Chapter 1. Introduction to Data Communications
... • Sets up virtual circuits for audio-video applications – Real-Time Transport Protocol (RTP) • Used after a virtual connection setup by RSVP or RTSP • Adds a sequence number and a timestamp for helping applications to synchronize delivery • Uses UDP (because of its small header) as transport Copyrig ...
... • Sets up virtual circuits for audio-video applications – Real-Time Transport Protocol (RTP) • Used after a virtual connection setup by RSVP or RTSP • Adds a sequence number and a timestamp for helping applications to synchronize delivery • Uses UDP (because of its small header) as transport Copyrig ...
Introducing Networks
... • The Data Link layer, the second layer of the OSI model, interacts with the networking hardware • The Network layer supports logical addressing and routing of data packets • The Transport layer segments data that is to be sent out on the network into MTUs • The Session layer, the fifth layer, estab ...
... • The Data Link layer, the second layer of the OSI model, interacts with the networking hardware • The Network layer supports logical addressing and routing of data packets • The Transport layer segments data that is to be sent out on the network into MTUs • The Session layer, the fifth layer, estab ...
Dealing with multiple clients
... continuing with 10BASE-T, was designed for point-to-point links only and all termination was built into the device. This changed hubs from a specialist device used at the center of large networks to a device that every twisted pair-based network with more than two machines had to use. The tree struc ...
... continuing with 10BASE-T, was designed for point-to-point links only and all termination was built into the device. This changed hubs from a specialist device used at the center of large networks to a device that every twisted pair-based network with more than two machines had to use. The tree struc ...
in NAT translation table
... • Motivation: local network uses just one IP address as far as outside world is concerned: – no need to be allocated range of addresses from ISP: just one IP address is used for all devices – can change addresses of devices in local network without notifying outside world – can change ISP without ch ...
... • Motivation: local network uses just one IP address as far as outside world is concerned: – no need to be allocated range of addresses from ISP: just one IP address is used for all devices – can change addresses of devices in local network without notifying outside world – can change ISP without ch ...
IETF 82
... • This draft mainly consists of text that was originally part of the MPLS-TP Data Plane Architecture (RFC 5960) and accepted by the WG, but which was taken out for scope reasons • A reserved Ethernet multicast address is allocated and dedicated for MPLS-TP point-to-point links ...
... • This draft mainly consists of text that was originally part of the MPLS-TP Data Plane Architecture (RFC 5960) and accepted by the WG, but which was taken out for scope reasons • A reserved Ethernet multicast address is allocated and dedicated for MPLS-TP point-to-point links ...
[Networking Hardwares]
... • Different computers have different bus architectures; PCI bus master slots are most commonly found on 486/Pentium PCs and ISA expansion slots are commonly found on 386 and older PCs. • NICs come in three basic varieties: 8-bit, 16-bit, and 32-bit. The larger the number of bits that can be transfer ...
... • Different computers have different bus architectures; PCI bus master slots are most commonly found on 486/Pentium PCs and ISA expansion slots are commonly found on 386 and older PCs. • NICs come in three basic varieties: 8-bit, 16-bit, and 32-bit. The larger the number of bits that can be transfer ...
Constrained Application Protocol for Internet of Things
... CoAP is now becoming the standard protocol for IoT applications. Security is important to protect the communication between devices. In the following part, a security protocol DTLS is introduced. Also, one of CoAP application, Smart Homes, is described in this section. There are three main elements ...
... CoAP is now becoming the standard protocol for IoT applications. Security is important to protect the communication between devices. In the following part, a security protocol DTLS is introduced. Also, one of CoAP application, Smart Homes, is described in this section. There are three main elements ...
Concerns in networking
... – Commonly relies on e.g. dynamic service discovery and formation rather than servers ...
... – Commonly relies on e.g. dynamic service discovery and formation rather than servers ...
Services and System Aspects (SA) LTE Africa 11.11.2014
... • Broadcast communications in physical layer (i.e. no feedback loop) and is connectionless • Works in complete absence of infrastructure as well. • The direct user plane communication service for transmission of IP packets is provided by the radio layer • Group security keys are derived from a share ...
... • Broadcast communications in physical layer (i.e. no feedback loop) and is connectionless • Works in complete absence of infrastructure as well. • The direct user plane communication service for transmission of IP packets is provided by the radio layer • Group security keys are derived from a share ...
ppt
... Gain user access to system Gain root access Replace system binaries to set up backdoor Use backdoor for future activities ...
... Gain user access to system Gain root access Replace system binaries to set up backdoor Use backdoor for future activities ...
Nearcast: A Locality-Aware P2P Live Streaming Approach for
... • The topology mismatch problem brings great link stress (unnecessary traffic) in the Internet infrastructure and greatly degrades the system performance. • In this article, we address this problem and propose a localityaware P2P overlay construction method, called Nearcast, which builds an efficien ...
... • The topology mismatch problem brings great link stress (unnecessary traffic) in the Internet infrastructure and greatly degrades the system performance. • In this article, we address this problem and propose a localityaware P2P overlay construction method, called Nearcast, which builds an efficien ...
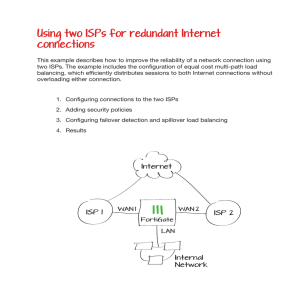
Using two ISPs for redundant Internet connections
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
Chapter 10
... network is dependent on the switch • However, in most large star networks, backup switches are available immediately in case of hardware failure ...
... network is dependent on the switch • However, in most large star networks, backup switches are available immediately in case of hardware failure ...
Dynamic Routing - Department of Computer Technology and
... Is the routing of voice conversations over the Internet or through any other IP-based network. Have some protocols such as VOIP protocols.(Network Voice Protocol) Is economic Essipacially prefered by the companies Protocols carry voice and data Use some devices such as Gateway, IP router ...
... Is the routing of voice conversations over the Internet or through any other IP-based network. Have some protocols such as VOIP protocols.(Network Voice Protocol) Is economic Essipacially prefered by the companies Protocols carry voice and data Use some devices such as Gateway, IP router ...
Figure 3.1 Network types
... Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures ...
... Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures ...
知识管理的IT实现 IBM知识管理解决方案
... (6)Gateway: A gateway can translate information between different network data formats or network architectures. It can translate TCP/IP to AppleTalk so computers supporting TCP/IP can communicate with Apple brand computers. Most gateways operate at the application layer,but can operate at the ne ...
... (6)Gateway: A gateway can translate information between different network data formats or network architectures. It can translate TCP/IP to AppleTalk so computers supporting TCP/IP can communicate with Apple brand computers. Most gateways operate at the application layer,but can operate at the ne ...
IT1402 -MOBILE COMPUTING
... WTP (Transaction) – provides reliable data transfer based on request/reply paradigm • no explicit connection setup or tear down • optimized setup (data carried in first packet of protocol exchange) • seeks to reduce 3-way handshake on initial request – supports • header compression • segmentation /r ...
... WTP (Transaction) – provides reliable data transfer based on request/reply paradigm • no explicit connection setup or tear down • optimized setup (data carried in first packet of protocol exchange) • seeks to reduce 3-way handshake on initial request – supports • header compression • segmentation /r ...
Document
... Separation of control and data transfer plane Flexible network control Centralized QoS management e2e QoS ...
... Separation of control and data transfer plane Flexible network control Centralized QoS management e2e QoS ...
Avici’s Test Program for High Quality/Reliability
... All conditions must be tested because different results can be produced. ...
... All conditions must be tested because different results can be produced. ...
View
... In 1985 the defense withdraw from the network and it became funded by US National Science Foundation. The network was called NSFNET with linked many of the universities, Research labs, Libraries to access their super computers thus establishing the communication. The network grew very rapidly. I ...
... In 1985 the defense withdraw from the network and it became funded by US National Science Foundation. The network was called NSFNET with linked many of the universities, Research labs, Libraries to access their super computers thus establishing the communication. The network grew very rapidly. I ...
Presentation
... IBP: The Internet Backplane Protocol » Storage provisioned on community “depots” » Very primitive service (similar to block service, but more sharable) • Goal is to be a common platform (exposed) • Also part of end-to-end design » Best effort service – no heroic measures • Availability, reliability ...
... IBP: The Internet Backplane Protocol » Storage provisioned on community “depots” » Very primitive service (similar to block service, but more sharable) • Goal is to be a common platform (exposed) • Also part of end-to-end design » Best effort service – no heroic measures • Availability, reliability ...
ARD Presentation
... IP (Internet Protocol ) requires the location of any host connected to the Internet to be uniquely identified by an assigned IP address. This raises one of the most important issues in mobility, because when a host moves to another physical location, it has to change its IP address. However, the hig ...
... IP (Internet Protocol ) requires the location of any host connected to the Internet to be uniquely identified by an assigned IP address. This raises one of the most important issues in mobility, because when a host moves to another physical location, it has to change its IP address. However, the hig ...
Chapter 15 Local Area Network Overview
... loops — Only one path between any two devices — Impossible in standards-based implementation to provide multiple paths through multiple switches between devices • Limits both performance and reliability. ...
... loops — Only one path between any two devices — Impossible in standards-based implementation to provide multiple paths through multiple switches between devices • Limits both performance and reliability. ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.




![[Networking Hardwares]](http://s1.studyres.com/store/data/008735158_1-5386f102645656963f8ccf54c73f2a35-300x300.png)