Basic Networking, Part TWO
... Not all theses addresses are usable; some are overhead associated with network definitions, and some are reserved The TCP/IP stack converts between the MAC address and the IP address using the Address Resolution Protocol(ARP) for IPv4 or the Neighbor Discovery Protocol(NDP) for IPv6 o These pro ...
... Not all theses addresses are usable; some are overhead associated with network definitions, and some are reserved The TCP/IP stack converts between the MAC address and the IP address using the Address Resolution Protocol(ARP) for IPv4 or the Neighbor Discovery Protocol(NDP) for IPv6 o These pro ...
emulab.net: A Network Emulation and
... Assigns IP addresses and host names Configures VLANs Loads disks, reboots nodes, configures Oss Starts event system, traffic generators, link monitoring/control Yet more odds and ends ... User does his/her experiment ...
... Assigns IP addresses and host names Configures VLANs Loads disks, reboots nodes, configures Oss Starts event system, traffic generators, link monitoring/control Yet more odds and ends ... User does his/her experiment ...
Lecture 6: Intra
... • Represent blocks with a single pair (first network address, count) • Restrict block sizes to powers of 2 - Represent length of network in bits w. slash - E.g.: 128.96.34.0/25 means netmask has 25 1 bits, followed by 7 0 bits, or 0xffffff80 = 255.255.255.128 - E.g.: 128.96.33.0/24 means netmask 255 ...
... • Represent blocks with a single pair (first network address, count) • Restrict block sizes to powers of 2 - Represent length of network in bits w. slash - E.g.: 128.96.34.0/25 means netmask has 25 1 bits, followed by 7 0 bits, or 0xffffff80 = 255.255.255.128 - E.g.: 128.96.33.0/24 means netmask 255 ...
Chapter4_1
... network: between two hosts (may also involve intervening routers in case of VCs) transport: between two processes ...
... network: between two hosts (may also involve intervening routers in case of VCs) transport: between two processes ...
Self-Organizing Hierarchical Neural Network
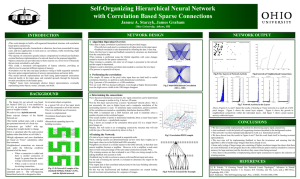
... •This work attempts to build a self-organized hierarchical structure with correlation based sparse connectivity. •Self-organizing networks, hierarchical or otherwise, have been researched for many years, and have applications in such areas as: surveillance, traffic monitoring, flight control, rescue ...
... •This work attempts to build a self-organized hierarchical structure with correlation based sparse connectivity. •Self-organizing networks, hierarchical or otherwise, have been researched for many years, and have applications in such areas as: surveillance, traffic monitoring, flight control, rescue ...
Slide 1
... Socket Address: Socket address is a combination of IP address and port number. In order to provide communication between two different processes ...
... Socket Address: Socket address is a combination of IP address and port number. In order to provide communication between two different processes ...
Automation of Batch Vacuum Pans At D.R.B.C Sugar Factory
... If SH does not receive ACK, it assumes disconnection and changes the window size of the sender to 0 - Choking Maintain TCP end-to-end semantics Packet loss due to error bits is propagated to sender Freeze TCP True end-to-end scheme and does not require the involvement of any intermediaries (such as ...
... If SH does not receive ACK, it assumes disconnection and changes the window size of the sender to 0 - Choking Maintain TCP end-to-end semantics Packet loss due to error bits is propagated to sender Freeze TCP True end-to-end scheme and does not require the involvement of any intermediaries (such as ...
lecture1424803314
... supporting communication among host computers using the Internet protocols. These protocols include the Internet Protocol (IP), the Internet Control Message Protocol (ICMP), the Internet Group Management Protocol (IGMP), and a variety transport and application protocols that depend upon them. All In ...
... supporting communication among host computers using the Internet protocols. These protocols include the Internet Protocol (IP), the Internet Control Message Protocol (ICMP), the Internet Group Management Protocol (IGMP), and a variety transport and application protocols that depend upon them. All In ...
1_Oct16_2015 - users.cs.umn.edu
... Then, its probability of occurring in any one year is 1/100 or 1% – Could happen more than once in 100 years (independent of when last event occurred) ...
... Then, its probability of occurring in any one year is 1/100 or 1% – Could happen more than once in 100 years (independent of when last event occurred) ...
Assignment-3
... Switches can range in price anywhere from $10 for a no-name budget switch to well over $10,000 for a high-end Cisco ...
... Switches can range in price anywhere from $10 for a no-name budget switch to well over $10,000 for a high-end Cisco ...
Chapter 1 Introduction
... 1969, four nodes (universities) connected via IMPs to form a network – Software (NCP) Network Control Protocol provided communication between the hosts. 1972, Vint Cerf and Bob Kahn invented (TCP) Transmission Control Protocol ...
... 1969, four nodes (universities) connected via IMPs to form a network – Software (NCP) Network Control Protocol provided communication between the hosts. 1972, Vint Cerf and Bob Kahn invented (TCP) Transmission Control Protocol ...
networking-1234619450976217-2
... An Internet Protocol (IP) address is a numerical identification (logical address) that is assigned to devices participating in a computer network utilizing the Internet Protocol for communication between its nodes. Although IP addresses are stored as binary numbers, they are often displayed in more ...
... An Internet Protocol (IP) address is a numerical identification (logical address) that is assigned to devices participating in a computer network utilizing the Internet Protocol for communication between its nodes. Although IP addresses are stored as binary numbers, they are often displayed in more ...
Hardened IDS using IXP
... Chris Clark, Jun Li, Chengai Lu, Weidong Shi, Ashley Thomas, Yi Zhang Motivation ...
... Chris Clark, Jun Li, Chengai Lu, Weidong Shi, Ashley Thomas, Yi Zhang Motivation ...
Chapter 9
... 7 if necessary. Beginning with Layer 1, look for simple problems such as power cords plugged in the wall. The most common problems that occur on IP networks result from errors in the addressing scheme. The commands telnet and ping are two important commands that are used for testing a network. ...
... 7 if necessary. Beginning with Layer 1, look for simple problems such as power cords plugged in the wall. The most common problems that occur on IP networks result from errors in the addressing scheme. The commands telnet and ping are two important commands that are used for testing a network. ...
IIUSA – Internet Institute
... Static versus Dynamic Routes • Static routes are established by a network administrator and manually input directly into the routing table • Dynamic routes are learned through the use of a Routing Protocol. Dynamic routes are adaptive. Changes to path availability or establishment of new paths are a ...
... Static versus Dynamic Routes • Static routes are established by a network administrator and manually input directly into the routing table • Dynamic routes are learned through the use of a Routing Protocol. Dynamic routes are adaptive. Changes to path availability or establishment of new paths are a ...
5.3.3.5 Packet Tracer - Configure Layer 3 Switches Instructions IG
... The Network Administrator is replacing the current router and switch with a new Layer 3 switch. As the Network Technician, it is your job to configure the switch and place it into service. You will be working after hours to minimize disruption to the business. Note: This activity begins with a score ...
... The Network Administrator is replacing the current router and switch with a new Layer 3 switch. As the Network Technician, it is your job to configure the switch and place it into service. You will be working after hours to minimize disruption to the business. Note: This activity begins with a score ...
Analysis of a Clock Synchronization Protocol for Wireless Sensor
... in the hand proof. However, there was some places that needed some expansion (1 line of hand proof can be equivalent to 100 lines in Isabelle). These places were the core places explaining some details of the protocol. ...
... in the hand proof. However, there was some places that needed some expansion (1 line of hand proof can be equivalent to 100 lines in Isabelle). These places were the core places explaining some details of the protocol. ...
A Platform For Constructing Virtual Worlds
... are just as important. • Look at the mozart demo, where you would also see the distributed component architecture where new functionality can be added on the fly and make available to all participants in a Mozart instant messenger (ICQ like) Internet service. ...
... are just as important. • Look at the mozart demo, where you would also see the distributed component architecture where new functionality can be added on the fly and make available to all participants in a Mozart instant messenger (ICQ like) Internet service. ...
Network Devices - Eastern Oregon University
... MAC addresses on a given network (not a network segment, but an actual network as defined by its network address) A regular switch forwards all broadcast frames out all ports, but a VLAN switch forwards broadcast frames only to ports that are part of the same VLAN Multiple switches can be part of th ...
... MAC addresses on a given network (not a network segment, but an actual network as defined by its network address) A regular switch forwards all broadcast frames out all ports, but a VLAN switch forwards broadcast frames only to ports that are part of the same VLAN Multiple switches can be part of th ...
Application Control
... Analyses the payload and the header information of an IP packet to detect different kind of intrusion attempts • Monitors inbound traffic • Inspects single packets only, not full stream or TCP/IP sequence • System alerts on 31 malicous packets; most common operating system fingerprinting attempts (n ...
... Analyses the payload and the header information of an IP packet to detect different kind of intrusion attempts • Monitors inbound traffic • Inspects single packets only, not full stream or TCP/IP sequence • System alerts on 31 malicous packets; most common operating system fingerprinting attempts (n ...
Resume - Trelco Limited Company
... Responsible for the technical support of hardware, systems, applications, network administration and configuration of system security for the five regional airport offices of the Department Of Homeland Security in Kansas City. I use advanced diagnostic techniques to identify problems, investigate ca ...
... Responsible for the technical support of hardware, systems, applications, network administration and configuration of system security for the five regional airport offices of the Department Of Homeland Security in Kansas City. I use advanced diagnostic techniques to identify problems, investigate ca ...
Sybex CCNA 640-802 Chapter 1: Internetworking Instructor
... •They don’t forward broadcasts by default. •They can filter the network based on layer 3 (Network layer) information (e.g., IP address). ...
... •They don’t forward broadcasts by default. •They can filter the network based on layer 3 (Network layer) information (e.g., IP address). ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.