New services call for new financial networks TextStart With China`s
... must for the network, as it guarantees delivery of key services over convergent IP network. This is particularly true for real-time services like deposits, videoconferencing, and voice services, which require high-quality bearing resources. Third, as bank outlets are widely distributed, it is gettin ...
... must for the network, as it guarantees delivery of key services over convergent IP network. This is particularly true for real-time services like deposits, videoconferencing, and voice services, which require high-quality bearing resources. Third, as bank outlets are widely distributed, it is gettin ...
Network Topologies
... Only one token is available on the network. When a computer on a network wishes to transmit, it first captures the token; only then can it transmit data. ...
... Only one token is available on the network. When a computer on a network wishes to transmit, it first captures the token; only then can it transmit data. ...
Computer networks Considerations When Choosing a Topology
... transmission media, the most popular being twisted-pair wire, coaxial cable, and the fiber optic cable. With the development of network and communication technology, the inconvenience of wiring is solved with WSN into people’s life; especially it has wide perspective and practicability in the area o ...
... transmission media, the most popular being twisted-pair wire, coaxial cable, and the fiber optic cable. With the development of network and communication technology, the inconvenience of wiring is solved with WSN into people’s life; especially it has wide perspective and practicability in the area o ...
The Internet and Its Uses - Information Systems Technology
... • When establishing a baseline, consider how a network has been designed and what the expected performance for this network should be under normal operating conditions. ...
... • When establishing a baseline, consider how a network has been designed and what the expected performance for this network should be under normal operating conditions. ...
02-evolution2
... DiffServ is stateless (like IP) and scales Service Profiles can be defined by ISP for customers and by transit providers for ISPs DiffServ is very easily deployable and could enable well working VoIP and real-time video Unfortunately, it is not used between operators ...
... DiffServ is stateless (like IP) and scales Service Profiles can be defined by ISP for customers and by transit providers for ISPs DiffServ is very easily deployable and could enable well working VoIP and real-time video Unfortunately, it is not used between operators ...
Workshop 6 Slides - dhdurso.org index to available resources
... Ensures messages delivered in the order in which they were sent. Virtual circuit. A path from A to B is fixed for the duration of one session. Different from A to B may have different paths. Partial remedy to adapting to load changes. Ensures that messages will be delivered in the order in whi ...
... Ensures messages delivered in the order in which they were sent. Virtual circuit. A path from A to B is fixed for the duration of one session. Different from A to B may have different paths. Partial remedy to adapting to load changes. Ensures that messages will be delivered in the order in whi ...
Survey of Active network
... • Reduce network traffic and response time. – where to locate object. – how to forward request between caches. ...
... • Reduce network traffic and response time. – where to locate object. – how to forward request between caches. ...
IAP 01 – Introduction to Internet Architecture
... and its role in Internet architecture. To strengthen the concepts of TCP/IP Protocol Suite. To provide comprehensive knowledge and implementation of routing protocols. To realize the need of Quality of Service based communication and to understand various QoS ...
... and its role in Internet architecture. To strengthen the concepts of TCP/IP Protocol Suite. To provide comprehensive knowledge and implementation of routing protocols. To realize the need of Quality of Service based communication and to understand various QoS ...
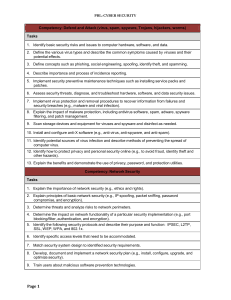
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 18. Manage and distribute critical software updates that resolve known security vulnerabilities and other stability issues. 19. Explain the importance of educating users and supervisors in regard to network security. 20. Implement security controls such as MAC or DAC to ensure user policies are enab ...
... 18. Manage and distribute critical software updates that resolve known security vulnerabilities and other stability issues. 19. Explain the importance of educating users and supervisors in regard to network security. 20. Implement security controls such as MAC or DAC to ensure user policies are enab ...
Penetration Testing Presentation
... • Relying on people not reading the EULAs – the Microsoft PLUS! Scheme. • Kevin Mitnick: The Art of Deception & The Art of Intrusion ...
... • Relying on people not reading the EULAs – the Microsoft PLUS! Scheme. • Kevin Mitnick: The Art of Deception & The Art of Intrusion ...
Grange Insurance Uses NetScout to Provide Continuous Information
... and routers. Data from both these sources can be viewed side-by-side in the nGenius solution for comparison purposes and enterprise-wide visibility, without the necessity of manually correlating data, as is the case with other vendor products, and provides additional data points on application utili ...
... and routers. Data from both these sources can be viewed side-by-side in the nGenius solution for comparison purposes and enterprise-wide visibility, without the necessity of manually correlating data, as is the case with other vendor products, and provides additional data points on application utili ...
PROTECTING AGAINST DDOS WITH F5
... Network reconnaissance likely included timing information on all available links and database queries. ...
... Network reconnaissance likely included timing information on all available links and database queries. ...
Subnetting Cases (presentation)
... for the 199.199.199.0 network with the subnet mask 255.255.255.192 Hosts ...
... for the 199.199.199.0 network with the subnet mask 255.255.255.192 Hosts ...
Internet Backplane Protocol API and Applications
... can scale in terms of – the size of the user community, – the aggregate quantity of storage that can be allocated, and – the breadth of distribution of service nodes across network borders ...
... can scale in terms of – the size of the user community, – the aggregate quantity of storage that can be allocated, and – the breadth of distribution of service nodes across network borders ...
e o t , n
... ignore the potential influence of stream network topology on gene movement. We have developed and applied an agent-based model that tracks the lineage and breeding location of individual fish over time, this simulating the movement of non-native genes among spawning locations within a stream network ...
... ignore the potential influence of stream network topology on gene movement. We have developed and applied an agent-based model that tracks the lineage and breeding location of individual fish over time, this simulating the movement of non-native genes among spawning locations within a stream network ...
MCSE Guide to Designing a Windows 2000 Directory Service
... – Bridge determines the destination and source segments – If the segments are the same, the packet is dropped ("filtered"); if the segments are different, then the packet is "forwarded" to the correct segment. – Additionally, bridges do not forward bad or misaligned packets ...
... – Bridge determines the destination and source segments – If the segments are the same, the packet is dropped ("filtered"); if the segments are different, then the packet is "forwarded" to the correct segment. – Additionally, bridges do not forward bad or misaligned packets ...
Good CV for a Network Engineer
... Senior Cisco/Juniper Network Engineer October 2009 – present Senior level design & project engineer – contract Gather and collate network requirements by working with clients and colleagues. Design secure and scalable networks. Assist in sizing effort for the network part of projects. Assist ...
... Senior Cisco/Juniper Network Engineer October 2009 – present Senior level design & project engineer – contract Gather and collate network requirements by working with clients and colleagues. Design secure and scalable networks. Assist in sizing effort for the network part of projects. Assist ...
Layer cake and an hourglass
... Increased overhead for apps that don’t need functionality Full functionality can be • But, in-network performance may be better ...
... Increased overhead for apps that don’t need functionality Full functionality can be • But, in-network performance may be better ...
UoD_CISCO Networking Academy
... 9.2 Self-Defending Network 9.3 Building a Comprehensive Security Policy ...
... 9.2 Self-Defending Network 9.3 Building a Comprehensive Security Policy ...
shuffling:improving data security in ad hoc networks based
... reveal relationships between nodes or disclose their IP addresses. If a route to a particular node is requested more often than to other nodes, the attacker will be able to expect that the node is important for the network, and disabling it could bring the entire network down. Unlike passive attacks ...
... reveal relationships between nodes or disclose their IP addresses. If a route to a particular node is requested more often than to other nodes, the attacker will be able to expect that the node is important for the network, and disabling it could bring the entire network down. Unlike passive attacks ...
nexosTroubleshooting..
... port, four local area network (LAN) ports, and a wireless network interface. Internally, the WRT54G contains one of several models of the Broadcom BCM 47XX/53XX family of “system-on-a-chip” (“SoC”) platforms, a 200MHz, 32-bit embedded MIPS [23] architecture with 16 MB of RAM, and 4 MB flash ROM. (So ...
... port, four local area network (LAN) ports, and a wireless network interface. Internally, the WRT54G contains one of several models of the Broadcom BCM 47XX/53XX family of “system-on-a-chip” (“SoC”) platforms, a 200MHz, 32-bit embedded MIPS [23] architecture with 16 MB of RAM, and 4 MB flash ROM. (So ...
Network Emulation for Researching Long-Fat
... “We evaluated our Web proxy design with 10 clients on 100Mbit ethernet.” “Simulation results indicate ...” “Memory and CPU demands on the individual nodes were not measured, but we believe will be modest.” “The authors ignore interrupt handling overhead in their evaluation, which likely domi ...
... “We evaluated our Web proxy design with 10 clients on 100Mbit ethernet.” “Simulation results indicate ...” “Memory and CPU demands on the individual nodes were not measured, but we believe will be modest.” “The authors ignore interrupt handling overhead in their evaluation, which likely domi ...
Lecture 3b - Anonymity in networks
... Still need appropriate protocols in case nodes are compromised Still need EMI emission elimination (TEMPEST) ...
... Still need appropriate protocols in case nodes are compromised Still need EMI emission elimination (TEMPEST) ...