Downlaod File
... A. There are four connection methods for transmission media: 1. Optical fiber: An optical fiber is used for communication in a single direction. STC uses the optical fiber when transmitting telephone. 2. Wired: waves are guided along a solid medium such as a transmission line. STC offered wired serv ...
... A. There are four connection methods for transmission media: 1. Optical fiber: An optical fiber is used for communication in a single direction. STC uses the optical fiber when transmitting telephone. 2. Wired: waves are guided along a solid medium such as a transmission line. STC offered wired serv ...
Shortest Path Bridging IEEE 802.1aq Overview
... devices, head end and/or transit multicast replication , all while supporting the full suit of 802.1 OA&M. Applications consist of STP replacement, Data Center L2 fabric control, L2 Internet Distributed Exchange point fabric control, small to medium ...
... devices, head end and/or transit multicast replication , all while supporting the full suit of 802.1 OA&M. Applications consist of STP replacement, Data Center L2 fabric control, L2 Internet Distributed Exchange point fabric control, small to medium ...
Attention aided perception in sparse-coding networks
... The attention signal is applied on the marker, Natt, of the attended object Catt. ( Catt {C1 , C2 , C3 ...} ). ...
... The attention signal is applied on the marker, Natt, of the attended object Catt. ( Catt {C1 , C2 , C3 ...} ). ...
Electronic Commerce
... A bridge logically separates a single network into two segments This is useful when you have one or more servers (for example) on the network that are heavily used and others that are not ...
... A bridge logically separates a single network into two segments This is useful when you have one or more servers (for example) on the network that are heavily used and others that are not ...
Reconciling Zero-conf with Efficiency in Enterprises
... A switch must handle frames carried in every VLAN the switch is participating in; increasing mobility forces switches to join many, sometimes all, VLANs Forwarding path (i.e., a tree) in each VLAN is still inefficient STP converges slow Trunk configuration overhead increase significantly ...
... A switch must handle frames carried in every VLAN the switch is participating in; increasing mobility forces switches to join many, sometimes all, VLANs Forwarding path (i.e., a tree) in each VLAN is still inefficient STP converges slow Trunk configuration overhead increase significantly ...
OSI Model: Physical Layer Data Link Network
... Connection-Oriented – before data is sent, the service from the sending computer must establish a connection with the receiving computer. Connectionless – data can be sent at any time by the service from the sending computer. ...
... Connection-Oriented – before data is sent, the service from the sending computer must establish a connection with the receiving computer. Connectionless – data can be sent at any time by the service from the sending computer. ...
Wireless Communications and Networks
... between client and gateway are not modified, using message authentication Privacy – ensures that the data cannot be read by a third party, using encryption Authentication – establishes authentication of the two parties, using digital certificates Denial-of-service protection – detects and rejects me ...
... between client and gateway are not modified, using message authentication Privacy – ensures that the data cannot be read by a third party, using encryption Authentication – establishes authentication of the two parties, using digital certificates Denial-of-service protection – detects and rejects me ...
EECC694 - Shaaban
... – Used only when other congestion control methods in place fail. – When capacity is reached, routers or switches may discard a number of incoming packets to reduce their load. EECC694 - Shaaban #4 lec #8 Spring2000 3-30-2000 ...
... – Used only when other congestion control methods in place fail. – When capacity is reached, routers or switches may discard a number of incoming packets to reduce their load. EECC694 - Shaaban #4 lec #8 Spring2000 3-30-2000 ...
The Advanced Internet Project in Costa Rica
... and education networks, such as Geant in Europe and CA3Net in Canada. The pilot project had already functioned flawlessly for almost a year. Moreover, it was demonstrated how the new technologies and concepts could substitute old ones with great advantage. For example commutation within the IP proto ...
... and education networks, such as Geant in Europe and CA3Net in Canada. The pilot project had already functioned flawlessly for almost a year. Moreover, it was demonstrated how the new technologies and concepts could substitute old ones with great advantage. For example commutation within the IP proto ...
Chapter 19. Host-to-Host Delivery: Internetworking
... In IPv4 addressing, a block of addresses can be defined as x.y.z.t /n in which x.y.z.t defines one of the addresses and the /n defines the mask. The first address in the block can be found by setting the rightmost 32 − n bits to 0s The last address in the block can be found by setting the rightmost ...
... In IPv4 addressing, a block of addresses can be defined as x.y.z.t /n in which x.y.z.t defines one of the addresses and the /n defines the mask. The first address in the block can be found by setting the rightmost 32 − n bits to 0s The last address in the block can be found by setting the rightmost ...
Network Security
... Firewall ensures that the internal network and the Internet can both talk to the DMZ, but usually not to each other The DMZ relays services at the application level, e.g. mail forwarding, web proxying The DMZ machines and firewall are centrally administered by people focused on security full-time (i ...
... Firewall ensures that the internal network and the Internet can both talk to the DMZ, but usually not to each other The DMZ relays services at the application level, e.g. mail forwarding, web proxying The DMZ machines and firewall are centrally administered by people focused on security full-time (i ...
Marina Papatriantafilou – Network layer part 2 (Control Plane)
... • instantiation, implementation in the Internet routing protocols – RIP – OSPF – BGP • ICMP (control protocol) ...
... • instantiation, implementation in the Internet routing protocols – RIP – OSPF – BGP • ICMP (control protocol) ...
DK_February_2008_Koblenz - delab-auth
... The cache discovery protocol (2/2) When a mediator receives a request, searches its cache • If it deduces that the request can be satisfied by a neighboring node (remote cache hit), forwards the request to the neighboring node with the largest residual energy • If the request can not be satisfied b ...
... The cache discovery protocol (2/2) When a mediator receives a request, searches its cache • If it deduces that the request can be satisfied by a neighboring node (remote cache hit), forwards the request to the neighboring node with the largest residual energy • If the request can not be satisfied b ...
3rd Edition: Chapter 2
... arbitrary end systems directly communicate peer-peer peers are intermittently connected and change IP addresses ...
... arbitrary end systems directly communicate peer-peer peers are intermittently connected and change IP addresses ...
Teleinformatique
... Interconnection -- Connection-oriented Session protocol: Protocol specification ISO/IEC 8649:1996 Information technology -- Open Systems Interconnection -- Service definition for the Association Control Service Element ISO 8571-2:1988 Information processing systems -- Open Systems Interconnection -- ...
... Interconnection -- Connection-oriented Session protocol: Protocol specification ISO/IEC 8649:1996 Information technology -- Open Systems Interconnection -- Service definition for the Association Control Service Element ISO 8571-2:1988 Information processing systems -- Open Systems Interconnection -- ...
Chapter 1. Introduction to Data Communications
... • Multiprotocol over ATM (MPOA)- LANE extension – Uses IP addresses in addition to MAC addresses • If same subnet, use MAC address; otherwise use IP • ATM backbone operating like a network of brouters Copyright 2005 John Wiley & Sons, Inc ...
... • Multiprotocol over ATM (MPOA)- LANE extension – Uses IP addresses in addition to MAC addresses • If same subnet, use MAC address; otherwise use IP • ATM backbone operating like a network of brouters Copyright 2005 John Wiley & Sons, Inc ...
Interior gateway protocol
... • An IGP (Interior Gateway Protocol) is a protocol for exchanging routing information between gateways (hosts with routers) within an autonomous network (for example, a system of corporate local area networks). • The routing information can then be used by the Internet ...
... • An IGP (Interior Gateway Protocol) is a protocol for exchanging routing information between gateways (hosts with routers) within an autonomous network (for example, a system of corporate local area networks). • The routing information can then be used by the Internet ...
Κατανεμημένα Συστήματα
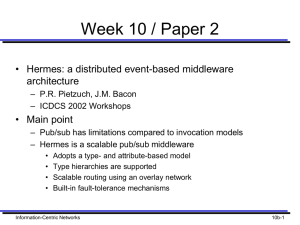
... Introduction • CORBA and Java RMI have proved very useful – Higher-level interface that hides underlying complexity – Invocation model: request/reply client/server – Good for LANs but does not scale ...
... Introduction • CORBA and Java RMI have proved very useful – Higher-level interface that hides underlying complexity – Invocation model: request/reply client/server – Good for LANs but does not scale ...
Document
... Connection-Oriented – before data is sent, the service from the sending computer must establish a connection with the receiving computer. Connectionless – data can be sent at any time by the service from the sending computer. ...
... Connection-Oriented – before data is sent, the service from the sending computer must establish a connection with the receiving computer. Connectionless – data can be sent at any time by the service from the sending computer. ...
Fundamentals of Multimedia, Chapter 15
... • The only thing UDP provides is multiplexing and error detection through a Checksum. ...
... • The only thing UDP provides is multiplexing and error detection through a Checksum. ...
Wireless Local Area Networks
... Network can be established in a new location just by moving the PCs! ...
... Network can be established in a new location just by moving the PCs! ...
... still must cover if forwarded via K. Thus, in such a case, K may decide to drop the packet. The requisite information can be collected from the headers of packets that K overhears as the session goes on. To make it possible, the packet header should carry the current number of hops traveled by the p ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.