SWIM: Scalable Weakly-consistent Infection-style Process Group Membership Protocol
... these group sizes is an increase in either the rate of false failure detections of processes, or the time to detect a failure. [12] identifies the quadratic increase in the message load imposed by such membership protocols as another symptom of the unscalability of traditional protocols for membersh ...
... these group sizes is an increase in either the rate of false failure detections of processes, or the time to detect a failure. [12] identifies the quadratic increase in the message load imposed by such membership protocols as another symptom of the unscalability of traditional protocols for membersh ...
3rd Edition, Chapter 5
... The probability of no collision is probability of no event in the vulnerability period = 2T Let T = 1 (i.e., our time is measured in packet transmission times, not seconds) Then what is ? = average number of transmission attempts per transmission time. ...
... The probability of no collision is probability of no event in the vulnerability period = 2T Let T = 1 (i.e., our time is measured in packet transmission times, not seconds) Then what is ? = average number of transmission attempts per transmission time. ...
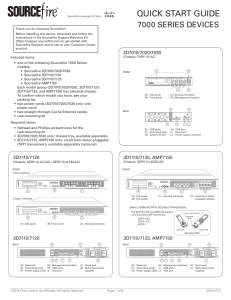
http://www.cisco.com/c/dam/en/us/td/docs/security/sourcefire/3d-system/53/quick-start-guides/QSG-3D7xxx-v53-3-20140311.pdf
... Deploying the Device Your device is typically deployed inside a firewall, where it is connected to your trusted management network and the various network segments you want to monitor. In a simple deployment scenario, you connect the management interface on your device to your trusted management net ...
... Deploying the Device Your device is typically deployed inside a firewall, where it is connected to your trusted management network and the various network segments you want to monitor. In a simple deployment scenario, you connect the management interface on your device to your trusted management net ...
PRO-2014-0192-uPnP_cloud_update - FTP
... description document (DDD) than can be retrieved by means of HTTP. The device description contains information about the device and the implemented services in the device. The service description location can be derived from the information in the device description and can also be retrieved by mean ...
... description document (DDD) than can be retrieved by means of HTTP. The device description contains information about the device and the implemented services in the device. The service description location can be derived from the information in the device description and can also be retrieved by mean ...
User Manual
... ELPRO products are designed to be used in industrial environments by experienced industrial engineering personnel with adequate knowledge of safety design considerations. ELPRO radio products are used on unprotected license-free radio bands with radio noise and interference. The products are designe ...
... ELPRO products are designed to be used in industrial environments by experienced industrial engineering personnel with adequate knowledge of safety design considerations. ELPRO radio products are used on unprotected license-free radio bands with radio noise and interference. The products are designe ...
NETWORK MANAGEMENT
... should be generated under network manager control. To limit access to accounting information, the accounting facility must provide the capability to verify users’ authorization to access and manipulate that information. ...
... should be generated under network manager control. To limit access to accounting information, the accounting facility must provide the capability to verify users’ authorization to access and manipulate that information. ...
P2P final
... “Pong” back to the pinging user to acknowledge that they have received this message. ...
... “Pong” back to the pinging user to acknowledge that they have received this message. ...
TPOT: Translucent Proxying of TCP
... further. The interested reader is directed to [4] and [27] for such a discussion. Note that an alternative approach is to multiplex several TCP connections onto a single TCP connection. This is generally more complex as it requires the demarcation of the multiple data-streams, so that they may be se ...
... further. The interested reader is directed to [4] and [27] for such a discussion. Note that an alternative approach is to multiplex several TCP connections onto a single TCP connection. This is generally more complex as it requires the demarcation of the multiple data-streams, so that they may be se ...
PDF - International Journal of Recent Scientific Research
... Line-of-Sight (NLOS) typically up to 6 - 10 km (4 - 6 miles) for fixed customer premises equipment (CPE). It is based on IEEE 802.16 standard and also called Broadband Wireless Access [8]. ...
... Line-of-Sight (NLOS) typically up to 6 - 10 km (4 - 6 miles) for fixed customer premises equipment (CPE). It is based on IEEE 802.16 standard and also called Broadband Wireless Access [8]. ...
STA-UI-A0037s (BlueW_2310 USB version) User`s Manual
... A Peer-to-Peer Network consists of two or more notebook or desktop computers with Wireless USB Dongles that communicate directly to each other without the use of an Access Point. Such networks are usually small but they can be very useful. Co-workers can quickly set up a Peer-to-Peer group in a temp ...
... A Peer-to-Peer Network consists of two or more notebook or desktop computers with Wireless USB Dongles that communicate directly to each other without the use of an Access Point. Such networks are usually small but they can be very useful. Co-workers can quickly set up a Peer-to-Peer group in a temp ...
1. Introduction - Revistas Universidad Distrital Francisco José de
... The next generation optical access networks were known as G-PON, the G-PON standardization was made in 2001-2004 over ITU-T recommendation G.984.x (G.984.1-G.984.7) and worldwide deployments started in 2010. IEEE also standardizes G-PON, which is included in the IEEE 802.3ah standard called 1 Gb/s E ...
... The next generation optical access networks were known as G-PON, the G-PON standardization was made in 2001-2004 over ITU-T recommendation G.984.x (G.984.1-G.984.7) and worldwide deployments started in 2010. IEEE also standardizes G-PON, which is included in the IEEE 802.3ah standard called 1 Gb/s E ...
UDP Lite
... ECN usage (not available in UDP API) scalability in case of client-server based usage TCP-based applications that are used at the same time may work better perhaps smaller loss ratio while maintaining reasonable throughput ...
... ECN usage (not available in UDP API) scalability in case of client-server based usage TCP-based applications that are used at the same time may work better perhaps smaller loss ratio while maintaining reasonable throughput ...
DLB APC v5.95 User’s Guide Revision 1.0 9 October 2014
... In router mode the device will receive internet through WAN port and will share it to the LAN ports that will be separated with a different IP range. The type of connection to the WAN interface can be made by Static IP, DHCP clie ...
... In router mode the device will receive internet through WAN port and will share it to the LAN ports that will be separated with a different IP range. The type of connection to the WAN interface can be made by Static IP, DHCP clie ...
Slide 1
... If a routing update and the interface on which it is received belong to the same major network, the subnet mask of the interface is applied to the network in the routing update. If a routing update and the interface on which it is received belong to different major networks, the classful subnet ...
... If a routing update and the interface on which it is received belong to the same major network, the subnet mask of the interface is applied to the network in the routing update. If a routing update and the interface on which it is received belong to different major networks, the classful subnet ...
COMPLEMENT YOUR BUSINESS SERVICES PORTFOLIO WITH VIRTUALIZED
... own private overlay. This model also provides the ability to position the transport characteristics to match your specific market. For instance, SLA levels on overbooking, traffic engineering and QoS can be placed in between premium VPN offerings and standard and business grade Internet services. P ...
... own private overlay. This model also provides the ability to position the transport characteristics to match your specific market. For instance, SLA levels on overbooking, traffic engineering and QoS can be placed in between premium VPN offerings and standard and business grade Internet services. P ...
5 Configuring Settings on the Cisco Unified Wireless IP Phone 7925G
... The Cisco Unified IP Phones enable DHCP, by default, to automatically assign IP addresses to devices when you connect them to the network. If you do not use DHCP in your network, then you must disable DHCP and manually enter the network configuration information. For more information, see “Interacti ...
... The Cisco Unified IP Phones enable DHCP, by default, to automatically assign IP addresses to devices when you connect them to the network. If you do not use DHCP in your network, then you must disable DHCP and manually enter the network configuration information. For more information, see “Interacti ...
Guide to Network Defense and Countermeasures
... – Functions as electronic “eyes” of an IDPS – Host-based IDPS – IDPS installed on a single host computer has its agent built into the IDPS software – Network-based IDPS – sensor is hardware or software that monitors network traffic in real time – Attacks detected by an IDPS sensor • Single-session a ...
... – Functions as electronic “eyes” of an IDPS – Host-based IDPS – IDPS installed on a single host computer has its agent built into the IDPS software – Network-based IDPS – sensor is hardware or software that monitors network traffic in real time – Attacks detected by an IDPS sensor • Single-session a ...
IP Multimedia Subsystem and Its Future Perspectives
... into Availability Zones, EC2 can complete disaster recovery into the Amazon cloud. However, the accidental failures of the hardware and software could still cause serious influence of large-scale cloud services. Reliability and disaster recovery solutions in cloud computing are two main challenges. ...
... into Availability Zones, EC2 can complete disaster recovery into the Amazon cloud. However, the accidental failures of the hardware and software could still cause serious influence of large-scale cloud services. Reliability and disaster recovery solutions in cloud computing are two main challenges. ...
Firewall and Network Address Translation Feature
... Products and software version that apply to this guide This Guide applies to the AR-Series firewalls running AlliedWare Plus version 5.4.5 or ...
... Products and software version that apply to this guide This Guide applies to the AR-Series firewalls running AlliedWare Plus version 5.4.5 or ...
Ubee DDW365 Advanced Wireless Gateway
... Use only the power cable supplied with the device. Do not attach the power supply cable to building surfaces or floorings. Rest the power cable freely without any obstacles. Do not place heavy items on top of the power cable. Do not abuse, step, or walk on the cable. Do not place heavy objects o ...
... Use only the power cable supplied with the device. Do not attach the power supply cable to building surfaces or floorings. Rest the power cable freely without any obstacles. Do not place heavy items on top of the power cable. Do not abuse, step, or walk on the cable. Do not place heavy objects o ...
Ubee DDW365 Advanced Wireless Gateway
... Use only the power cable supplied with the device. Do not attach the power supply cable to building surfaces or floorings. Rest the power cable freely without any obstacles. Do not place heavy items on top of the power cable. Do not abuse, step, or walk on the cable. Do not place heavy objects o ...
... Use only the power cable supplied with the device. Do not attach the power supply cable to building surfaces or floorings. Rest the power cable freely without any obstacles. Do not place heavy items on top of the power cable. Do not abuse, step, or walk on the cable. Do not place heavy objects o ...
OSI Seven Layers Model Explained with Examples DOCX Format
... TCP/IP protocol model is another popular layer model that describes network standards. For CCNA exam you should be aware about this model as well. This model has same names of layers as OSI reference model has. Don't be confuse with same name, layers at both model have different functionality in eac ...
... TCP/IP protocol model is another popular layer model that describes network standards. For CCNA exam you should be aware about this model as well. This model has same names of layers as OSI reference model has. Don't be confuse with same name, layers at both model have different functionality in eac ...
Networks and Communication
... communication protocols • Each party retains knowledge of the other • Each party retains information about state of the other (vis a vis the protocol itself) • Each party “knows” if connection is broken ...
... communication protocols • Each party retains knowledge of the other • Each party retains information about state of the other (vis a vis the protocol itself) • Each party “knows” if connection is broken ...
DESIGN AND IMPLEMENTATION OF A WIRELESS ZIGBEE MESH NETWORK
... low-cost and low-power. For the XBee RF module, it does not need too much power and it can provide a reliable way to communicate between two or more devices. It interfaces to a host device through a logic-level asynchronous serial port. Through its serial port, the module can communicate with any lo ...
... low-cost and low-power. For the XBee RF module, it does not need too much power and it can provide a reliable way to communicate between two or more devices. It interfaces to a host device through a logic-level asynchronous serial port. Through its serial port, the module can communicate with any lo ...