Mapping of scalable RDMA protocols to ASIC/FPGA
... • Aggregate of all cores is spanning several FPGAs • Intra-device communication is a issue, need to be careful with PCB design. • We are currently trying to accommodate most of the cores in one FPGA. •Most of the cores will be made available free-of-charge to researchers in non-profit or government ...
... • Aggregate of all cores is spanning several FPGAs • Intra-device communication is a issue, need to be careful with PCB design. • We are currently trying to accommodate most of the cores in one FPGA. •Most of the cores will be made available free-of-charge to researchers in non-profit or government ...
William Stallings Data and Computer Communications
... Small chunks (packets) of data at a time Packets passed from node to node between source and destination Used for terminal to computer and computer to computer communications ...
... Small chunks (packets) of data at a time Packets passed from node to node between source and destination Used for terminal to computer and computer to computer communications ...
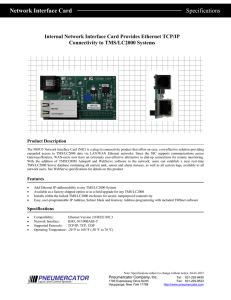
Network Interface Card Specifications
... expanded access to TMS/LC2000 data via LAN/WAN Ethernet networks. Since the NIC supports communications across Gateways/Routers, WAN-users now have an extremely cost-effective alternative to dial-up connections for remote monitoring. With the addition of TMSCOMM Autopoll and WebServe software to the ...
... expanded access to TMS/LC2000 data via LAN/WAN Ethernet networks. Since the NIC supports communications across Gateways/Routers, WAN-users now have an extremely cost-effective alternative to dial-up connections for remote monitoring. With the addition of TMSCOMM Autopoll and WebServe software to the ...
Johns Hopkins University Applied Physics Lab (2008)
... CFDP Performance on MESSENGER What is CFDP? Standardization of communication protocols and ground systems Requirement to downlink science and telemetry data as fast as possible Observed that bitrate can be increased as antenna angle from horizon increases ...
... CFDP Performance on MESSENGER What is CFDP? Standardization of communication protocols and ground systems Requirement to downlink science and telemetry data as fast as possible Observed that bitrate can be increased as antenna angle from horizon increases ...
Review() - Personal.psu.edu
... Scheduled Contacts • If potentially communicating nodes move along predictable paths, they can predict or receive time schedules of their future positions and thereby arrange their future communication sessions • Require time-synchronization ...
... Scheduled Contacts • If potentially communicating nodes move along predictable paths, they can predict or receive time schedules of their future positions and thereby arrange their future communication sessions • Require time-synchronization ...
docx - African Scholar Publications
... model) with appropriate data exchange methods. Underlying these layers are the core networking technologies, consisting of two layers. The internet layer enables computers to identify and locate each other via Internet Protocol (IP) addresses, and allows them to connect to one another via intermedi ...
... model) with appropriate data exchange methods. Underlying these layers are the core networking technologies, consisting of two layers. The internet layer enables computers to identify and locate each other via Internet Protocol (IP) addresses, and allows them to connect to one another via intermedi ...
Chapter 5 : The Internet: Addressing & Services
... addresses without the user or an administrator having to be involved in each configuration change. WINS automatically creates a computer name-IP address mapping entry in a table. When a computer is moved to another geographic location, the new subnet information will be updated automatically in th ...
... addresses without the user or an administrator having to be involved in each configuration change. WINS automatically creates a computer name-IP address mapping entry in a table. When a computer is moved to another geographic location, the new subnet information will be updated automatically in th ...
NETWORK SYSTEMS 2 Learner Guide
... one of the tests written and the corresponding weight used to Page -3- ...
... one of the tests written and the corresponding weight used to Page -3- ...
CSCI6268L10 - Computer Science
... ports – Establish a connection with listen() and connect() • IP and UDP were “stateless” protocols ...
... ports – Establish a connection with listen() and connect() • IP and UDP were “stateless” protocols ...
CSCI6268L10 - Computer Science
... ports – Establish a connection with listen() and connect() • IP and UDP were “stateless” protocols ...
... ports – Establish a connection with listen() and connect() • IP and UDP were “stateless” protocols ...
k - CSE, IIT Bombay
... • psoriasis diagnosed correctly only in 30% of the cases • Psoriasis resembles other diseases within the papulosquamous group of diseases, and is somewhat difficult even for specialists to ...
... • psoriasis diagnosed correctly only in 30% of the cases • Psoriasis resembles other diseases within the papulosquamous group of diseases, and is somewhat difficult even for specialists to ...
2.1 Chapter 2 Network Models
... Moves bit sequence over a physical link. Defines the following: a) Physical characteristics of EIA interfaces and medium. b) Bit representation: encoding/decoding, electrical/optical. c) Data rate: (b/s) bit TX duration. d) Bits synch: sender and receiver clock synch and same data rate. e) Line conf ...
... Moves bit sequence over a physical link. Defines the following: a) Physical characteristics of EIA interfaces and medium. b) Bit representation: encoding/decoding, electrical/optical. c) Data rate: (b/s) bit TX duration. d) Bits synch: sender and receiver clock synch and same data rate. e) Line conf ...
PPT - Graham Klyne
... • Cannot assume simultaneous end-to-end communication • Email-like techniques are being proposed for use over an Inter-Planetary Network (IPN) backbone ...
... • Cannot assume simultaneous end-to-end communication • Email-like techniques are being proposed for use over an Inter-Planetary Network (IPN) backbone ...
Lecture 3: Introduction to net
... Taking roughly 10 minutes to spread worldwide, the worm took down 5 of the 13 DNS root servers along with tens of thousands of other servers, and impacted a multitude of systems ranging from (bank) ATM systems to air traffic control to emergency (911) systems (25 Jan) ...
... Taking roughly 10 minutes to spread worldwide, the worm took down 5 of the 13 DNS root servers along with tens of thousands of other servers, and impacted a multitude of systems ranging from (bank) ATM systems to air traffic control to emergency (911) systems (25 Jan) ...
Lecture 1 - Lane Department of Computer Science and Electrical
... Demand for better networks is dramatically increasingTelecommunications companies are racing to get better computer networking capabilities to home, businesses and communities Has become the political center of attention – with government agencies pushing initiatives to get greater network connectiv ...
... Demand for better networks is dramatically increasingTelecommunications companies are racing to get better computer networking capabilities to home, businesses and communities Has become the political center of attention – with government agencies pushing initiatives to get greater network connectiv ...
CS335 Networking & Network Administration
... routing table to forward packets. IP is an example of a routed protocol. Routing protocols Support a routed protocol by providing mechanisms for sharing routing information. Routing protocol messages move between routers to update and maintain tables. TCP/IP examples are: ...
... routing table to forward packets. IP is an example of a routed protocol. Routing protocols Support a routed protocol by providing mechanisms for sharing routing information. Routing protocol messages move between routers to update and maintain tables. TCP/IP examples are: ...
CSC 335 Data Communications and Networking I
... connection-oriented transport layer services. • OSI transport layer protocol is a generic redesign of transport layer protocol which includes more functions than TCP. ...
... connection-oriented transport layer services. • OSI transport layer protocol is a generic redesign of transport layer protocol which includes more functions than TCP. ...
Chapter 4 Review Questions
... 23. In a group-shared tree, all senders send their multicast traffic using the same routing tree. With source-based tree, the multicast datagrams from a given source are routed over s specific routing tree constructed for that source; thus each source may have a different source-based tree and a rou ...
... 23. In a group-shared tree, all senders send their multicast traffic using the same routing tree. With source-based tree, the multicast datagrams from a given source are routed over s specific routing tree constructed for that source; thus each source may have a different source-based tree and a rou ...
Document
... An Internetwork is the connection of two or more distinct computer networks or network segments via a common routing technology. ...
... An Internetwork is the connection of two or more distinct computer networks or network segments via a common routing technology. ...
The Infrastructure Technologies
... Breaks the message into packets. Ensures error free, end-toend delivery of the complete message. ...
... Breaks the message into packets. Ensures error free, end-toend delivery of the complete message. ...
Powerpoint - Chapter 8
... The TCP/IP protocols were developed to support systems that use any computing platform or operating system. The TCP/IP protocol stack consists of four layers: link, internet, transport, and application. IP uses the ARP protocol to resolve IP addresses into the hardware addresses needed for data-link ...
... The TCP/IP protocols were developed to support systems that use any computing platform or operating system. The TCP/IP protocol stack consists of four layers: link, internet, transport, and application. IP uses the ARP protocol to resolve IP addresses into the hardware addresses needed for data-link ...
Wireless Networks
... mobile end-systems keep their IP address continuation of communication after interruption of link point of connection to the fixed network can be changed ...
... mobile end-systems keep their IP address continuation of communication after interruption of link point of connection to the fixed network can be changed ...
Presentation11-Internet-Protocol_www
... Once an IP address of a textual address is found, the involved servers in the lookup process will keep this information in their cache so a next request is ...
... Once an IP address of a textual address is found, the involved servers in the lookup process will keep this information in their cache so a next request is ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.