OSI Model - DePaul University
... • Your company network has become very slow, so you decide to break it up into multiple domains and use a router to connect the domains. As soon as you disconnect the networks, even with the router running properly, you can’t get data between networks. You are using four Windows NT servers (one in e ...
... • Your company network has become very slow, so you decide to break it up into multiple domains and use a router to connect the domains. As soon as you disconnect the networks, even with the router running properly, you can’t get data between networks. You are using four Windows NT servers (one in e ...
konsep dan komunikasi data dalam wan
... speed grades require optical fiber cables. SONET/SDH is the most popular protocol for data transfer on these backbones. Data that flows over SONET can be in the form of Asynchronous Transfer Mode (ATM) or Packet over SONET (PoS). Packet switching networks define endpoints but not the routes. IP netw ...
... speed grades require optical fiber cables. SONET/SDH is the most popular protocol for data transfer on these backbones. Data that flows over SONET can be in the form of Asynchronous Transfer Mode (ATM) or Packet over SONET (PoS). Packet switching networks define endpoints but not the routes. IP netw ...
Plugging the Leaks Without Unplugging Your Network in the Midst of
... barrier walls that physically enclose networking equipment, but also, networking devices within the facility. This enables unauthorized traffic to enter the network. These realities can cause a network to become vulnerable, from outside or within. Once the intruder is inside, either by physically ac ...
... barrier walls that physically enclose networking equipment, but also, networking devices within the facility. This enables unauthorized traffic to enter the network. These realities can cause a network to become vulnerable, from outside or within. Once the intruder is inside, either by physically ac ...
Reliable network solutions enabling Smart Grid Applications
... • TT/MSR – All time transfer signaling in control plane and un-accessible to users (DoS on the IP trunk level must still be considered) Security issues especially important since much of the driving forces for implementing fiber based time transport instead of using GPS/GLONASS is just – security… © ...
... • TT/MSR – All time transfer signaling in control plane and un-accessible to users (DoS on the IP trunk level must still be considered) Security issues especially important since much of the driving forces for implementing fiber based time transport instead of using GPS/GLONASS is just – security… © ...
Chapter 10 Introduction to MAN and WAN
... Packet-switched network – Network in which all data messages are transmitted using fixed-sized packages, called packets ...
... Packet-switched network – Network in which all data messages are transmitted using fixed-sized packages, called packets ...
Basic Operations of the SIP-Based Mobile Network
... • A SIP-based mobile network architecture to support networking services on the roads – Multiple wireless interfaces – Dynamic bandwidth to internal users – By interpreting SIP signaling, the RM and CAC mechanisms inside the SIP-MNG can guarantee QoS for users – a push mechanism to allow the SIP-MNG ...
... • A SIP-based mobile network architecture to support networking services on the roads – Multiple wireless interfaces – Dynamic bandwidth to internal users – By interpreting SIP signaling, the RM and CAC mechanisms inside the SIP-MNG can guarantee QoS for users – a push mechanism to allow the SIP-MNG ...
J6 Status Slides_1_April
... JTF-7 and 593rd ESC deploy Battle Command Common Server (BCCS) stacks – Leverages Data Integration from various information sources – Integrates all data feeders into ONE common operational picture (CPOF) JTF-7 generates exercise COP & shares IP space with 593rd during JLOTS Creates shared Common Op ...
... JTF-7 and 593rd ESC deploy Battle Command Common Server (BCCS) stacks – Leverages Data Integration from various information sources – Integrates all data feeders into ONE common operational picture (CPOF) JTF-7 generates exercise COP & shares IP space with 593rd during JLOTS Creates shared Common Op ...
Packet switching
... communications, such as twisted pair cables, the signalling used on that equipment, and the lowlevel protocols using that signalling. • Layer 2 - Internet or Internetworking Layer This layer defines IP addresses, with many routing schemes for navigating packets from one IP address to another. • Laye ...
... communications, such as twisted pair cables, the signalling used on that equipment, and the lowlevel protocols using that signalling. • Layer 2 - Internet or Internetworking Layer This layer defines IP addresses, with many routing schemes for navigating packets from one IP address to another. • Laye ...
A3_DistSysCh1 - Computer Science
... data files, web pages, CPU cycles) and the fair sharing of the resources • Economics of sharing expensive resources; e.g. server farms, cloud computing. • Performance enhancement – due to multiple processors; also due to ease of collaboration and info exchange – access to remote services – Groupware ...
... data files, web pages, CPU cycles) and the fair sharing of the resources • Economics of sharing expensive resources; e.g. server farms, cloud computing. • Performance enhancement – due to multiple processors; also due to ease of collaboration and info exchange – access to remote services – Groupware ...
J6 Status Slides_1_April - APAN Community SharePoint
... JTF-7 and 593rd ESC deploy Battle Command Common Server (BCCS) stacks – Leverages Data Integration from various information sources – Integrates all data feeders into ONE common operational picture (CPOF) JTF-7 generates exercise COP & shares IP space with 593rd during JLOTS Creates shared Common Op ...
... JTF-7 and 593rd ESC deploy Battle Command Common Server (BCCS) stacks – Leverages Data Integration from various information sources – Integrates all data feeders into ONE common operational picture (CPOF) JTF-7 generates exercise COP & shares IP space with 593rd during JLOTS Creates shared Common Op ...
Intro To Networking Part B Chapter 3
... Review the on site survey results with the customer to verify that the report accurately describes the current network and any plans for expansion (Let the customer know what you found and what can be accomplished) ...
... Review the on site survey results with the customer to verify that the report accurately describes the current network and any plans for expansion (Let the customer know what you found and what can be accomplished) ...
Adventures in Computer Security - Applied Crypto Group at Stanford
... Firewall • Protect server, not ISP • (More about firewalls next lecture) ...
... Firewall • Protect server, not ISP • (More about firewalls next lecture) ...
WSON Impairment
... network life, e.g., the optical interfaces might be upgraded to higher bit-rates. Such changes could result in paths being unsuitable for the optical signal. Moreover, the optical physical interfaces are typically provisioned at various stages of the network's life span as needed by traffic demands. ...
... network life, e.g., the optical interfaces might be upgraded to higher bit-rates. Such changes could result in paths being unsuitable for the optical signal. Moreover, the optical physical interfaces are typically provisioned at various stages of the network's life span as needed by traffic demands. ...
NETWORK
... environment, Dial up Network to Internet •Development and standardization of Computer Networks: During Initial phase of development each individual networking companies were having there own networking solution. which resulted in no of network island and connecting two different network was a tough ...
... environment, Dial up Network to Internet •Development and standardization of Computer Networks: During Initial phase of development each individual networking companies were having there own networking solution. which resulted in no of network island and connecting two different network was a tough ...
Autonomic Response to Distributed Denial of Service Attacks
... attack path determine the adequate response ...
... attack path determine the adequate response ...
Chapter 12
... – Carrier sense multiple access with collision detection (CSMA/CD) – each node compete with other nodes but differences will be resolved ...
... – Carrier sense multiple access with collision detection (CSMA/CD) – each node compete with other nodes but differences will be resolved ...
A crash course in networking
... • TCP/IP is a suite of international commercial-off-the-shelf protocols – Protocols that require handshaking or a response/replay do not work over long delays and intermittently connected networks – Protocols that require infrastructure may not necessarily be applicable to space unless caching of in ...
... • TCP/IP is a suite of international commercial-off-the-shelf protocols – Protocols that require handshaking or a response/replay do not work over long delays and intermittently connected networks – Protocols that require infrastructure may not necessarily be applicable to space unless caching of in ...
mod_8_study_guide_without_answers
... What is a specialized server that manages all security related aspects of users and network resources called? 8.3 Describe basic networking concepts and technologies 8.3.1 Explain bandwidth and data transmission ...
... What is a specialized server that manages all security related aspects of users and network resources called? 8.3 Describe basic networking concepts and technologies 8.3.1 Explain bandwidth and data transmission ...
HEAT Device Control
... Enabling Productivity and Strong Data Protection Removable devices are valuable productivity tools that facilitate data access and movement for improved collaboration between employees and partners. But the potential impact of data loss and malware introduction – be it accidental or malicious – is a ...
... Enabling Productivity and Strong Data Protection Removable devices are valuable productivity tools that facilitate data access and movement for improved collaboration between employees and partners. But the potential impact of data loss and malware introduction – be it accidental or malicious – is a ...
Computer and Network Security Group
... inside the certificate, in order to keep all data together ...
... inside the certificate, in order to keep all data together ...
In VINI Veritas - Georgia Institute of Technology
... • First experiment: Internet In A Slice – XORP open-source routing protocol suite (NSDI ’05) – Click modular router (TOCS ’00, SOSP ’99) ...
... • First experiment: Internet In A Slice – XORP open-source routing protocol suite (NSDI ’05) – Click modular router (TOCS ’00, SOSP ’99) ...
Binary and Decimal Number Systems What is 101011002 in decimal
... Copyright © 2001, Cisco Systems, Inc. All rights reserved. Printed in USA. Presentation_ID.scr ...
... Copyright © 2001, Cisco Systems, Inc. All rights reserved. Printed in USA. Presentation_ID.scr ...
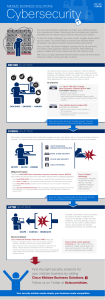
View the graphic
... from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network. To deal with these challenges, you need a smart, scalable threat-centric security model. This model needs to provide cost-effective threat remediation and support sta ...
... from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network. To deal with these challenges, you need a smart, scalable threat-centric security model. This model needs to provide cost-effective threat remediation and support sta ...