ppt used in lecture
... • Some QoS approaches are based on the netwrk running largely underloaded • e.g. EF and AF may only work for IP telephony if it constitutes a small part of traffic • This is not the case on many wireless links today. • Need to look at hard QoS schemes - particularly for low latency (e.g. interactive ...
... • Some QoS approaches are based on the netwrk running largely underloaded • e.g. EF and AF may only work for IP telephony if it constitutes a small part of traffic • This is not the case on many wireless links today. • Need to look at hard QoS schemes - particularly for low latency (e.g. interactive ...
Chapter-11 - University of the Western Cape
... from most distance-vector protocols by using topology changes to trigger routing database updates. Examples of hybrid protocols are OSI's IS-IS (Intermediate System-toIntermediate System), and Cisco's EIGRP (Enhanced Interior Gateway Routing ...
... from most distance-vector protocols by using topology changes to trigger routing database updates. Examples of hybrid protocols are OSI's IS-IS (Intermediate System-toIntermediate System), and Cisco's EIGRP (Enhanced Interior Gateway Routing ...
ppt
... • Admission control can only turn away new requests sometimes it may be have been better to terminate an ...
... • Admission control can only turn away new requests sometimes it may be have been better to terminate an ...
Linux+ Guide to Linux Certification
... Enabling development of software and hardware with common interfaces – Making worldwide networks possible; e.g., the Internet ...
... Enabling development of software and hardware with common interfaces – Making worldwide networks possible; e.g., the Internet ...
Introduction
... Suggest a new mobility metric and use it to measure and study characteristics of mobility models and ad hoc networking protocols Study effects of different mobility models on various ad hoc networking protocols, including (but not limited to) ad hoc: unicast routing (e.g., DSR, DSDV, AODV, TOR ...
... Suggest a new mobility metric and use it to measure and study characteristics of mobility models and ad hoc networking protocols Study effects of different mobility models on various ad hoc networking protocols, including (but not limited to) ad hoc: unicast routing (e.g., DSR, DSDV, AODV, TOR ...
Biological Networks Analysis
... A coherent feed-forward loop can act as a circuit that rejects transient activation signals from the general transcription factor and responds only to persistent signals, while allowing for a rapid system shutdown. ...
... A coherent feed-forward loop can act as a circuit that rejects transient activation signals from the general transcription factor and responds only to persistent signals, while allowing for a rapid system shutdown. ...
FMAudit Technical White Paper Product Line Overview
... HIPAA aims to protect all medical records and other individually identifiable health information used or disclosed by a covered entity in any form, whether electronically, on paper, or orally, is covered by the final rule. The FMAudit products are fully compliant with the HIPAA regulations as FMAudi ...
... HIPAA aims to protect all medical records and other individually identifiable health information used or disclosed by a covered entity in any form, whether electronically, on paper, or orally, is covered by the final rule. The FMAudit products are fully compliant with the HIPAA regulations as FMAudi ...
topology discovery in sensor networks
... Randomness in individual node state and network structure. Used for automated information gathering. ...
... Randomness in individual node state and network structure. Used for automated information gathering. ...
Distributed (Operating) Systems -Architectures-
... Outline of Next 3 Lessons • Underlying network layer communication protocols – OSI Model (ISO/OSI) – Internet Protocol Suit TCP/IP ...
... Outline of Next 3 Lessons • Underlying network layer communication protocols – OSI Model (ISO/OSI) – Internet Protocol Suit TCP/IP ...
Introduction to computer networkd #8
... Most of these application processes builds on what it needs and assumes only that an underlying transport mechanism (datagram or connection) will be provided. ...
... Most of these application processes builds on what it needs and assumes only that an underlying transport mechanism (datagram or connection) will be provided. ...
Economics, Policy and a little MPLS
... • Some QoS approaches are based on the netwrk running largely underloaded • e.g. EF and AF may only work for IP telephony if it constitutes a small part of traffic • This is not the case on many wireless links today. • Need to look at hard QoS schemes - particularly for low latency (e.g. interactive ...
... • Some QoS approaches are based on the netwrk running largely underloaded • e.g. EF and AF may only work for IP telephony if it constitutes a small part of traffic • This is not the case on many wireless links today. • Need to look at hard QoS schemes - particularly for low latency (e.g. interactive ...
3B-3 - McGraw Hill Higher Education
... – Also called linear bus – One wire connects all nodes – Terminator ends the wires – Uses a small amount of cable – One broken wire crashes the network ...
... – Also called linear bus – One wire connects all nodes – Terminator ends the wires – Uses a small amount of cable – One broken wire crashes the network ...
The Internet as a Universal Communication Network
... the IEEE INFOCOM 2002, New York, June 2002. F. A. Tobagi, A. P. Markopoulou and M. J. Karam, “Is the Internet Ready for VoIP?” Proceedings of the 2002 Tyrrhenian International Workshop on Digital ...
... the IEEE INFOCOM 2002, New York, June 2002. F. A. Tobagi, A. P. Markopoulou and M. J. Karam, “Is the Internet Ready for VoIP?” Proceedings of the 2002 Tyrrhenian International Workshop on Digital ...
NETWORKING
... A computer network is a telecommunications network that allows computers to exchange data. The physical connection between networked computing devices is ...
... A computer network is a telecommunications network that allows computers to exchange data. The physical connection between networked computing devices is ...
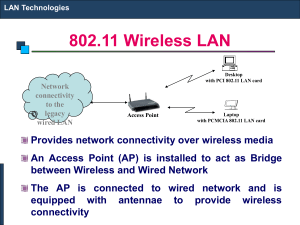
802.11 Wireless LAN
... electrically repeated on all the other ports connected to the same network segment, except for the port on which the data was sent. ...
... electrically repeated on all the other ports connected to the same network segment, except for the port on which the data was sent. ...
CCNA 2.0TM 1.800.865.0165
... and WAN routers and LAN switches. Expert Gary Crothers will show you how to configure a network to increase bandwidth, improve response times, and to enhance reliability and quality of service. At the conclusion of this course, you will solidify your knowledge of Cisco Systems® routing and switching ...
... and WAN routers and LAN switches. Expert Gary Crothers will show you how to configure a network to increase bandwidth, improve response times, and to enhance reliability and quality of service. At the conclusion of this course, you will solidify your knowledge of Cisco Systems® routing and switching ...
Kaleidoscope 2009 - Powerpoint template for paper presentation
... facilitate the communication between two management entities residing either in the same or in different nodes ...
... facilitate the communication between two management entities residing either in the same or in different nodes ...
Reaver
... network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the net ...
... network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the net ...
3rd Edition: Chapter 4 - Georgia Institute of Technology
... It computes a new least cost to x and sends its neighbors its DV. At time t2, y receives z’s update and updates its distance table. y’s least costs do not change and hence y does not send any message to z. ...
... It computes a new least cost to x and sends its neighbors its DV. At time t2, y receives z’s update and updates its distance table. y’s least costs do not change and hence y does not send any message to z. ...
Document
... DCs can be physically replicated Test - 8,000 IP addresses for 34 hours – 47 million packets, 21,000 DNS requests, 150,000 TCP connections – Peak: only 200 requests/sec on DC • Test DC can handle 40x this traffic ...
... DCs can be physically replicated Test - 8,000 IP addresses for 34 hours – 47 million packets, 21,000 DNS requests, 150,000 TCP connections – Peak: only 200 requests/sec on DC • Test DC can handle 40x this traffic ...
Network Topologies
... One node or device can contain multiple radio cards or modules, allowing the nodes to be customized to handle a unique set of functions and frequency bands. ...
... One node or device can contain multiple radio cards or modules, allowing the nodes to be customized to handle a unique set of functions and frequency bands. ...
A Data Dissemination Method for Supporting Mobile Sinks in
... Communication Overhead Analysis TTDD ...
... Communication Overhead Analysis TTDD ...
COMBO Introduction
... Openness and flexibility of COMBO solutions for network operators and service providers COMBO targets an open solution enabling interoperability of different carriers and fair sharing of resources: •Establish performance (e.g. QoS) and traffic management for fair sharing of total available resource ...
... Openness and flexibility of COMBO solutions for network operators and service providers COMBO targets an open solution enabling interoperability of different carriers and fair sharing of resources: •Establish performance (e.g. QoS) and traffic management for fair sharing of total available resource ...
Distributed Embedded Control System using ... Implementing Internet of Things to Driverless Car (Autonomous Vehicle)
... executed in the second segment (dynamic segment). Reducing the jitter can be achieved in the time-triggered processing since it is statically programmed and not by the event of any other time-triggered or non-timetriggered tasks. IV. Internet of things: Since there are several Internet applications ...
... executed in the second segment (dynamic segment). Reducing the jitter can be achieved in the time-triggered processing since it is statically programmed and not by the event of any other time-triggered or non-timetriggered tasks. IV. Internet of things: Since there are several Internet applications ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.