Configuring dial peers is similar to configuring static IP ro ...
... •Associating a telephone number to a voice port •For instance, if a call comes in for 408 555-3737, the router needs to know that this phone is connected to FXS VIC 2/0/0. •Cisco IOS uses objects called dial peers to accomplish this task •Configuring dial peers is similar to configuring static IP ro ...
D-Link AirPlus Xtreme G DWL-G810
... technology. OFDM works by splitting the radio signal into multiple smaller sub-signals that are then transmitted simultaneously at different frequencies to the receiver. OFDM reduces the amount of crosstalk (interference) in signal transmissions. The D-Link DWLG810 will automatically sense the best ...
... technology. OFDM works by splitting the radio signal into multiple smaller sub-signals that are then transmitted simultaneously at different frequencies to the receiver. OFDM reduces the amount of crosstalk (interference) in signal transmissions. The D-Link DWLG810 will automatically sense the best ...
ARCAT spec 262600 2009-9-15
... this information, are responsible for ensuring the acceptability of each application and appropriate use of the guidelines. In no event will Rockwell Automation be liable for misuse, misapplication or reliance on these guidelines in connection with any specific application. Rockwell Automation also ...
... this information, are responsible for ensuring the acceptability of each application and appropriate use of the guidelines. In no event will Rockwell Automation be liable for misuse, misapplication or reliance on these guidelines in connection with any specific application. Rockwell Automation also ...
White Paper
... end user of an Ethernet service. This paper is intended for telecommunications engineers and technicians involved in the deployment and use of Ethernet services. It will be of particular interest to those who are familiar with SONET/SDH services and who now find themselves deploying the “new” Ethern ...
... end user of an Ethernet service. This paper is intended for telecommunications engineers and technicians involved in the deployment and use of Ethernet services. It will be of particular interest to those who are familiar with SONET/SDH services and who now find themselves deploying the “new” Ethern ...
DHCP
... DHCP reduces the complexity and amount of administrative work by using automatic TCP/IP configuration Manual TCP/IP Configuration ...
... DHCP reduces the complexity and amount of administrative work by using automatic TCP/IP configuration Manual TCP/IP Configuration ...
Flowpoint and SmartSwitch Router DSL Devices
... prior notice. The reader should in all cases consult Aprisma to determine whether any such changes have been made. ...
... prior notice. The reader should in all cases consult Aprisma to determine whether any such changes have been made. ...
Implementation of Extensible Authentication Protocol in OPNET
... EAP Authentication Exchange Process Step1. The authenticator sends a Request to authenticate the peer. The Request has a Type field to indicate what is being requested. Step2. The peer sends a Response packet in reply to a valid Request. As with the Request packet, the Response packet contains a Typ ...
... EAP Authentication Exchange Process Step1. The authenticator sends a Request to authenticate the peer. The Request has a Type field to indicate what is being requested. Step2. The peer sends a Response packet in reply to a valid Request. As with the Request packet, the Response packet contains a Typ ...
LAN - Temple CIS
... 6.1 introduction, services 6.5 link virtualization: MPLS 6.2 error detection, correction 6.6 data center networking 6.3 multiple access protocols 6.7 a day in the life of a web request 6.4 LANs ...
... 6.1 introduction, services 6.5 link virtualization: MPLS 6.2 error detection, correction 6.6 data center networking 6.3 multiple access protocols 6.7 a day in the life of a web request 6.4 LANs ...