MPLS Forum Tutorials - Systems and Computer Engineering
... What is IntServ ? • An architecture allowing the delivery of the required level of QoS to real-time applications ...
... What is IntServ ? • An architecture allowing the delivery of the required level of QoS to real-time applications ...
Guide to TCP/IP, Third Edition
... – Remain important for identifying all servers or services that must be accessible to the Internet ...
... – Remain important for identifying all servers or services that must be accessible to the Internet ...
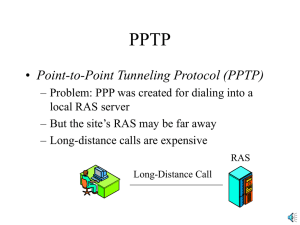
PPTP
... – But the site’s RAS may be far away – Long-distance calls are expensive RAS Long-Distance Call ...
... – But the site’s RAS may be far away – Long-distance calls are expensive RAS Long-Distance Call ...
NetMap: A Novel Framework for Fast Packet I/O
... packet, we have instrumented the sendto() system call in FreeBSD2 so that we can force an early return from the system call at different depths, and estimate the time spent in the various layers of the network stack. Figure 2 shows the results when a test program loops around a sendto() on a bound U ...
... packet, we have instrumented the sendto() system call in FreeBSD2 so that we can force an early return from the system call at different depths, and estimate the time spent in the various layers of the network stack. Figure 2 shows the results when a test program loops around a sendto() on a bound U ...
Expanded Notes: DHCP in the Network
... Administrator reserves specific IP addresses to be handed out to specific MAC addresses, so that certain devices always have the same IP address. Allows for these addresses to be changed from a central location instead of having to log in to each device separately. ...
... Administrator reserves specific IP addresses to be handed out to specific MAC addresses, so that certain devices always have the same IP address. Allows for these addresses to be changed from a central location instead of having to log in to each device separately. ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) ISSN: , PP: 39-43 www.iosrjournals.org
... providers attempt to deliver Ethernet services to multiple end users over a shared network infrastructure. Issues arise because enterprises need to retain control over their own VLAN administration (such as assigning Q-tags to VLANs), and over a shared infrastructure the service provider must contro ...
... providers attempt to deliver Ethernet services to multiple end users over a shared network infrastructure. Issues arise because enterprises need to retain control over their own VLAN administration (such as assigning Q-tags to VLANs), and over a shared infrastructure the service provider must contro ...
ppt
... Each network has its own max transfer unit – Ethernet ~ 1400 bytes; FDDI ~ 4500 bytes – P2P ~ 532 bytes; ATM ~ 53 bytes; Aloha ~ 80bytes Path ...
... Each network has its own max transfer unit – Ethernet ~ 1400 bytes; FDDI ~ 4500 bytes – P2P ~ 532 bytes; ATM ~ 53 bytes; Aloha ~ 80bytes Path ...
Discovery_Routing_Switching_Chapter2
... Identify router and switch hardware characteristics and use router CLI configuration and verification commands. Show the Enterprise Network Infrastructure Movie ...
... Identify router and switch hardware characteristics and use router CLI configuration and verification commands. Show the Enterprise Network Infrastructure Movie ...
net - Data Thinker
... subnet portion of address of arbitrary length address format: a.b.c.d/x, where x is # bits in subnet portion of address subnet part ...
... subnet portion of address of arbitrary length address format: a.b.c.d/x, where x is # bits in subnet portion of address subnet part ...
ex2-6 - wmmhicks.com
... You can “subnet the subnets” and have different sizes of subnet. Fit the addressing requirements better into the address space – less space needed. 25-May-17 ...
... You can “subnet the subnets” and have different sizes of subnet. Fit the addressing requirements better into the address space – less space needed. 25-May-17 ...
CCNP4v5.0
... 2. What happens with the IP type of service (ToS) values when the packet is encapsulated for transport through a tunnel? 3. In VPN environments, where can the QoS service policy be applied? ...
... 2. What happens with the IP type of service (ToS) values when the packet is encapsulated for transport through a tunnel? 3. In VPN environments, where can the QoS service policy be applied? ...
Framework Guidelines On Electricity Grid Connections
... The network code(s) shall set out necessary minimum standards and requirements to be followed by DSOs when connecting significant grid users to the distribution network. For DSOs that are defined as significant grid users, the network code(s) shall set out minimum standards and requirements for thei ...
... The network code(s) shall set out necessary minimum standards and requirements to be followed by DSOs when connecting significant grid users to the distribution network. For DSOs that are defined as significant grid users, the network code(s) shall set out minimum standards and requirements for thei ...
DatagramPacket packet
... Unlike TCP streams, which establish a connection, UDP causes fewer overheads. Real-time applications that demand up-tothe-second or better performance may be candidates for UDP, as there are fewer delays due to error checking and flow control of TCP. ...
... Unlike TCP streams, which establish a connection, UDP causes fewer overheads. Real-time applications that demand up-tothe-second or better performance may be candidates for UDP, as there are fewer delays due to error checking and flow control of TCP. ...
ppt - LIFL
... NAT traversal techniques Wide-Area Communication for Grids: An Integrated Solution to Connectivity, Performance and Security ...
... NAT traversal techniques Wide-Area Communication for Grids: An Integrated Solution to Connectivity, Performance and Security ...
ByteMobile T1000 Series Traffic Director Intelligently Steer Traffic and Manage Load
... Intelligently Steer Traffic and Manage Load Scalable performance on demand, to efficiently and cost-effectively add mobile packet core, control plane and data center capacity to meet changing traffic demands across applications and subscribers. The ByteMobile® T1000 Series Traffic Director intellige ...
... Intelligently Steer Traffic and Manage Load Scalable performance on demand, to efficiently and cost-effectively add mobile packet core, control plane and data center capacity to meet changing traffic demands across applications and subscribers. The ByteMobile® T1000 Series Traffic Director intellige ...
IEE1451.5QoS - IEEE-SA
... – Publish subscribe and client server models of IEEE1451 are supported by PAN – PAN allows re-use of commercial ethernet and IP technology – Many commercial HHDs and PCs will support PAN ...
... – Publish subscribe and client server models of IEEE1451 are supported by PAN – PAN allows re-use of commercial ethernet and IP technology – Many commercial HHDs and PCs will support PAN ...
ICT-Mobile Summit Template
... addressing privacy concerns within the federated telecommunications area. In contrast to existing mobile-centric, wireless sensing approaches, such as NORS [5], which usually either are defined for specialized hardware platforms only, or do not have open interfaces, or are only intended to support o ...
... addressing privacy concerns within the federated telecommunications area. In contrast to existing mobile-centric, wireless sensing approaches, such as NORS [5], which usually either are defined for specialized hardware platforms only, or do not have open interfaces, or are only intended to support o ...
3rd Edition: Chapter 4
... requirements “smart” end systems (computers) need for guaranteed can adapt, perform service control, error recovery “dumb” end systems simple inside network, telephones complexity at “edge” complexity inside many link types network different characteristics uniform service diffic ...
... requirements “smart” end systems (computers) need for guaranteed can adapt, perform service control, error recovery “dumb” end systems simple inside network, telephones complexity at “edge” complexity inside many link types network different characteristics uniform service diffic ...
Chap08
... query and update processing on the database server. This is possible through the use of stored procedures, modules of code which implement application logic, which are included on the database server. For example data integrity can be improved as multiple applications access the same stored procedur ...
... query and update processing on the database server. This is possible through the use of stored procedures, modules of code which implement application logic, which are included on the database server. For example data integrity can be improved as multiple applications access the same stored procedur ...
5620 SAM Data Sheet - LightRiver Technologies
... suites can be used to valid that performance requirements and SLAs are met. For ongoing day-to-day operations, network auditing and reporting as well as bulk maintenance changes can also be automated. Scripts can be triggered by events (for example, after the discovery of a network element), schedul ...
... suites can be used to valid that performance requirements and SLAs are met. For ongoing day-to-day operations, network auditing and reporting as well as bulk maintenance changes can also be automated. Scripts can be triggered by events (for example, after the discovery of a network element), schedul ...
Principles of reliable data transfer
... Client wants IP for www.amazon.com; 1st approx: Client queries a root server to find com DNS server Client queries com DNS server to get amazon.com DNS server Client queries amazon.com DNS server to get IP address for www.amazon.com ...
... Client wants IP for www.amazon.com; 1st approx: Client queries a root server to find com DNS server Client queries com DNS server to get amazon.com DNS server Client queries amazon.com DNS server to get IP address for www.amazon.com ...