SDN security 2 - FSU Computer Science
... • Find the shortest path passing through R4 – Shortest path between S and R4 – Shortest path between R4 and E ...
... • Find the shortest path passing through R4 – Shortest path between S and R4 – Shortest path between R4 and E ...
MPT SP2 v2 - Raven Computers Ltd
... Windows Firewall Reduction of attack surface of a Windows XP computer More secure infrastructure for DCOM Windows Messenger Service is off by default ...
... Windows Firewall Reduction of attack surface of a Windows XP computer More secure infrastructure for DCOM Windows Messenger Service is off by default ...
Q A format
... class of this generalized NUM formulation. As discussed in the answer to the last question, utility functions and constraint sets can be even richer. A deterministic fluid model is used in the above formulations. Stochastic network utility maximization is an active research area, as discussed later ...
... class of this generalized NUM formulation. As discussed in the answer to the last question, utility functions and constraint sets can be even richer. A deterministic fluid model is used in the above formulations. Stochastic network utility maximization is an active research area, as discussed later ...
22-IPv6-BF - EECS People Web Server
... • MT6D is possible because of the large address space allowed in IPv6 can provide and because of stateless address configuration (SLAAC) • Packets are encrypted and tunneled end-to-end so that source and destination address can be changed without breaking the session. ...
... • MT6D is possible because of the large address space allowed in IPv6 can provide and because of stateless address configuration (SLAAC) • Packets are encrypted and tunneled end-to-end so that source and destination address can be changed without breaking the session. ...
Download PDF: Regione Abruzzo - ARIT
... Italy’s Abruzzo region comprises 11,000 square kilometres dominated by the hills and mountains that stretch from the Apennines to the Adriatic Sea. It embraces the highest massifs of Central Italy, with landscapes of rugged beauty and peaks often higher than 2,000 metres. It is a geography that shap ...
... Italy’s Abruzzo region comprises 11,000 square kilometres dominated by the hills and mountains that stretch from the Apennines to the Adriatic Sea. It embraces the highest massifs of Central Italy, with landscapes of rugged beauty and peaks often higher than 2,000 metres. It is a geography that shap ...
Hotspot Shield Vpn Getjar
... Hotspot Shield Vpn Getjar - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, whil ...
... Hotspot Shield Vpn Getjar - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, whil ...
Business 4 Update
... Choice "c" is correct. In public key encryption, a public key is used to encrypt messages. A private key (which is never transmitted) is used to decrypt the message at the other end. There are two keys. Effectively, anyone can encrypt a message, but only the intended recipient can decrypt the messag ...
... Choice "c" is correct. In public key encryption, a public key is used to encrypt messages. A private key (which is never transmitted) is used to decrypt the message at the other end. There are two keys. Effectively, anyone can encrypt a message, but only the intended recipient can decrypt the messag ...
answers - Princeton CS
... QUESTION 3: Going With the Flow (10 points) (3a) A home user upgrades from a dial-up connection to high-speed broadband, but does not see much improvement in Internet performance for visiting a Web site. Give one reason why this might happen, even if the network and the Web server have ample capaci ...
... QUESTION 3: Going With the Flow (10 points) (3a) A home user upgrades from a dial-up connection to high-speed broadband, but does not see much improvement in Internet performance for visiting a Web site. Give one reason why this might happen, even if the network and the Web server have ample capaci ...
IM7200-L Cellular Addendum
... Watchdog “Keep Alive” This watchdog can be used to force a clean restart of the cellular modem and its services to work around any carrier issues (e.g. to prevent your carrier from disconnecting the cellular connection during idle periods). This service periodically pings a nominated IP address. Eac ...
... Watchdog “Keep Alive” This watchdog can be used to force a clean restart of the cellular modem and its services to work around any carrier issues (e.g. to prevent your carrier from disconnecting the cellular connection during idle periods). This service periodically pings a nominated IP address. Eac ...
IE Looks at 192.168.50.10 : 8080
... 2003, Internet Information Services (IIS), Routing and Remote Access, Active Directory directory service, and many other Microsoft applications, servers, and services. ...
... 2003, Internet Information Services (IIS), Routing and Remote Access, Active Directory directory service, and many other Microsoft applications, servers, and services. ...
Ubee DVW32CB
... not be reproduced, distributed, or altered in any fashion by any entity (either internal or external to Ubee), except in accordance with applicable agreements, contracts, or licensing, without the express written consent of Ubee and the business management owner of the material. Ubee Interactive con ...
... not be reproduced, distributed, or altered in any fashion by any entity (either internal or external to Ubee), except in accordance with applicable agreements, contracts, or licensing, without the express written consent of Ubee and the business management owner of the material. Ubee Interactive con ...
Cisco tcs2 - Liberty High School
... secured interconnections between them. Services Exposed to the Internet-Internet Connectivity will utilize a double firewall implementation with all Internet-exposed applications residing on a public backbone network. For security reasons, the only services exposed to the internet will be DNS and em ...
... secured interconnections between them. Services Exposed to the Internet-Internet Connectivity will utilize a double firewall implementation with all Internet-exposed applications residing on a public backbone network. For security reasons, the only services exposed to the internet will be DNS and em ...
class2
... ADSL: asymmetric digital subscriber line Up to 1 Mbps upstream (today typically < 256 kbps) Up to 8 Mbps downstream (today typically < 1 Mbps) FDM on phone line for upstream, downstream and voice shared ...
... ADSL: asymmetric digital subscriber line Up to 1 Mbps upstream (today typically < 256 kbps) Up to 8 Mbps downstream (today typically < 1 Mbps) FDM on phone line for upstream, downstream and voice shared ...
Network Standards and Protocols - Instituto Tecnológico de Morelia
... names, what DNS is to domain names. • The LMHOSTS (LAN Manager Hosts) file is used to enable domain name resolution when other methods, e.g. WINS, fail. The file can be located with the path %systemroot%\system32\drivers\etc\. ...
... names, what DNS is to domain names. • The LMHOSTS (LAN Manager Hosts) file is used to enable domain name resolution when other methods, e.g. WINS, fail. The file can be located with the path %systemroot%\system32\drivers\etc\. ...
4th Edition: Chapter 1 - Simon Fraser University
... institutional link to ISP (Internet) institutional router Ethernet switch ...
... institutional link to ISP (Internet) institutional router Ethernet switch ...
Evolution of Network Services in a Large University an Italian case
... tender action with Telecom Italia and Infostrada – at the time competition was just an absolute novelty for all of us – Telecom Italia was bound by law and by its own monopoly structure not to offer competitive solutions – Infostrada offer was more aggressive although they had no access to the local ...
... tender action with Telecom Italia and Infostrada – at the time competition was just an absolute novelty for all of us – Telecom Italia was bound by law and by its own monopoly structure not to offer competitive solutions – Infostrada offer was more aggressive although they had no access to the local ...
Step 1: Right-Click the My Network Places icon
... How to Setup Dialup Access to Goucher College for Windows 2000 Well you ask, how do I access my personal folders or my Department folders once I’ve connected using Dialup? Well it’s like this: My Network Places shortcuts are best used when you need to access your files stored on Darwin or Magellan ...
... How to Setup Dialup Access to Goucher College for Windows 2000 Well you ask, how do I access my personal folders or my Department folders once I’ve connected using Dialup? Well it’s like this: My Network Places shortcuts are best used when you need to access your files stored on Darwin or Magellan ...
Microsoft Internet Authentication Service
... These requirements will be defined within the CLEO Remote Access Acceptable Use Policy which is to be developed along side this pilot. How to in force such requirements when the PC in question is not on the premises of an institution is an added complication. As part of the pilot, methods for quaran ...
... These requirements will be defined within the CLEO Remote Access Acceptable Use Policy which is to be developed along side this pilot. How to in force such requirements when the PC in question is not on the premises of an institution is an added complication. As part of the pilot, methods for quaran ...
Chapter 10
... • Security for client computers • Security for the communication channels between computers • Security for server computers • Organizations that promote computer, network, and Internet security ...
... • Security for client computers • Security for the communication channels between computers • Security for server computers • Organizations that promote computer, network, and Internet security ...
A Review on Enhancement of Security in IPv6
... carried out with large number of systems attacking a specific martyr. Such as attacking network is called the Botnet. A Botnet is formed by thousands of slave systems usually termed as the Zombies. The attacking systems are much controlled and manipulated by a remote attacker who makes use of these ...
... carried out with large number of systems attacking a specific martyr. Such as attacking network is called the Botnet. A Botnet is formed by thousands of slave systems usually termed as the Zombies. The attacking systems are much controlled and manipulated by a remote attacker who makes use of these ...
Security+ Guide to Network Security Fundamentals
... system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it ...
... system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it ...
S22Kappler
... Number and heterogeneity of networks increases Common interface for data communication (IP) exists But what about control signalling? Networks have different capabilities/resources How to extend the capabilities/resources of networks? Networks are moving How to attach/detach moving net ...
... Number and heterogeneity of networks increases Common interface for data communication (IP) exists But what about control signalling? Networks have different capabilities/resources How to extend the capabilities/resources of networks? Networks are moving How to attach/detach moving net ...
Resource and Admission Control in NGN Ning Li Co-editor of Y.RACF
... ITU-T/ITU-D Workshop "Standardization and Development of Next Generation Networks" Dar es Salaam, 3-5 October 2006 ...
... ITU-T/ITU-D Workshop "Standardization and Development of Next Generation Networks" Dar es Salaam, 3-5 October 2006 ...
NEBULA - A Future Internet That Supports Trustworthy Cloud
... users are located. Third, the architecture must provide a network path between the access and data center over which data can be guaranteed confidentiality and integrity. The data must remain correct and safe in the face of malicious acts as well as equipment errors. Solving all the challenges of th ...
... users are located. Third, the architecture must provide a network path between the access and data center over which data can be guaranteed confidentiality and integrity. The data must remain correct and safe in the face of malicious acts as well as equipment errors. Solving all the challenges of th ...
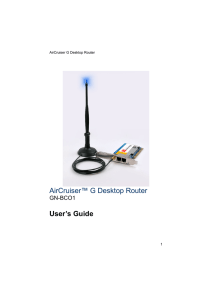
AirCruiser™ G Desktop Router User`s Guide
... Making a Wired Connection Now that you’ve installed the AirCruiser G, like any other router, you’ll need to configure it with your ISP internet connection. This section will help you through the process, which is made easier by SmartSetup 3. The AirCruiser G has one WAN (Internet) port and one LAN ( ...
... Making a Wired Connection Now that you’ve installed the AirCruiser G, like any other router, you’ll need to configure it with your ISP internet connection. This section will help you through the process, which is made easier by SmartSetup 3. The AirCruiser G has one WAN (Internet) port and one LAN ( ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.