KMBE - RADProductsOnline, Buy RAD Products Online at Great Prices
... Right, title and interest, all information, copyrights, patents, know-how, trade secrets and other intellectual property or other proprietary rights relating to this manual and to the KMBE and any software components contained therein are proprietary products of RAD protected under international cop ...
... Right, title and interest, all information, copyrights, patents, know-how, trade secrets and other intellectual property or other proprietary rights relating to this manual and to the KMBE and any software components contained therein are proprietary products of RAD protected under international cop ...
CS 352 Internet Technology
... Internet “Hourglass” Architecture • Defined by Internet Engineering Task Force (IETF) • “Hourglass” Design ...
... Internet “Hourglass” Architecture • Defined by Internet Engineering Task Force (IETF) • “Hourglass” Design ...
Chapter_10_Final
... • Used to identify the routers within a given address scope and send traffic to the nearest router, as determined by the local routing protocols. • Can be used to identify a particular set of routers in the enterprise, such as those that provide access to the Internet. • To use anycasts, the routers ...
... • Used to identify the routers within a given address scope and send traffic to the nearest router, as determined by the local routing protocols. • Can be used to identify a particular set of routers in the enterprise, such as those that provide access to the Internet. • To use anycasts, the routers ...
Abstract - Chennaisunday.com
... Techniques developed for fast recovery from single-link failures provide more than one forwarding edge to route a packet to a destination. Whenever the default forwarding edge fails or a packet is received from the node attached to the default forwarding edge for the destination, the packets are rer ...
... Techniques developed for fast recovery from single-link failures provide more than one forwarding edge to route a packet to a destination. Whenever the default forwarding edge fails or a packet is received from the node attached to the default forwarding edge for the destination, the packets are rer ...
COS 420 day 5 and 6
... Motivation: allow IP to operate over the widest possible variety of physical networks ...
... Motivation: allow IP to operate over the widest possible variety of physical networks ...
Networks
... • Split it up into smaller units if need be • Passes these to the network layer • Ensures that the packets all arrive correctly at the destination • Isolates layer 5 from changes in the underlying hardware ...
... • Split it up into smaller units if need be • Passes these to the network layer • Ensures that the packets all arrive correctly at the destination • Isolates layer 5 from changes in the underlying hardware ...
FM-Delta: Fault Management Packet Compression
... A typical implementation (e.g., [8]) uses a hardware engine and an on-chip memory; the engine periodically reads the messages stored in the memory and transmits them to the network. In this case the required memory space for 64k services is 64k × 100B ∼ = 6.4 MB. This is a very significant size for ...
... A typical implementation (e.g., [8]) uses a hardware engine and an on-chip memory; the engine periodically reads the messages stored in the memory and transmits them to the network. In this case the required memory space for 64k services is 64k × 100B ∼ = 6.4 MB. This is a very significant size for ...
Chapter 12 Supporting Network Address Translation (NAT) Lesson
... There are two types of connections to the Internet: routed and translated. When planning for a routed connection, you will need a range of IP addresses from your Internet service provider (ISP) to use on the internal portion of your network, and they will also give you the IP address of the DNS serv ...
... There are two types of connections to the Internet: routed and translated. When planning for a routed connection, you will need a range of IP addresses from your Internet service provider (ISP) to use on the internal portion of your network, and they will also give you the IP address of the DNS serv ...
Document
... Multiplexing, the radio signal is split into multiple, smaller signals These signals are transmitted at the same time, but at different frequencies OFDM operates in the 5 Ghz band, which makes it more resistant to interference than FHSS and DSSS OFDM is used by the 802.11a standard ...
... Multiplexing, the radio signal is split into multiple, smaller signals These signals are transmitted at the same time, but at different frequencies OFDM operates in the 5 Ghz band, which makes it more resistant to interference than FHSS and DSSS OFDM is used by the 802.11a standard ...
Cisco PIX 515E Security Appliance
... Administrators can easily manage large numbers of remote Cisco PIX Security Appliances using CiscoWorks VPN/ Security Management Solution (VMS). This suite consists of numerous modules including Management Center for Firewalls, Auto Update Server Software and Security Monitor. This powerful combina ...
... Administrators can easily manage large numbers of remote Cisco PIX Security Appliances using CiscoWorks VPN/ Security Management Solution (VMS). This suite consists of numerous modules including Management Center for Firewalls, Auto Update Server Software and Security Monitor. This powerful combina ...
miercom cisco uc 500 test
... features enabled and four endpoints was setup and operational in under 15 minutes. There are several visual feedback mechanisms within the application which aid users in configuration. The first area that was configured was the telephony settings. Several of the fields within the dialog boxes were o ...
... features enabled and four endpoints was setup and operational in under 15 minutes. There are several visual feedback mechanisms within the application which aid users in configuration. The first area that was configured was the telephony settings. Several of the fields within the dialog boxes were o ...
Role of Interface Manipulation Style and Scaffolding on
... adjust priority levels or make more informed routing decisions in response to network congestion and changing traffic patterns. SPIN [Heinzelman, 1999 ] makes adaptive decisions to participate in data dissemination based on current energy levels and the cost of communication. In [Woo and Culler 2001 ...
... adjust priority levels or make more informed routing decisions in response to network congestion and changing traffic patterns. SPIN [Heinzelman, 1999 ] makes adaptive decisions to participate in data dissemination based on current energy levels and the cost of communication. In [Woo and Culler 2001 ...
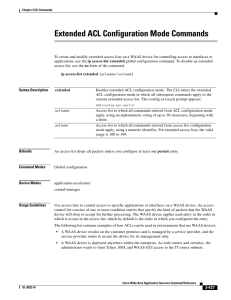
Extended ACL Configuration Mode Commands
... service provider wants to secure the device for its management only. ...
... service provider wants to secure the device for its management only. ...
Middleware and Distributed Systems Peer-to
... • End Game Mode: Last blocks usually come in very slowly • Last requests are sent to all peers in the set P2P | Middleware and Distributed Systems Freitag, 12. Februar 2010 ...
... • End Game Mode: Last blocks usually come in very slowly • Last requests are sent to all peers in the set P2P | Middleware and Distributed Systems Freitag, 12. Februar 2010 ...
TSHOOT Chapter 9 - Faculty Website Directory
... The user (admin1) attempts to obtain an EXEC shell service, which requires authorization. The cmd parameter specifies a command that the user is trying to execute. If * is listed, it refers to plain EXEC access. The method used to authorize this access is TACACS+. The router sends the necess ...
... The user (admin1) attempts to obtain an EXEC shell service, which requires authorization. The cmd parameter specifies a command that the user is trying to execute. If * is listed, it refers to plain EXEC access. The method used to authorize this access is TACACS+. The router sends the necess ...
Middleware and Distributed Systems Peer-to
... • End Game Mode: Last blocks usually come in very slowly • Last requests are sent to all peers in the set P2P | Middleware and Distributed Systems Montag, 30. Januar 12 ...
... • End Game Mode: Last blocks usually come in very slowly • Last requests are sent to all peers in the set P2P | Middleware and Distributed Systems Montag, 30. Januar 12 ...
COMPUTER NETWORKS
... Local Area Network – closed network, serving users of one organisation in a small area (up to several kilometers) connected via telephone, cable, optical or wireless communication lines. Metropolitian Area Network – connecting computer users in a large area (region, city) via various communication ...
... Local Area Network – closed network, serving users of one organisation in a small area (up to several kilometers) connected via telephone, cable, optical or wireless communication lines. Metropolitian Area Network – connecting computer users in a large area (region, city) via various communication ...
PDF
... ABSTRACTTransmission control protocols have been used for data transmission process. TCP has been pre-owned for data transmission over wired communication having different bandwidths and message delays over the network. TCP provides communication using 3-handshake which sends RTS and ACK comes from ...
... ABSTRACTTransmission control protocols have been used for data transmission process. TCP has been pre-owned for data transmission over wired communication having different bandwidths and message delays over the network. TCP provides communication using 3-handshake which sends RTS and ACK comes from ...
Chapter 4
... Offset: byte number of the 1st byte of the fragment (specified in units of 8-byte chunks) ...
... Offset: byte number of the 1st byte of the fragment (specified in units of 8-byte chunks) ...
Unix System Administration
... Port Forwarding Type NAT • port 80 forwarded to port 8080 on server 192.168.1.200 : iptables -t nat -A PREROUTING -p tcp -i eth0 -d $external_ip \ --dport 80 --sport 1024:65535 -j DNAT --to 192.168.1.200:8080 ...
... Port Forwarding Type NAT • port 80 forwarded to port 8080 on server 192.168.1.200 : iptables -t nat -A PREROUTING -p tcp -i eth0 -d $external_ip \ --dport 80 --sport 1024:65535 -j DNAT --to 192.168.1.200:8080 ...
Easyln Products for LonWorks
... The OPC technology presents todays standard for visualization and monitoring systems to access field level data. By this standardized interface SCADA systems communicate with PLCs and field busses, production level data are thus integrated into office applications. Even data exchange with other fie ...
... The OPC technology presents todays standard for visualization and monitoring systems to access field level data. By this standardized interface SCADA systems communicate with PLCs and field busses, production level data are thus integrated into office applications. Even data exchange with other fie ...
“Network” Components
... CPU availability, between the application and the network. However it does require close integration of Object Classes which could cause difficulties. Application Messages (i.e. derivatives of the Amessage class ) would be carried across Boundary B by the link code. Group B : Implement the Network I ...
... CPU availability, between the application and the network. However it does require close integration of Object Classes which could cause difficulties. Application Messages (i.e. derivatives of the Amessage class ) would be carried across Boundary B by the link code. Group B : Implement the Network I ...
Virtual Private Netorks: An Overview
... resources from any public location using the remoteaccess VPN. If a secure VPN runs as part of a trusted VPN, then a hybrid VPN results [1]. C. A very useful classification of VPNs results from its nature, soft or hard. Usually a firewall is used to create and to manage a VPN. This is a hard VPN and ...
... resources from any public location using the remoteaccess VPN. If a secure VPN runs as part of a trusted VPN, then a hybrid VPN results [1]. C. A very useful classification of VPNs results from its nature, soft or hard. Usually a firewall is used to create and to manage a VPN. This is a hard VPN and ...
chap2_2ed_5July02 - National Tsing Hua University
... An Interface by which the network manager may monitor and control the network. The capability of translating the network manager’s requirements into the actual monitoring and control of remote elements in the network. A database of network management information extracted from the database of ...
... An Interface by which the network manager may monitor and control the network. The capability of translating the network manager’s requirements into the actual monitoring and control of remote elements in the network. A database of network management information extracted from the database of ...