Chapter 4 slides - Uppsala University
... the potential range for such metrics as bandwidth, throughput, delay, and reliability can be large ...
... the potential range for such metrics as bandwidth, throughput, delay, and reliability can be large ...
RIP
... the potential range for such metrics as bandwidth, throughput, delay, and reliability can be large ...
... the potential range for such metrics as bandwidth, throughput, delay, and reliability can be large ...
Security_Networking
... o No assurance that packets arrive o No assurance packets are in order, and so on ...
... o No assurance that packets arrive o No assurance packets are in order, and so on ...
Presentation - ece.virginia.edu
... IntServ, DiffServ, TCP switching, etc. Implemented at IP routers instead of end hosts. Not scalable, especially when traffic is large. ...
... IntServ, DiffServ, TCP switching, etc. Implemented at IP routers instead of end hosts. Not scalable, especially when traffic is large. ...
Slide 1
... IntServ, DiffServ, TCP switching, etc. Implemented at IP routers instead of end hosts. Not scalable, especially when traffic is large. ...
... IntServ, DiffServ, TCP switching, etc. Implemented at IP routers instead of end hosts. Not scalable, especially when traffic is large. ...
bryan-vsgc06
... • Image two phones not being able to talk to each other… • Main groups for telephony are IETF and ITU – IETF defines VoIP standard SIP – We have been chairing IETF efforts to standardized P2PSIP – Looks liklely to become a standard in the next 1-2 years ...
... • Image two phones not being able to talk to each other… • Main groups for telephony are IETF and ITU – IETF defines VoIP standard SIP – We have been chairing IETF efforts to standardized P2PSIP – Looks liklely to become a standard in the next 1-2 years ...
Securing Network
... Internal Users are usually far more dangerous Normal employees have tools, experience, and know your systems – after all they use them Customers usually take little internal protection precautions – preferring to focus on external Firewalls, and DMZ scenarios for security Data is now being hacked – ...
... Internal Users are usually far more dangerous Normal employees have tools, experience, and know your systems – after all they use them Customers usually take little internal protection precautions – preferring to focus on external Firewalls, and DMZ scenarios for security Data is now being hacked – ...
File
... • The TCP/IP provided a choice (TCP or UDP) to the customers. • TCP/IP describes an existing set of protocols The OSI model was more general ...
... • The TCP/IP provided a choice (TCP or UDP) to the customers. • TCP/IP describes an existing set of protocols The OSI model was more general ...
ppt
... • Programming network applications requires knowledge of the protocol and the communication layers. From the perspective of applications networking is a service that allows an application to send and receive data from other computers. • PCs connected to the network have unique addresses/names known ...
... • Programming network applications requires knowledge of the protocol and the communication layers. From the perspective of applications networking is a service that allows an application to send and receive data from other computers. • PCs connected to the network have unique addresses/names known ...
Network-on-FPGA
... C communications library Advantages of Message Passing • Directly supported by hardware Small code base (meets memory constraints) Easy to implement (meets time constraints) ...
... C communications library Advantages of Message Passing • Directly supported by hardware Small code base (meets memory constraints) Easy to implement (meets time constraints) ...
lecture 17
... a server Server - A computer that is dedicated to providing information in response to external requests • Client/server network - Model for applications in which the bulk of the back-end processing takes place on a server, while the front-end processing is handled by the clients ...
... a server Server - A computer that is dedicated to providing information in response to external requests • Client/server network - Model for applications in which the bulk of the back-end processing takes place on a server, while the front-end processing is handled by the clients ...
ITGS
... – Arranged as a RAID array » Redundant Array of Independent Disks - failover system for hard disks in which multiple hard disks are connected together » the info from one hard disk is mirrored onto another one every time something is saved, so that if a hard disk fails, the computer switches to its ...
... – Arranged as a RAID array » Redundant Array of Independent Disks - failover system for hard disks in which multiple hard disks are connected together » the info from one hard disk is mirrored onto another one every time something is saved, so that if a hard disk fails, the computer switches to its ...
Export to MS Word
... History of the Internet - Timeline When we talk about the Internet, we talk about the World Wide Web from the past four or five years. But, its history goes back a lot further; all the way back to the 1950s and 60s. "Where was I," you ask, "while all this was happening?" Well, it's quite simple real ...
... History of the Internet - Timeline When we talk about the Internet, we talk about the World Wide Web from the past four or five years. But, its history goes back a lot further; all the way back to the 1950s and 60s. "Where was I," you ask, "while all this was happening?" Well, it's quite simple real ...
Communications and Networks
... manages resources such as user accounts for an entire network. – Host—any computer system that can be accessed over a network. – Router —a node that forwards or routes data packets from one network to their destination in another network ...
... manages resources such as user accounts for an entire network. – Host—any computer system that can be accessed over a network. – Router —a node that forwards or routes data packets from one network to their destination in another network ...
for TCP
... – Consequence: Sender must buffer all TPDUs sent – May need to retransmit • Receiver needs to buffer – Out of order TPDUs – Flow control to application(s) (maximize tranmission speed) • Sender TP layer also buffers to even flow from its application(s) (smooth out bursts to match network) • Buffering ...
... – Consequence: Sender must buffer all TPDUs sent – May need to retransmit • Receiver needs to buffer – Out of order TPDUs – Flow control to application(s) (maximize tranmission speed) • Sender TP layer also buffers to even flow from its application(s) (smooth out bursts to match network) • Buffering ...
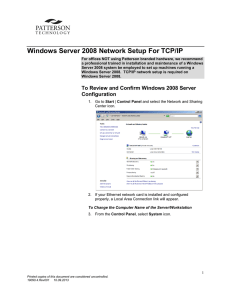
Windows Server 2008 Network Setup For TCP/IP
... Printed copies of this document are considered uncontrolled. 19090.4.Rev001 10.09.2013 ...
... Printed copies of this document are considered uncontrolled. 19090.4.Rev001 10.09.2013 ...
TCP and UDP
... •Processes data for use by applications •Assembles data received by network layer ...
... •Processes data for use by applications •Assembles data received by network layer ...
Here is the Power Point Presentation on Chord
... willy-nilly, using a reference to a node on the network, and having a potentially inefficient topology for searching: ...
... willy-nilly, using a reference to a node on the network, and having a potentially inefficient topology for searching: ...
UNIX for Programmers and Users
... Internet Protocol (IP version 4) addressing is a hardware independent labeling scheme ...
... Internet Protocol (IP version 4) addressing is a hardware independent labeling scheme ...
Lecture 19
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.